OLOID + Ping Identity
OLOID integrates with Ping Identity to deliver seamless, passwordless multi-factor authentication (MFA) for frontline workers using shared devices. This integration enhances security, reduces login friction, and improves workforce productivity across industries like retail, healthcare, and manufacturing.
Features & benefits
Multiple modes for establishing identity at your workplace Modern physical access for smartphone & non-smartphone users
Secure and Efficient Access with OLOID + Ping Identity
- Passwordless MFA with PingOne for Workforce: OLOID integrates with PingOne for Workforce, enabling phishing-resistant, passwordless MFA across shared and personal devices. Users benefit from fast and secure access without the hassle of passwords.
- Single Sign-On with PingFederate: OLOID works with PingFederate to deliver passwordless Single Sign-On (SSO), allowing workers to authenticate once and access all Ping-connected applications seamlessly.
- Centralized Identity with PingDirectory: OLOID’s integration with PingDirectory ensures centralized, passwordless identity management across all devices and applications, making it easy to apply security policies consistently.

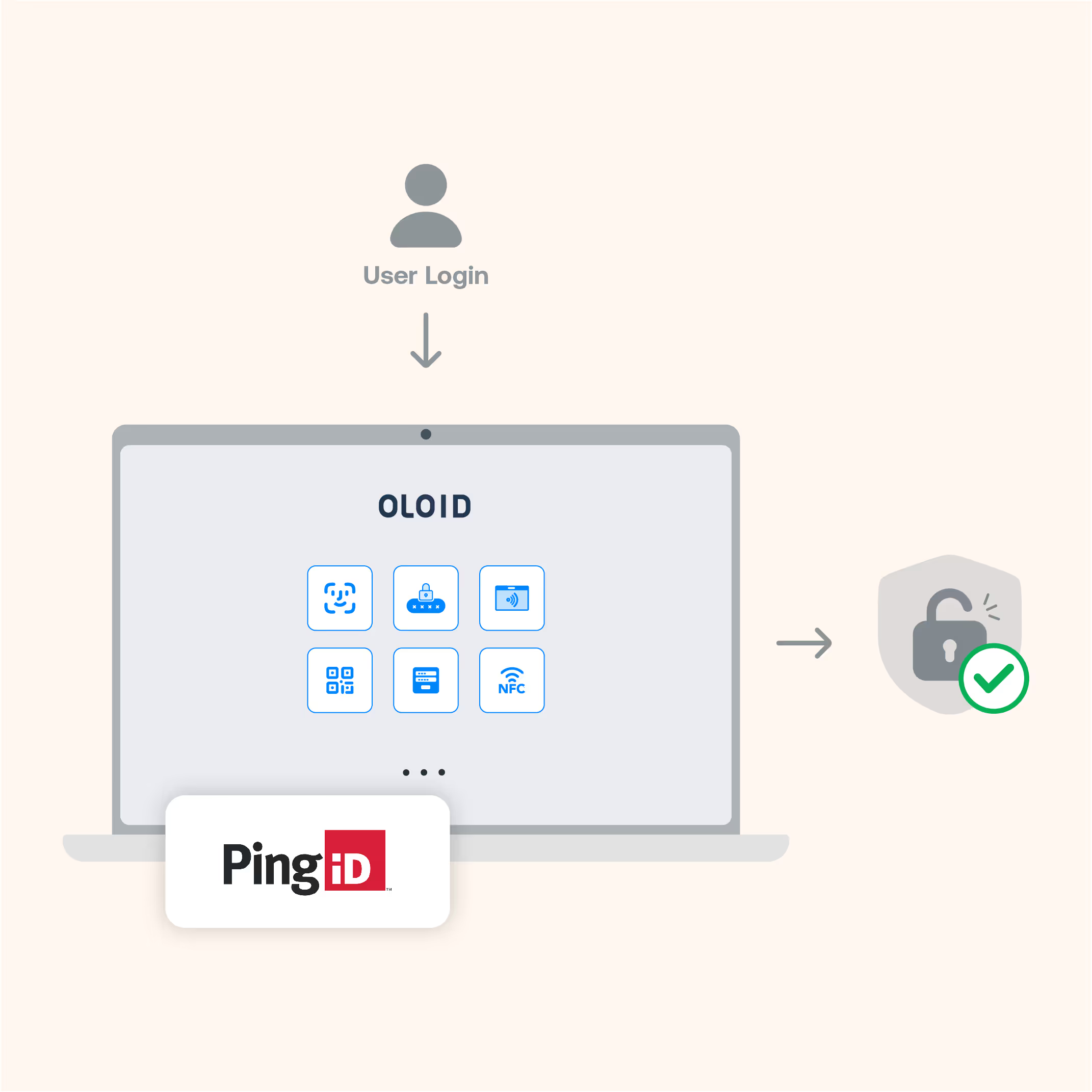
Simplified Security and User Experience
- PingID MFA: Combine OLOID’s passwordless MFA with PingID, offering flexible authentication methods such as biometrics, push notifications, and passkeys, enhancing security for shared devices.
- Cross-Platform Passwordless Login: OLOID extends passwordless login to multiple platforms, enabling secure access to Windows, Android and IOS devices.
- Adaptive Authentication: OLOID enhances Ping’s Adaptive Authentication, dynamically adjusting security based on real-time risk signals like location and behavior, ensuring frictionless access for users while strengthening security.
- Automatic Identity Pass-Through: When users authenticate with OLOID’s passkeys on a desktop, their identity is automatically passed to PingFederate, allowing access to all Ping-connected applications without additional steps unless further verification is needed.
Enhanced Security with OLOID + Ping Identity
- PingAccess Integration: OLOID integrates with PingAccess to provide passwordless, role-based access control for applications and APIs. This ensures that only authorized users can access sensitive resources securely.
- Protection Against Modern Threats: OLOID’s passwordless authentication defends against credential-based attacks, such as phishing and credential stuffing, offering full protection from man-in-the-middle (MitM) and push bombing attacks.

Built for Frontline Workers: OLOID + Ping Identity
- Fast, Touchless Login with PingID: OLOID enables fast, touchless authentication via PingID, using passkeys, biometrics, or mobile devices for seamless login to shared devices.
- Seamless Shift Transitions: OLOID and Ping simplify shift changes by allowing workers to log in and out of shared devices quickly without entering passwords, reducing downtime.
- Unified Access Across IT and OT Systems: OLOID extends Ping’s identity management capabilities to both IT and operational technology (OT) systems, ensuring secure, passwordless access for all roles in your workforce.



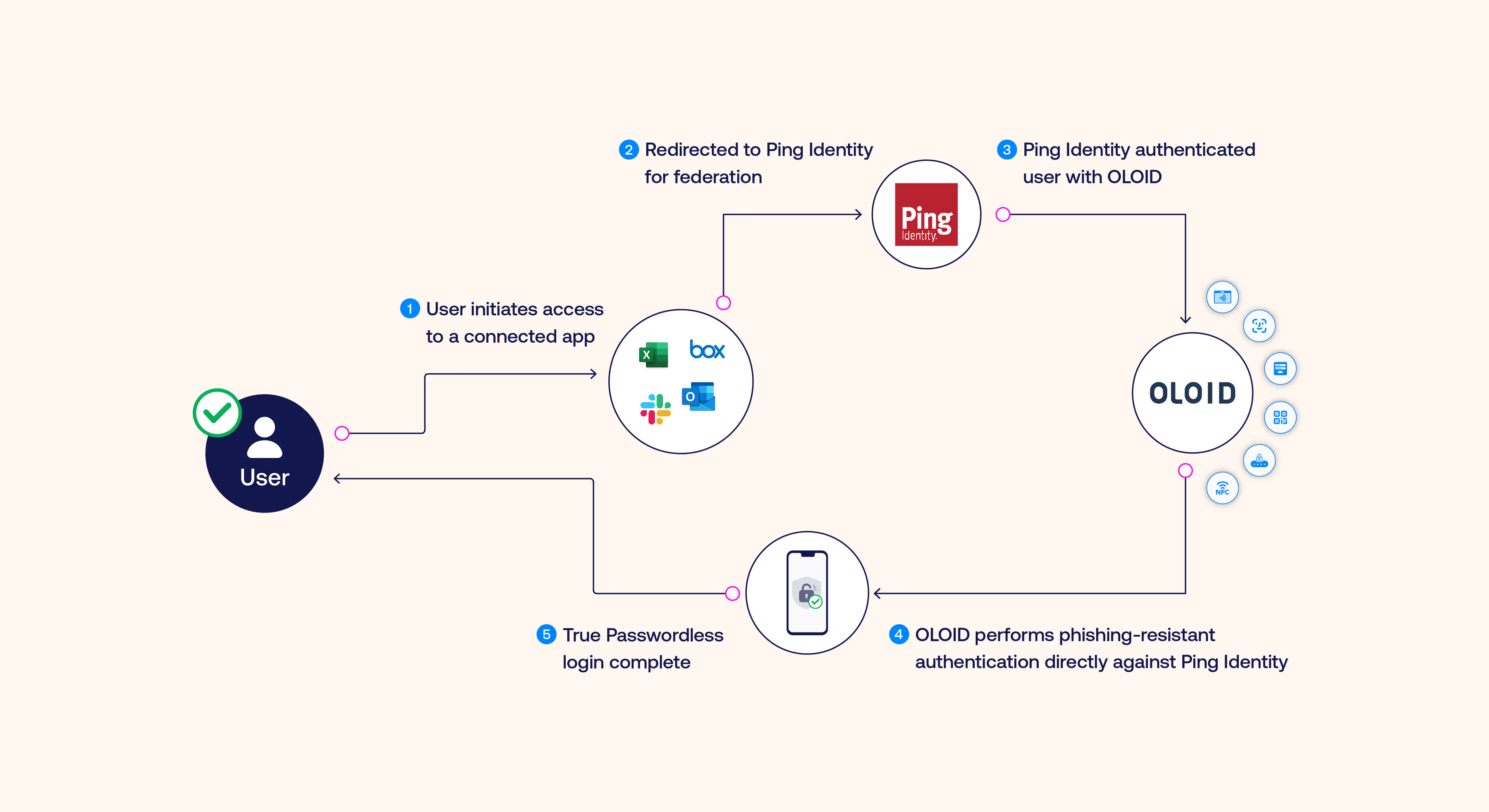
Ping Architecture Diagram
A visual representation of OLOID + PING Architecture
Related posts


Step-By-Step Guide to Seamless MFA Implementation
Effective MFA implementation is crucial for protecting organizations against password breaches and unauthorized access. This blog offers a step-by-step guide to deploying multi-factor authentication, from assessing infrastructure to training users and optimizing performance. Learn about common implementation pitfalls, their solutions, and best practices to simplify multi-factor authentication adoption while strengthening overall security.


How OLOID Secures and Automates Manufacturing Access
The post explains how OLOID secures and automates access in manufacturing environments using modern identity and automation solutions. It highlights features like passwordless authentication, contactless time tracking, and workflow automation. Learn how OLOID boosts safety, efficiency, and compliance for frontline workers.


Biometrics by the Numbers: Trends, Adoption & Challenges
This post explores how biometric technologies are transforming identity verification and data security. It highlights key statistics on adoption, market growth, and consumer trust. Gain insight into privacy, accuracy, and regulatory challenges shaping the future of biometrics.
Making every day-in-the-life of frontline workers frictionless & secure!
Get the latest updates! Subscribe now!
Thank you! Your submission has been received!
Oops! Something went wrong while submitting the form.


Benefits You Can Quantify
Save Time
Save 45–60 seconds per authentication & reclaim hours of clinician time every week
Reduce IT Burden
80% fewer password‑reset tickets means IT teams focus on higher‑value work
Stronger Security
Phishing‑resistant factors and real‑time policy controls
Happier Clinicians
Frictionless login keeps attention on patient care, not passwords

Compliance & Certifications

EPCS

Security & Privacy Rules

Authenticator Assurance
Level 2/3
Level 2/3

Audited infrastructure
Frequently Asked Questions (FAQ)