The OLOID Blog
Articles and Podcasts on Customer Service, AI and Automation, Product, and more
1.webp)
Featured
What is Cloud Identity and Access Management (IAM)? A Complete Guide
Cloud identity and access management plays a central role in modern cloud security by verifying identities and controlling access across cloud environments. As enterprises adopt more cloud services, a well-designed IAM system enhances security through role-based access control, lifecycle management, and continuous monitoring while closing gaps in identities and access across frontline and shared environments.
.webp)
What is Zero Trust Network Access? A Complete Guide for Modern Enterprises
This guide explains Zero Trust Network Access (ZTNA), why traditional VPN-based security falls short, and how identity-driven access works in modern enterprises. It walks through ZTNA architecture, core principles, deployment models, and real-world use cases. The article highlights how ZTNA limits lateral movement and secures remote, cloud, and shared environments. It also shows how OLOID strengthens Zero Trust in shared workstation scenarios with continuous identity assurance.

SAML vs SSO: Key Differences and How Enterprises Implement Single Sign-On
This article clarifies the distinction between SAML and SSO in modern enterprise identity architecture, explaining how SSO defines the authentication strategy while SAML enables secure identity federation between identity providers and applications. Rather than treating them as competing technologies, it shows how they work together in hybrid environments and where SAML-based SSO remains most effective. It also explores where newer protocols fit and how enterprises design multi-protocol identity frameworks.

SAML Authentication Explained: How It Works, Benefits, and Enterprise Use Cases
SAML remains a backbone for enterprise authentication, enabling secure workforce access and browser-based Single Sign-On across business applications. The article explains how SAML works through Identity Providers, Service Providers, and assertions, showing why organizations still rely on it for stable identity operations. It presents SAML as relevant today, balancing where it performs strongly and where newer identity models may work better. The piece places SAML within the modern identity landscape alongside zero trust, passwordless authentication, and identity orchestration.

Digital Identity Verification: A Complete Guide to Remote Identity Proofing
Digital Identity Verification enables organizations to confirm user identities remotely without physical presence or passwords. Businesses implement this technology to prevent fraud, accelerate onboarding, and meet global KYC/AML compliance requirements. This guide explores verification methods, implementation strategies, real-world applications, and best practices for success. Compliance officers, fintech executives, and security teams gain actionable frameworks for deploying robust identity verification across digital channels.

What is SCIM? The Complete Guide to System for Cross-domain Identity Management
SCIM, or System for Cross-domain Identity Management, is an open standard protocol that automates user provisioning and deprovisioning across cloud applications. This blog explains how SCIM eliminates manual identity management tasks, reduces security risks, and streamlines employee lifecycle workflows. Learn the implementation strategies, real-world use cases, solutions to common challenges, and best practices for deploying SCIM effectively in your organization.

FIDO2 WebAuthn: The Complete Guide to Passwordless Authentication
FIDO2 WebAuthn transforms digital security by eliminating traditional password vulnerabilities. This comprehensive guide explores what FIDO2 and WebAuthn are, how they work together, and why organizations are adopting them. Explore the technical architecture, step-by-step registration and authentication flows, implementation strategies, and real-world use cases.

Federated Identity Management: Complete Guide to Secure Cross-Domain Authentication
Federated Identity Management enables secure authentication across multiple organizations without creating separate accounts for each system. This blog explores how FIM works, key protocols like SAML and OAuth, implementation steps, real-world use cases, and best practices. Learn how enterprises use federation to reduce password fatigue, enhance security, and streamline access across cloud applications and partner ecosystems.

Federated SSO: Enabling Seamless Cross-Organizational Authentication
Federated Single Sign-On (SSO) enables seamless authentication across multiple organizations through trusted identity federation relationships. This comprehensive guide explores the fundamentals of Federated SSO, how it differs from standard SSO, and the protocols that enable cross-domain access. IT administrators, enterprise architects, B2B SaaS companies, and security professionals will find step-by-step implementation guidance, solutions to common challenges, best practices for secure federation, and real-world use cases.

What Is Context-Based Authentication? Benefits, Use Cases & How It Works
Context-based authentication evaluates environmental and behavioral factors before granting system access. Traditional authentication applies identical requirements regardless of access circumstances or risk levels. This guide explains how context-aware authentication works, analyzes signals like location and device health, and enforces dynamic policies. Learn implementation strategies, real-world use cases, and best practices for deploying intelligent authentication.

Fingerprint Authentication Explained: How It Works, Benefits, and Real World Applications
Fingerprint authentication uses unique biological patterns to securely and conveniently verify user identity. This comprehensive guide explores fingerprint scanning, including how it works, different sensor types, implementation strategies, and practical applications. Learn the advantages of biometric verification, common challenges with proven solutions, and best practices for deploying this technology. Whether you're evaluating security options or implementing access systems, this resource provides actionable insights for modern authentication needs.

What is Authentication? Your Complete Guide to Digital Identity Verification
Authentication forms the foundation of digital security by verifying identity before granting system access. This comprehensive guide explains authentication fundamentals, the verification process, and the three primary authentication factors. Readers will discover various authentication methods from passwords to biometrics, understand the critical difference between authentication and authorization, explore real-world use cases, and learn proven security best practices. Whether you're an IT professional, business leader, developer, or general user interested in digital security, this resource provides precise, actionable knowledge for understanding and implementing effective authentication strategies.

Behavioral Biometrics: The Future of Continuous, Passwordless Authentication
Behavioral biometrics represents the future of fraud prevention and continuous authentication technology. This comprehensive guide explores how AI and machine learning analyze unique user behavior patterns to detect fraud, prevent account takeover, and enhance security without adding friction. Learn about behavioral biometrics types, technology fundamentals, real-world applications across industries, implementation best practices, and emerging trends.

What is SSPR: Benefits, Implementation, and Security Considerations
Self-Service Password Reset (SSPR) empowers users to reset passwords and unlock accounts independently without IT helpdesk intervention. This comprehensive implementation guide covers SSPR fundamentals, step-by-step deployment in cloud and hybrid environments, authentication methods, security considerations, and proven strategies to maximize user adoption. Get actionable insights to reduce support costs, enhance productivity, and strengthen security postures.
.webp)
3FA (Three-Factor Authentication): The Ultimate Guide to Maximum Security
Three-Factor Authentication represents the pinnacle of identity verification security in today's threat landscape. This comprehensive guide explores how 3FA combines knowledge factors, possession factors, and biometric factors to protect sensitive data from unauthorized access. Learn the detailed implementation strategies, proven deployment best practices, industry-specific real-world applications, and practical solutions to common challenges.

Time-Based One-Time Password (TOTP): The Complete Guide to Secure Authentication
Time-Based One-Time Password (TOTP) generates temporary authentication codes that expire within 30-60 seconds. Organizations use TOTP to secure access without relying on vulnerable SMS-based verification methods. This guide explains technical implementation, security advantages, and deployment strategies for enterprise environments.

Biometric Spoofing Explained: Risks, Real Attacks and Prevention
Biometric spoofing uses fake fingerprints, facial replicas, or synthetic voice recordings to deceive authentication systems. Attackers exploit weaknesses in biometric sensors and verification algorithms to bypass security without legitimate credentials. This guide explains spoofing techniques, real-world attack examples, and comprehensive defense strategies. Learn about liveness detection technologies, multi-factor authentication approaches, and best practices for preventing biometric authentication compromise across enterprise environments.

Rainbow Table Attacks: What They Are, How They Work, and How to Protect Passwords
Rainbow table attacks use precomputed hash databases to crack passwords rapidly by matching stolen hashes against precalculated values. These lookup tables exploit unsalted password hashes through time-memory tradeoff techniques, avoiding repeated hash calculations. This guide explains how rainbow tables work, why they remain effective, and provides comprehensive defense strategies. You'll discover modern hashing algorithms, salting techniques, and authentication methods that make rainbow table attacks computationally infeasible.

Password Spraying: What It Is, How It Works, and How to Defend Against It
Password spraying is a credential-based attack in which attackers try common passwords across multiple user accounts simultaneously. Unlike brute-force attacks targeting a single account, password spraying distributes attempts to avoid lockout mechanisms. This guide explains how password spraying works, why it succeeds, and provides detection strategies. You'll discover best practices for prevention, including multi-factor authentication, risk-based policies, and passwordless alternatives, eliminating password vulnerabilities.

What Is a Physical Security Key? How It Works, Why It Matters & When to Use It
Physical security keys are hardware devices that provide cryptographic authentication and resist phishing and credential theft attacks. These tamper-resistant tokens use FIDO2 and WebAuthn protocols, replacing passwords with device-bound verification. This blog explains how security keys work, compares types, and provides implementation guidance. Explore use cases, setup procedures, and considerations for deploying hardware authentication across personal and enterprise environments.

Mobile Authentication Explained: Methods, Benefits, and Secure Login Best Practices
Mobile authentication uses smartphones as primary verification devices, replacing traditional password-based login systems. Organizations deploy biometrics, passkeys, push notifications, and device-bound credentials for secure access. This blog explains how mobile authentication works, compares security methods, and provides implementation strategies. Learn the best practices, use case recommendations, and security considerations for deploying mobile-first authentication across enterprise environments.
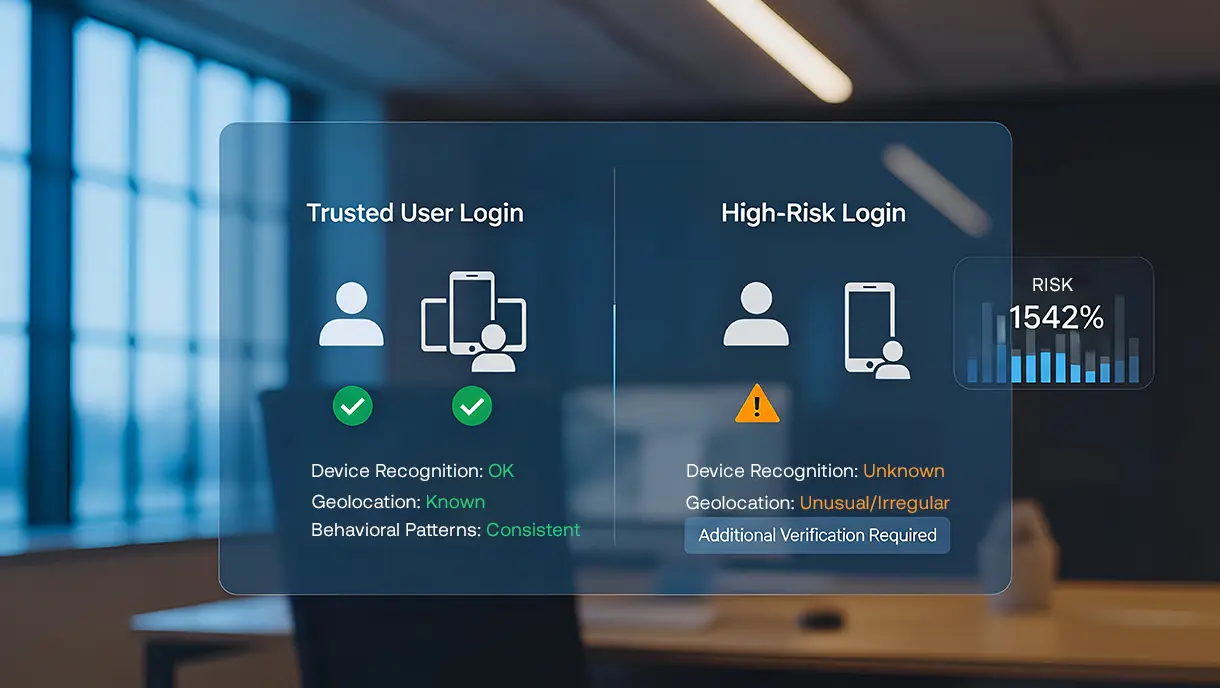
What Is Risk-Based Authentication? Benefits, Use Cases & How It Works
Risk-based authentication evaluates threat indicators and user behavior patterns before enforcing authentication requirements. Traditional static authentication applies the same verification regardless of the actual risk levels. This guide explains how risk-based systems calculate scores, analyze signals, and make dynamic decisions. Learn implementation strategies, regulatory compliance requirements, and best practices for deploying intelligent, risk-aware authentication.

Adaptive Authentication: How Risk-Based Access Transforms Modern Enterprise Security
Adaptive authentication dynamically adjusts security requirements based on real-time risk assessment during login attempts. Traditional authentication applies identical verification for all access scenarios regardless of context. This guide explains how adaptive authentication works, evaluates contextual signals, and enforces appropriate security responses. Learn implementation strategies, common use cases, and best practices for deploying risk-based authentication across enterprise environments.

The Future of Passwords: What Comes Next in Digital Authentication?
Passwords have protected digital accounts for decades, but cannot effectively defend against modern cyber threats. Organizations increasingly adopt passwordless authentication using passkeys, biometrics, and device-based credentials. This guide explores why passwords are becoming obsolete and what technologies replace them. You'll discover authentication trends, implementation challenges, and predictions for how digital identity will evolve.

LDAP vs ADFS: Differences, Use Cases, and How to Choose the Right Approach
LDAP and ADFS represent fundamentally different approaches to enterprise authentication and identity management. LDAP provides directory-based authentication for on-premises systems, while ADFS enables federated identity with single sign-on capabilities. This guide compares architectural differences, protocol support, and use cases for both systems. Learn when each approach fits best and how modern identity platforms bridge traditional and cloud-native authentication requirements.

Strong Authentication: A Comprehensive Guide to Securing Your Digital Identity
Strong authentication provides robust identity verification that resists common attack vectors threatening traditional authentication. Organizations shift from password-based systems to cryptographic methods using multiple verification factors. This guide explains what makes authentication strong, explores modern implementation methods, and provides actionable strategies. Learn about the compliance requirements, implementation challenges, and best practices for deploying strong authentication across enterprise environments.

Credential Rotation: What It Is, Why It Matters, and How to Implement It
Credential rotation systematically replaces passwords, keys, and tokens to limit exposure from compromised credentials. Organizations face growing risks from static credentials that attackers exploit for unauthorized access. This guide explains rotation concepts, benefits, implementation steps, and automation strategies. Learn the best practices for rotating different credential types and building enterprise policies that strengthen security posture.

How to Eliminate Passwords with Passwordless Authentication
Passwords create security vulnerabilities and operational burdens that modern organizations can no longer afford. Passwordless authentication eliminates these risks through biometrics, cryptographic keys, and device-based verification. This blog explores why eliminating passwords matters and how to implement effective alternatives. Learn passwordless authentication methods, implementation strategies, and best practices for transitioning your enterprise to passwordless security.
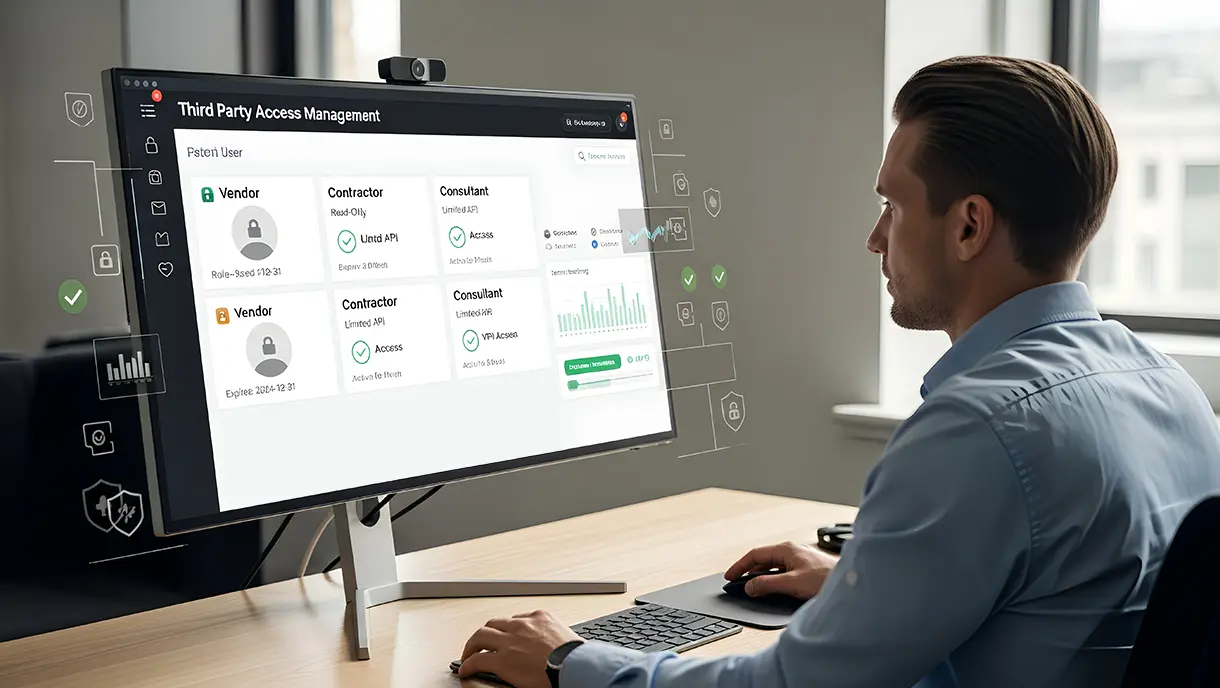
Third-Party Access Management: A Complete Guide to Secure Vendor Access
Third-party access management governs how external vendors, contractors, and partners access internal systems and data. Organizations face growing risks from uncontrolled vendor privileges, making structured access policies essential. This blog covers risk factors, implementation strategies, and security best practices. You'll learn how to balance business needs with robust protection for your critical assets.

2FA Bypass: How Attackers Break Two-Factor Authentication (And How to Prevent It)
Two-factor authentication adds an extra layer of security beyond passwords, but attackers continually develop methods to circumvent these protections. This guide explores standard 2FA bypass techniques, including phishing, SIM swapping, session hijacking, and push notification abuse. Learn why traditional 2FA methods fail and learn modern alternatives and prevention strategies using phishing-resistant authentication, biometrics, and passwordless solutions.

Understanding Authentication Protocols and How They Work
Authentication protocols establish secure communication between users, devices, and applications. These standardized frameworks verify identity before granting access to resources. Organizations use protocols like OAuth, SAML, and Kerberos across different environments. This guide explains how protocols work, their benefits, and practical implementation strategies for enterprises.
Making every day-in-the-life of frontline workers frictionless & secure!
Get the latest updates! Subscribe now!
Thank you! Your submission has been received!
Oops! Something went wrong while submitting the form.



