Securing Shared Devices Without Shared Passwords
Shared devices are vital in frontline work, but shared passwords and legacy MFA can’t meet the demands of shift-based, high-turnover environments. Modern security needs contactless, passwordless solutions that scale, ensuring secure access, individual accountability, and fast ROI.
Frontline workers drive essential operations in factories, clinics, warehouses, and stores, but they're stuck with authentication systems built for office environments, not shared devices and rotating shifts. In these high-pressure settings, shared passwords have become a dangerous necessity.
Across multiple shifts, dozens of workers access the same terminals using shared credentials written on sticky notes or passed along verbally. While this seems practical, the risk of shared passwords in manufacturing includes broken audit trails, compliance violations, security vulnerabilities, and hidden costs that most organizations underestimate. Passwordless shared device access offers a modern alternative designed specifically for these frontline environments.
These risks raise critical questions for frontline operations:
- What happens to accountability when thirty workers share one login?
- Can your organization survive a compliance audit with shared password practices?
- How much is password sharing costing in IT support and lost productivity?
- How do you maintain security when PPE prevents traditional authentication?
This complete guide examines the specific risks shared passwords create for frontline workers. We'll break down the security, compliance, and operational dangers, quantify the real costs, and explore authentication solutions built for shared-device environments.
The Hidden Risks Behind Shared Passwords
Shared passwords may seem like a minor operational shortcut, especially in fast-paced frontline environments, but for large enterprises, they represent a serious and often underestimated cybersecurity risk. These credentials, routinely passed between shift workers or posted near shared devices, erode the very foundations of enterprise security: individual accountability, traceability, and access control. For cybersecurity leaders, this isn't just a user behavior issue; it’s a structural vulnerability that introduces real exposure across security, compliance, and operational domains.
When login activity can’t be tied to a specific individual, audit trails break down, investigations stall, and compliance with frameworks like HIPAA, PCI DSS, NIST, and ISO 27001 becomes nearly impossible. Meanwhile, frontline workers, frustrated by slow, outdated login methods, resort to risky workarounds just to keep up with the demands of their roles. These realities strain IT resources, inflate support costs, and undermine the very tools meant to protect critical systems.
The cost of shared credentials is more than just a security concern; it’s a compound problem affecting productivity, compliance, and enterprise agility. It’s time to take a closer look at the hidden risks behind shared passwords and why organizations need to move beyond them.
1. Lack of Traceability
When multiple employees use the same credentials on a shared device, all user activity appears identical in system logs. This erases individual accountability, making it impossible to determine who performed specific actions which could become a major obstacle during security investigations or incident response.
This lack of traceability doesn’t just weaken security; it introduces significant audit and compliance risks. Standards like HIPAA, PCI DSS, and NIST SP 800-53 mandate user-specific access controls and detailed activity logs. Shared logins make it difficult, if not impossible, to meet these requirements, often leading to failed audits, heightened regulatory scrutiny, and severe consequences. These can include hefty fines, legal liability, and even loss of certification or the right to operate in regulated industries.
According to the 2025 Verizon Data Breach Investigations Report, 22% of breaches still stem from stolen or misused credentials - further highlighting the risk of anonymous, shared access.
Example: Gaps in Audit Trails Due to Shared Logins
In many healthcare environments, staff may use a common login such as "med-staff01" to access shared workstations. To save time, the password might be posted nearby or shared verbally.
While this simplifies access during busy periods, it makes it difficult to trace who accessed what, when, and why, especially in the event of a data review or compliance audit.
2. Poor Employee Login Experiences lead to risky shortcuts
A broken access experience is another leading reason why organizations seek change. As technology becomes more prevalent in frontline environments, employees are increasingly frustrated by slow, inconsistent, or impractical login processes, especially when using shared devices or working in fast-paced, physical conditions.
According to Okta's 2023 report, 67% of frontline workers report being frustrated by outdated or inefficient access methods, and many admit to using risky workarounds like password sharing or writing credentials down just to stay productive.
These frustrations not only reduce efficiency but also undermine morale and increase resistance to security protocols. By implementing passwordless, user-friendly authentication, organizations can eliminate these pain points, streamline operations, and demonstrate that security measures are designed to support, not hinder, the workforce.
3. Increased Exposure Risk
Sharing login credentials across multiple users significantly increases the risk of unauthorized access. If those credentials are leaked, guessed, or retained by a former employee, they may continue accessing sensitive systems undetected.
In some workplaces, credentials are not stored securely - written on sticky notes, whiteboards, or exposed through unsecured documents, further exposing systems to internal and external threats.
This practice also complicates offboarding. Revoking access for one person requires changing a shared password used by many, which can disrupt operations and delay critical tasks. Updating and securely distributing the new password creates security risks and usually requires IT to support password resets and restore access when locked out.
4. Higher IT Costs
While often overshadowed by security concerns, the IT operational burden of managing shared credentials is significant - and growing. For many organizations, especially those with large frontline workforces, password-related issues quietly drain budgets, reduce IT efficiency, and strain support teams.
5. Productivity Loss from Inefficient Access
Shared logins and outdated authentication methods create friction in daily workflows. Frontline employees often waste time logging in and out of shared systems, re-authenticating throughout shifts, or waiting for access resets. Even a 15 to 20 delay can add up, especially in fast-paced environments where speed, efficiency and productivity are critical.
In some cases, workers avoid logging out entirely to save time, which introduces additional security risks. And when credentials are forgotten, lost, or reset for the entire team, productivity takes a direct hit. By eliminating these bottlenecks with passwordless, fast, and role-based access, organizations can free up valuable time and keep frontline operations moving without unnecessary interruptions.
Why Traditional MFA Fails Frontline Teams
Shared passwords are only part of the problem. Even when organizations implement multi-factor authentication (MFA), the tools often fall short, particularly in frontline environments where the realities of daily operations differ significantly from office settings.
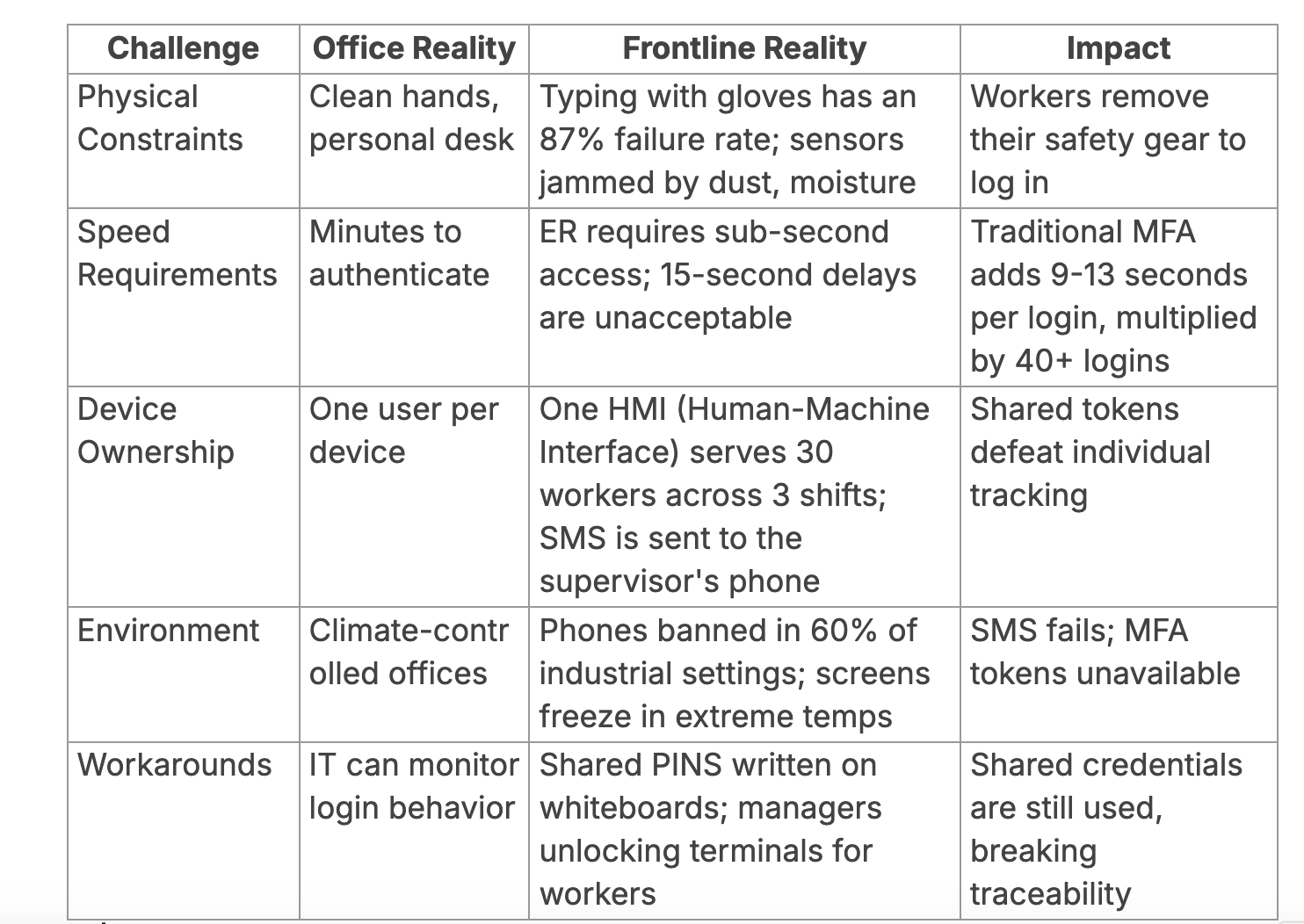
Most MFA systems were designed for desk-based employees. They assume each worker has their own device, unrestricted access to a mobile phone, and the time to complete multi-step login processes. But in places like hospitals, warehouses, and manufacturing plants, those assumptions don’t hold up.
Where Traditional MFA Breaks Down
- Physical constraints like gloves and PPE make typing and fingerprint scans difficult or unreliable
- Mobile device bans due to safety or hygiene concerns eliminate phone-based authentication
- Shared passwords are common on terminals used across multiple shifts, leading to session confusion, frequent reauthentication, and the loss of individual accountability.
- Login delays of even a few seconds can disrupt fast-paced workflows, leading workers to bypass security entirely
When authentication becomes a bottleneck, users find workarounds. They stay logged in, share credentials, or ask supervisors to unlock systems for them. These shortcuts introduce new vulnerabilities and ultimately defeat the very purpose of MFA.
To better understand the disconnect, let’s compare how traditional MFA performs in office environments versus frontline settings.
Office MFA vs. Frontline Reality: A Side-by-Side View
Warning Signs Your MFA Is Failing
- Authentication challenges make up more than 40% of IT help desk calls
- Workers share login credentials or ask managers to "unlock it for me"
- Productivity drops and user satisfaction tanks due to login delays
Running the Numbers: The Real Cost of Passwords
You’re already paying for passwords, you just don’t see the invoice.
Every year, shared logins and outdated authentication methods drain time, money, and morale. The costs may be hidden, but they’re very real.
The Hidden Costs of Passwords
Help Desk Costs from Password Resets
Even conservative estimates reveal significant expenses:
- Average cost per reset: $35
- Average resets per frontline worker/year: 12
- For a 1,000-employee organization:
- 12,000 resets × $35 = $420,000 annually
Note: These are still conservative estimates. Actual figures can vary significantly depending on your organization's size, structure, and industry.
Productivity Loss from Login Errors
Failed login attempts disrupt workflow and waste time at scale:
- Average logins per frontline worker/year: ~880
- 5% error rate: 95,000+ failed logins/year (for 2,000 users)
- Each failed attempt wastes ~10 seconds
- Total time lost: 264+ hours/year
- Estimated productivity cost: $13,000+ annually
Amplified Disruption in Shared Environments
Shared credentials create disproportionate disruptions:
- A single reset can affect dozens of users, halting productivity across an entire shift
- Credential changes on shared terminals lead to cascading delays and access confusion
- Workarounds like posted passwords or verbal sharing increase the IT burden and introduce new risks
These disruptions result in lost production time, greater reliance on support, and heightened vulnerability, all of which carry operational and financial impact.
IT Resource Drain
Password issues tie up critical IT resources:
- Teams spend hours per week on low-value, repetitive tasks: lockouts, resets, access coordination
- These tasks pull attention away from high-priority work such as automation, cybersecurity, and system upgrades
- Over time, this creates longer project timelines, slower incident response, and reduced organizational agility
IT capacity is one of your most valuable assets, password friction squanders it.
Compliance Risk and Regulatory Exposure
Shared logins and lack of user-specific authentication undermine compliance:
- Standards like HIPAA, PCI DSS, NIST SP 800-53, and ISO 27001 require traceability and individual accountability
- Shared credentials make it nearly impossible to produce accurate audit logs or assign responsibility during investigations
- A failed audit can result in:
- Hefty fines
- Legal exposure
- Loss of certification or operational license
- Heightened regulatory scrutiny going forward
In regulated industries, these outcomes can delay projects, increase administrative overhead, and restrict business operations.
Typical ROI Timeline
Most organizations recover their investment in 6 to 8 months, primarily through reductions in help desk tickets. Full ROI is typically achieved within 12 to 18 months, with additional long-term gains in efficiency, security, and regulatory assurance.
So the bottom line is -
The true cost of passwords is much larger than most organizations realize. From hidden IT labor to lost productivity and compliance risk, password-based access drains your resources on multiple fronts. In frontline environments, where shared devices and shift work are the norm, costs compound every day.
It’s time to move beyond passwords, and reclaim that value.
The Better Way: Passwordless and Usernameless Authentication
It’s time to replace them with a solution purpose-built for the frontline: passwordless, usernameless authentication that delivers security, speed, and traceability, without compromise.
Key Benefits
Instant, Effortless Access
- Sub-2-second logins using facial recognition or badge tap
- Proximity-based authentication using RFID or NFC to detect approaching users
- QR code login for environments where shared hardware is limited
- Support for FIDO2/WebAuthn security keys in specialized workflows
Robust Security by Design
- Biometric templates are encrypted and stored locally, never uploaded to the cloud
- Passive liveness detection ensures only real, present users can authenticate
- Built on a zero-knowledge architecture: OLOID cannot access raw biometric data
- Compliant with GDPR, HIPAA, CCPA, NIST, and ISO 27001 standards
- Scoped PINs and supervisor badge overrides for emergency or fallback access
Traceability and Accountability on Shared Devices
- Every session is tied to a verified individual; no generic or shared accounts
- Real-time integration with your SIEM and Identity Provider (IdP)
- Comprehensive audit trails support compliance and incident response
- Built-in consent collection, right-to-delete, and data portability capabilities
Smarter Device and Session Management
- Auto-lock sessions when users step away to prevent unauthorized access
- Role-Based Access Control (RBAC) without relying on shared credentials
- Unlimited users per terminal with seamless transitions between sessions
- Endpoint protection compatibility for antivirus, patching, and policy enforcement
Seamless Enterprise Integration
- Works out of the box with Windows, Android, iOS, and web applications
- Connects with your HR systems for automated user provisioning and lifecycle management
- Supports Single Sign-On (SSO) and centralized policy enforcement
- Continuous monitoring and real-time alerts through SIEM integration
Real-World Wins
Organizations across healthcare, manufacturing, pharmaceutical, retail, and contact centers are transforming frontline operations with OLOID's passwordless access platform. One standout example is Tyson Foods, where scale, complexity, and security intersect daily.
Tyson Foods
With 140,000 employees spread across 140 production facilities, Tyson Foods relied heavily on shared devices for shift-based operations. But outdated logins were slow, inconsistent, and left security gaps.
Results after implementing OLOID:
- Over 5,000 shared terminals secured across the enterprise
- Login times reduced from 45 seconds to under 2 seconds using facial recognition and badge-based authentication
- Password resets eliminated, slashing help desk volume and IT overhead
- Full user traceability is achieved through audit logs tied to individual identities
- Return on investment realized in under 4 months, driven by productivity gains and support cost savings
Across industries, OLOID customers report similar benefits:
- Hospitals: Faster EHR access, improved patient data protection, HIPAA-aligned audit trails
- Retailers: Streamlined point-of-sale access during shift transitions without card sharing
- Manufacturers: Touchless logins that comply with PPE protocols and accelerate workstation turnover
Five Steps to a Smooth Rollout
A successful transition to passwordless authentication, especially in dynamic frontline settings, hinges on careful planning, user-centric design, and phased implementation. Here’s how leading organizations roll out OLOID effectively:
1. Assess Physical and Environmental Constraints
Map out real-world usage scenarios across departments. Consider lighting conditions, PPE use, glove interference, mobile phone restrictions, and hardware availability to determine the best authentication method for each zone.
2. Select the Right Authentication Mix
Choose from facial recognition, badge/NFC tap, QR code login, or FIDO2 security keys, or combine them. OLOID allows hybrid configurations tailored to your workforce, environment, and compliance needs.
3. Engage, Educate, and Empower Frontline Staff
Communicate the “why” clearly: faster logins, better security, less password frustration. Use supervised self-enrollment and simple training sessions to accelerate adoption and build confidence among users.
4. Pilot with a Focused Group
Start with a single site or team to validate assumptions, test infrastructure, and gather feedback. Use this data to refine policies and workflows before scaling across additional locations.
5. Scale Strategically with Continuous Monitoring
Roll out in phases while monitoring authentication metrics, user feedback, and system performance. Leverage OLOID’s analytics and SIEM integration to measure adoption, efficiency, and risk mitigation.
Best Practice Checklist
To get the most from your investment in passwordless, usernameless authentication, follow these proven best practices from real-world OLOID deployments:
- Implement liveness detection to prevent spoofing and ensure real-time presence
- Enable presence-based auto-lock to secure terminals when users step away
- Configure scoped PINs and supervisor badges as backup authentication options
- Support QR codes and FIDO2 security keys for environments with variable constraints
- Export authentication logs regularly to your SIEM for compliance and auditing
- Engage frontline teams early with transparent communication, training, and feedback loops
- Leverage existing infrastructure (badges, cameras, access control systems) to accelerate deployment and reduce cost
- Run pilot programs before scaling to test under real conditions and build internal momentum
Conclusion: Leave Shared Passwords Behind
Passwords were never designed for the realities of the frontline - shared devices, rotating shifts, and PPE make them both inconvenient and insecure. They create friction for workers and risk for organizations, compromising both productivity and compliance.
Passwordless authentication bridges this gap, delivering fast, secure access with full user accountability. It empowers frontline teams to work efficiently without sacrificing safety.
With OLOID, organizations with frontline workers can modernize shared device access, reduce IT overhead, and achieve rapid ROI, all while strengthening security where it matters most.
Ready to see it in action? Book a 30-minute demo and experience passwordless login in under 2 seconds.
FAQs
1. What is the most effective passwordless solution for shared frontline devices?
The ideal solution depends on your environment. OLOID supports facial recognition with passive liveness detection for clean or clinical settings, badge or NFC tap for rugged or gloved environments, and QR code or FIDO2 security key options for flexible access. A hybrid approach often provides the best coverage across use cases.
2. How does OLOID secure shared workstations in hospitals, factories, or warehouses?
OLOID replaces shared logins with individual, passwordless access via facial recognition, badge tap, or QR code. Sessions auto-lock when users step away, and every login is traceable, helping you meet HIPAA, NIST, and ISO compliance standards even in high-turnover, shift-based environments.
3. Can shared device access be audited at the individual level?
Yes. OLOID ties each session to a verified individual, enabling complete audit trails across all shared terminals. These logs can be exported to your SIEM system for real-time visibility, threat detection, and compliance reporting.
4. Why do traditional MFA solutions fail for frontline teams?
Most MFA systems assume users have personal smartphones, stable connectivity, and time for multi-step logins. Frontline environments involve gloves, PPE, mobile phone restrictions, and shared devices, making traditional MFA impractical and often bypassed.
5. How quickly can organizations realize ROI with OLOID?
Most customers see return on investment within 4 to 8 months. Savings come from reduced help desk tickets, faster shift transitions, and eliminated password resets, plus long-term gains in compliance, efficiency, and risk reduction.
6. How is individual activity tracked on a shared terminal?
OLOID logs every login and action against a unique user identity, facial, badge, or QR-based. This eliminates the ambiguity of generic logins like "staff01" and enables full accountability and traceability.
7. How does OLOID prevent unauthorized access to shared devices?
OLOID uses biometric authentication with liveness detection, badge tap with role-based access, and presence-based auto-locking. Fallback mechanisms like scoped PINs and supervisor badges are available, ensuring that only authorized users can access the terminal.
8. What happens if a camera fails or a badge is lost?
OLOID offers layered fallback options including scoped PINs and supervisor override badges. Every access method is still tied to an individual user and recorded in audit logs for accountability and traceability.
9. Is biometric data secure and privacy-compliant?
Absolutely. OLOID stores biometric data as encrypted mathematical templates on the device itself, never in the cloud. The platform complies with GDPR, HIPAA, CCPA, and BIPA regulations, and includes built-in consent tracking and right-to-delete controls.



Get the latest updates! Subscribe now!




