Passwordless & usernameless authentication for frontline systems

Enable frictionless & secure access to shared devices, apps & SSO using physical identity factors
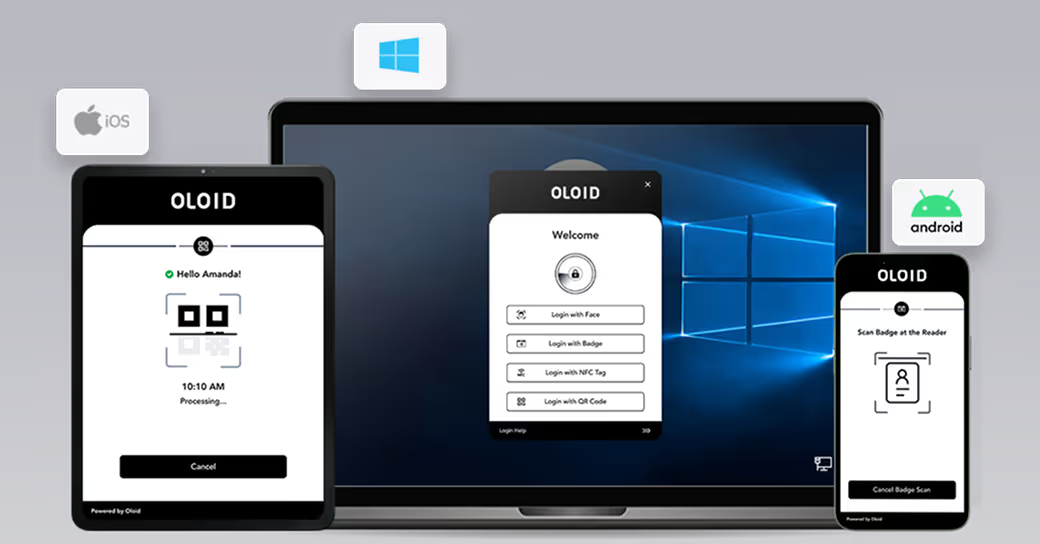
Flexible Passwordless Access
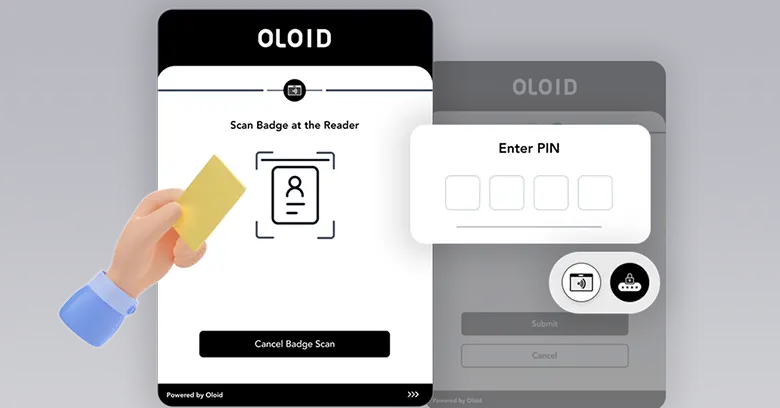
Phishing-Resistant MFA
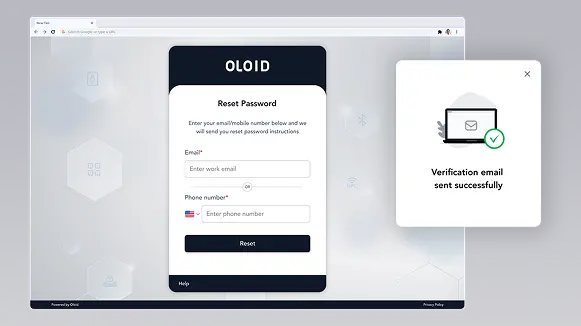
Reduced IT Overhead with Self-service Resets
Flexible, adaptive & secure authentication for each use case





Address the biggest challenges of passwordless adoption
Built with FIDO2 and Passkeys Compatibility
Credential Lifecycle & Auto-Provisioning

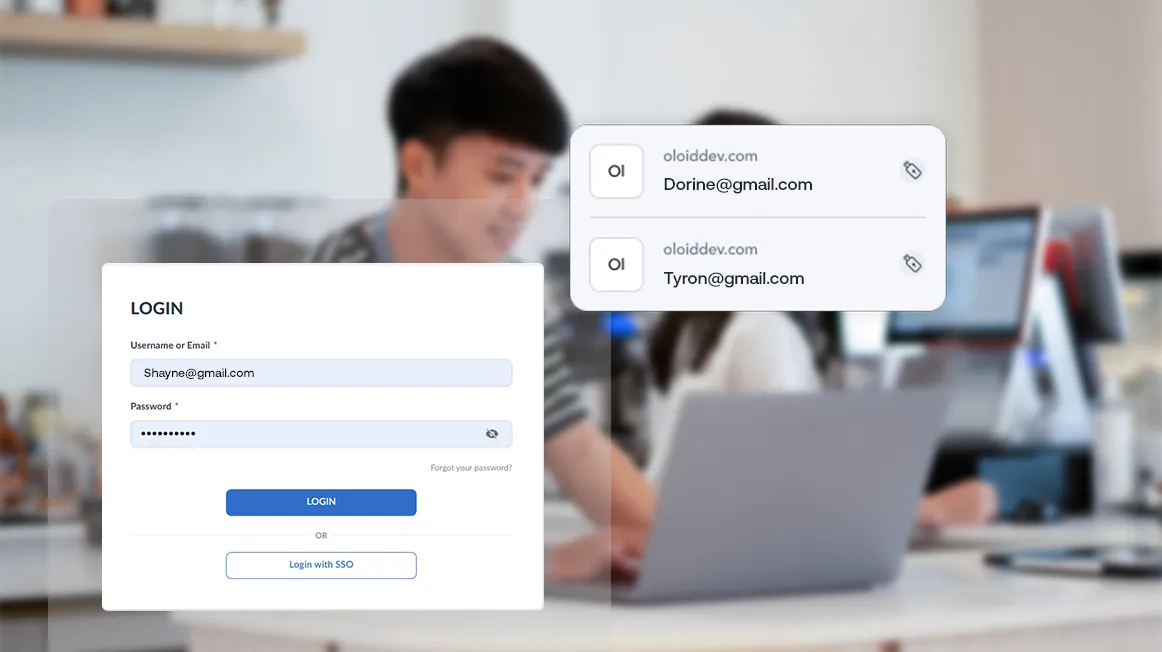
Compatible with Existing SSO Systems

Integrates with Existing MDM Solutions
.webp)
Continuous authentication & presence detection
Continuous Authentication
Verifies that the user accessing the device is the authorized user who had originally logged in. Options to block screen, automatically logout or report incidents to supervisor and security teams.

Presence Detection
Tracks the continuous presence of authorized device users using camera-based silhouette detection. Detects unauthorized personnel and image capture devices like smartphones/cameras

Auditable Logs for Compliance
Provides detailed logs and audits of shared account usage, ensuring activity of every individual on shared devices, even when workers use shared credentials

Turn workplace identity and access into a competitive advantage




Self-service password resets and account recovery for frontline workers
Empower your frontline workforce to quickly regain access to accounts on their own, reducing downtime and reliance on IT support for password-related issues, reducing password reset tickets & saving IT resources

Phising-resistant MFA using multiple factors
like face recognition and badges ensures that unauthorized users are locked out of critical systems, keeping your organization secure.

Employees can authenticate instantly
using convenient factors like face recognition and badge tap eliminating password-related delays and allowing them to access devices and systems seamlessly.
Featured integrations
Hear from our customers
FAQs on passwordless authentication for frontline systems
What authentication methods does OLOID support for frontline workers?

Can OLOID be used on shared frontline devices like tablets, workstations, or handheld scanners?

Is OLOID’s passwordless authentication phishing-resistant?

Does OLOID integrate with existing SSO systems like Okta or Entra ID?

Can the platform track which user performed actions on shared accounts?

Get the latest updates! Subscribe now!




































