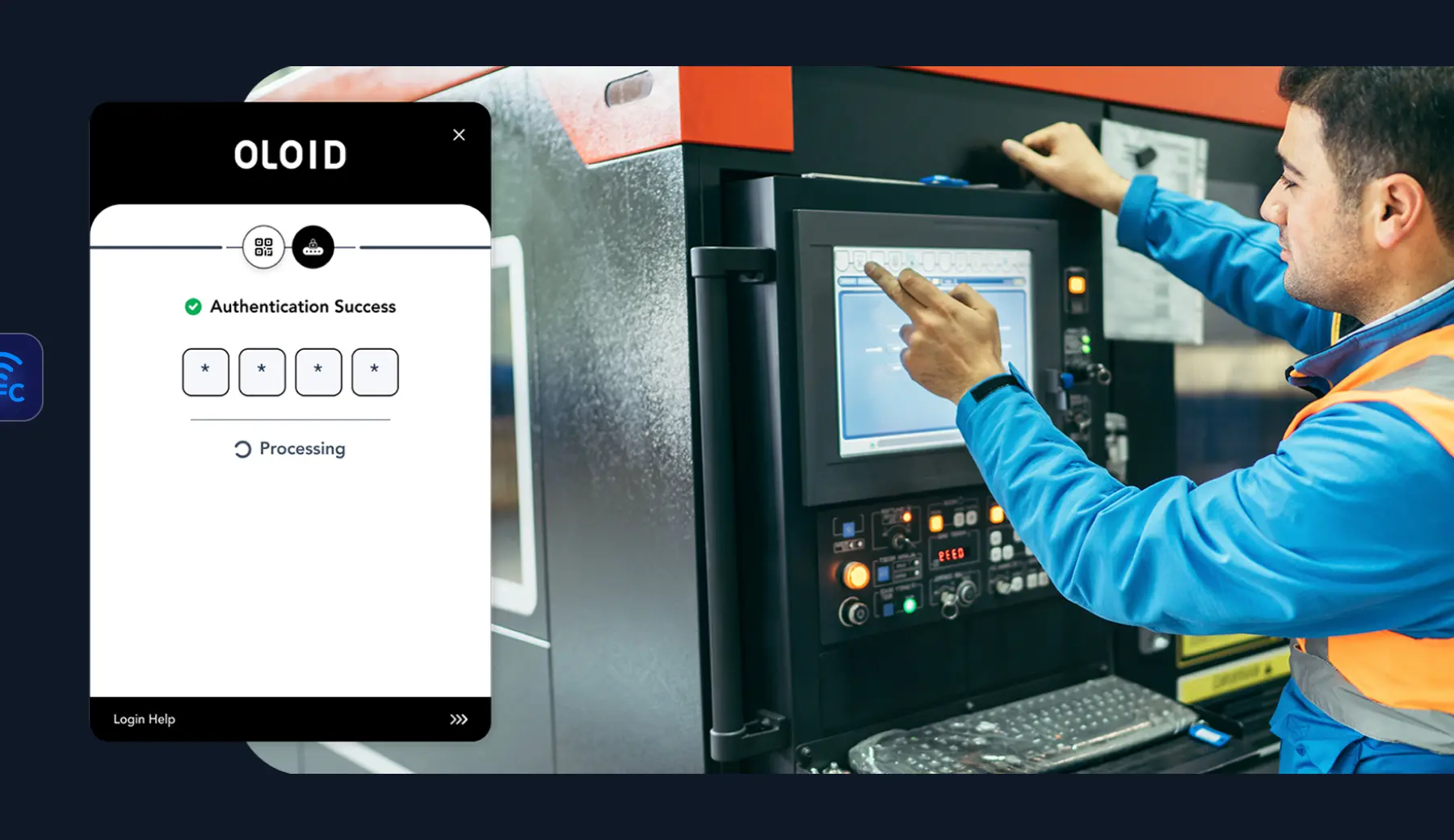
Auditable shared account login
Shared accounts are common in many industries, but they often lack accountability and create security vulnerabilities. Auditable shared account login ensures that every access attempt is tied to an identifiable user, eliminating anonymity while maintaining operational flexibility.

Industry use cases
Effortless, Secure Access for Frontline Workers with SSO
Manufacturing
Track machine or equipment usage by assigning shared credentials to individuals, ensuring compliance and operational safety.

Retail
Allow store associates to access shared POS systems securely, with logs to track individual activities for fraud prevention.

Healthcare
Tie shared EHR system logins to individual staff members, ensuring accountability while maintaining quick access during emergencies.

Pharmaceuticals
Track and attribute individual access to shared systems like laboratory information management systems (LIMS) or production control platforms to ensure accountability and regulatory adherence.

Contact Centers
Identify agents using shared customer management tools, ensuring accountability in handling sensitive data.

Accountability and security for shared credentials





User Attribution Reimagined
Identify the individual accessing a shared account through badge taps, biometrics, or other authentication methods.
- Identify who accessed and when
- Maintain logs of access
- Enable audit capability

Detailed Access Logs
Maintain comprehensive logs of all login attempts, including time, location, and user identity.
- Automate audibale logs
- Set login attempt rules
- Reports include time, location & identity

Integration with IAM Systems
Seamlessly integrate with SSO and directory services to enable secure shared account management.
- Easy integration with SSO
- Enable directory services
- Account management

Granular Role-Based Policies
Control what users can do with shared accounts based on their role or context.
- Meet your RBAC requirements
- Ensure approval flows
- Define account access timeslots
Schedule a demo
Flexible and secure authentication that fits well
Choose amongst many form factors. Allow your staff to unlock any smart device with the same credentials.


“We recognized the tech challenges our frontline workers faced. Partnering with OLOID provided a user-friendly, passwordless solution. Through the OLOID-Okta integration, team members can swiftly access apps, view payroll, change benefits, & access job instructions on tablets.”
Related posts
Securing Shared Devices Without Shared Passwords
Shared devices are vital in frontline work, but shared passwords and legacy MFA can’t meet the demands of shift-based, high-turnover environments. Modern security needs contactless, passwordless solutions that scale, ensuring secure access, individual accountability, and fast ROI.

Shared Devices: How Frontline Workers Use Them to Authenticate
This post explains how frontline workers use shared devices like tablets, kiosks, and computers to access work systems securely. It highlights key authentication methods such as biometrics, smart cards, and role-based access control for convenience and safety. Learn how OLOID’s Passwordless Authenticator simplifies login with facial recognition and MFA, improving compliance and efficiency.

Importance of a Facial Recognition-based Time Clock
Facial recognition time clocks are redefining how organizations manage employee attendance by combining speed, accuracy, and security in a fully touchless process. This blog examines how facial recognition technology operates, its advantages over traditional punch-in systems, and its increasing role in reducing time theft and manual errors. Learn how businesses are adopting AI-powered, contactless attendance systems to streamline workforce management and ensure compliance.
FAQs on auditable shared account login for frontline systems
What is an auditable shared account login?

An auditable shared account login allows multiple users to access a shared system account while ensuring every session is tied to a specific, verified individual. This eliminates anonymous credential sharing and brings accountability and traceability to environments where shared accounts are operationally necessary.
How does OLOID identify individual users on shared accounts?

OLOID uses passwordless authentication factors—such as face recognition, badge scans, NFC, QR codes, or PINs—to verify the individual before granting access to the shared account. Even though the account itself is shared, each login and session is attributed to a specific person.
What information is captured in shared account audit logs?

Access logs capture who accessed the shared account, when the access occurred, and from which device or location. These records are stored in a searchable audit trail that supports security monitoring, forensic investigations, and compliance reporting.
Can auditable shared login integrate with existing SSO, IAM, and role-based policies?

Yes. OLOID integrates with SSO platforms, directory services, and IAM systems to centralize identity attribution and logging. Role-based access policies can be enforced on shared accounts, allowing organizations to define what actions different users can perform and when access is permitted, supporting least-privilege and segregation-of-duties controls.
How does auditable shared login support regulated and high-accountability industries?

Auditable shared login is especially valuable in industries that rely on shared workstations and accounts—such as healthcare, manufacturing, retail, pharmaceuticals, and contact centers—where accountability is critical. By tying every shared account session to an individual, organizations can meet regulatory requirements, strengthen internal controls, and simplify compliance audits.
Making every day-in-the-life of frontline workers frictionless & secure!
Get the latest updates! Subscribe now!
Thank you! Your submission has been received!
Oops! Something went wrong while submitting the form.




