10 Best SSO Solutions for 2026 [Expert Comparison]
Modern Single Sign-On solutions deliver secure, seamless access across enterprise applications while reducing password fatigue and identity risks. This comprehensive comparison of the 10 best SSO platforms examines authentication protocols, integration capabilities, and real-world performance. From Okta to Microsoft Entra ID and OLOID, discover which SSO solution aligns with your organization's security, compliance, and user experience priorities.

As organizations accelerate digital transformation and adopt Zero Trust frameworks, SSO has evolved from a convenience feature to a critical security requirement. Today’s Single Sign-On platforms offer passwordless capabilities, adaptive authentication, and unified identity management across hybrid and multi-cloud environments.
However, with hundreds of vendors offering the same SSO capabilities, choosing the right platform requires evaluating authentication protocols, integration depth, and scalability. The best solution strikes a balance between robust security and a frictionless user experience, seamlessly integrating into your existing identity infrastructure.
This blog compares the top 10 SSO solutions for 2026, examining their capabilities, integration ecosystems, and ideal use cases. You’ll also discover the key factors to consider when selecting an SSO platform to enhance both security and productivity.
Our Methodology for Selecting the Best Single Sign-On Platforms
We conducted a rigorous analysis of over 40 SSO providers to identify the most secure, scalable, and user-friendly platforms for enterprise deployment. Our evaluation focused on the critical parameters most important to IT leaders, security teams, and end users.
1. Supported Authentication Protocols (SAML, OAuth, OpenID Connect, etc.)
We prioritized platforms offering comprehensive protocol support, including SAML 2.0, OAuth 2.0, OpenID Connect (OIDC), and WS-Federation. Broad protocol compatibility ensures seamless integration with both modern cloud applications and legacy enterprise systems, reducing implementation friction and technical debt.
2. Integration with IAM, MFA, and Directory Services
We assessed each platform's ability to integrate with Identity and Access Management (IAM) systems, multi-factor authentication tools, and directory services, including Active Directory, LDAP, and cloud-based identity providers. Deep integration capabilities enable centralized identity governance and streamlined user provisioning across the organization.
3. User Experience and Admin Simplicity
We evaluated the end-user login experience and administrative interface for each platform. The best SSO solutions deliver frictionless authentication for users while providing IT teams with intuitive dashboards, policy management tools, and comprehensive visibility into access patterns.
4. Security and Compliance Readiness
We examined built-in security features, including session management, adaptive access controls, anomaly detection, and compliance certifications. Platforms demonstrating strong alignment with frameworks like SOC 2, GDPR, ISO 27001, and NIST received higher priority in our evaluation.
5. Deployment Flexibility (Cloud, Hybrid, or On-Premise)
We analyzed deployment options to ensure compatibility with diverse infrastructure models. The strongest SSO platforms offer flexible deployment across cloud-native, hybrid, and on-premise environments without sacrificing performance or security capabilities.
6. Pricing and ROI
We compared licensing models, per-user costs, and total cost of ownership across enterprise tiers. Solutions delivering measurable ROI through reduced IT overhead, improved security posture, and enhanced productivity ranked highest in our cost-effectiveness analysis.
These evaluation criteria helped us identify the 10 best SSO solutions for 2026, ensuring each platform meets the demanding security, usability, and integration requirements of modern enterprises. Let's examine how these platforms compare head-to-head.
Head-to-Head Comparison: 10 Best SSO Solutions in 2026
Here's a comprehensive comparison of the leading SSO platforms, highlighting their strengths, ideal use cases, and key differentiators:
Now that we’ve compared the leading SSO platforms across key criteria such as security, integrations, and scalability, it’s time to take a deeper look at what sets each one apart.
[[cta]]
Detailed Overview of the Top SSO Platforms
Each SSO platform brings its own approach to balancing security, usability, and scalability. Below is a closer look at how the top providers compare in terms of authentication capabilities, integration flexibility, and overall enterprise readiness.
1. Okta
Best For: Large enterprises needing an extensive app catalog and identity federation
Okta stands as one of the most comprehensive identity platforms available, offering Single Sign-On alongside a complete Identity and Access Management suite. With over 7,000 pre-built integrations, Okta seamlessly connects users to virtually any cloud, mobile, or legacy application through a unified authentication experience.
The platform's Universal Directory serves as a centralized identity source, automatically syncing with HR systems and external directories to maintain accurate user profiles. Okta's adaptive authentication engine analyzes contextual signals, including device posture, network location, and user behavior, to dynamically enforce appropriate security measures without disrupting legitimate access.
Key Features of Okta
- Extensive Application Catalog: Offers pre-configured SSO templates for over 7,000 SaaS, web, and mobile applications, facilitating rapid deployment with minimal technical configuration.
- Adaptive Multi-Factor Authentication: Integrates risk-based authentication policies that dynamically adjust security requirements based on login context, device trust, and behavioral patterns.
- Universal Directory: Centralizes identity management with a flexible schema, automated synchronization from multiple sources, and granular attribute mapping for consistent user profiles.
- API Access Management: Offers OAuth 2.0 and OpenID Connect support for securing APIs, microservices, and custom applications with token-based authentication and fine-grained authorization.
2. Microsoft Entra ID
Best For: Organizations deeply invested in the Microsoft ecosystem
Microsoft Entra ID, formerly Azure Active Directory, delivers enterprise-grade identity and access management with deep integration across the Microsoft stack. It provides seamless SSO to Microsoft 365 applications, Azure services, and thousands of third-party SaaS platforms through a unified identity fabric.
Entra ID's conditional access engine evaluates real-time signals, including user risk level, device compliance state, location, and application sensitivity, to enforce granular access policies. Integration with Microsoft Defender for Identity adds threat detection and automated response capabilities, strengthening the overall security posture.
Key Features of Microsoft Entra ID
- Native Microsoft Integration: Delivers seamless authentication across Microsoft 365, Azure, Dynamics 365, and Windows environments with minimal configuration overhead.
- Conditional Access Policies: Enforce intelligent access controls based on real-time risk assessments, device health, location, and user context to enable adaptive security.
- Hybrid Identity Support: Bridges on-premises Active Directory with cloud services through Azure AD Connect, enabling gradual cloud migration while maintaining existing infrastructure.
- Passwordless Authentication: Supports Windows Hello, FIDO2 security keys, and Microsoft Authenticator for phishing-resistant, user-friendly authentication experiences.
3. OLOID
Best For: Enterprises with frontline workforces requiring frictionless, compliant, and secure access
OLOID redefines enterprise SSO with a passwordless authentication platform designed specifically for the challenges of modern, distributed workforces. Unlike traditional SSO solutions that rely on typed passwords or mobile devices, OLOID enables frictionless authentication through biometrics, NFC credentials, QR codes, and badge-based access, eliminating password fatigue and credential theft risks.
OLOID's passwordless authentication solution uniquely unifies physical and digital identity, allowing the same credentials that grant building access also to authenticate users to enterprise applications. This convergence simplifies identity management, reduces credential sprawl, and delivers consistent security policies across both physical and digital access points.
OLOID's deviceless authentication approach proves especially valuable for frontline workers in manufacturing, healthcare, retail, and logistics environments where shared workstations are standard and personal device policies are impractical. The platform integrates seamlessly with existing IAM systems, directory services, and enterprise applications through standard protocols like SAML and OIDC.
Key Features of OLOID
- Passwordless & Deviceless Authentication: Enables secure access through facial recognition, RFID badges, QR codes, and NFC tags, eliminating the need for passwords or personal mobile devices.
- Unified Physical & Digital Identity: Converges building access and application authentication under a single identity platform, streamlining credential management across the enterprise.
- Frontline Workforce Optimization: Delivers fast, frictionless authentication designed for shared workstations, high-turnover environments, and users without dedicated devices.
- Seamless IAM Integration: Connects with major identity providers, including Okta, Microsoft Entra ID, Ping Identity, and ADP, through standard protocols for centralized governance.
- Phishing-Resistant MFA: Provides FIDO2-certified authentication methods that eliminate vulnerabilities associated with passwords, SMS codes, and traditional two-factor approaches.
User Reviews of OLOID
Organizations using OLOID consistently highlight its simplicity, scalability, and innovation in enabling passwordless workforce authentication. Below are a few insights from customers who have adopted OLOID to modernize their access management.
5/5 Stars
OLOID provides an effortless yet secure entry system in our office without having to go through various complicated steps to scrutinize an employee's identity, hence being reliable.” - Kirk Evangelio O. Fleet specialist, Mid-Market (51-1000 emp.)
4.7/5 Stars
“OLOID has been very accommodating in developing and delivering what we are asking without extensive back and forth ticketing processes and costly changes. Our experience with the team assigned to our project has been nothing but excellent. They have allowed us to test and give feedback. They have provided us with the packaging for managing our own delivery which we have had challenges with other vendors.” - Verified User in Food Production, Enterprise
[[cta-2]]
4. JumpCloud
Best For: Mid-market companies seeking an AD alternative with SSO
JumpCloud offers an open directory platform that reimagines identity and access management for cloud-first organizations. By consolidating user authentication, device management, and application access into a single platform, JumpCloud eliminates the need for multiple point solutions while reducing infrastructure overhead.
JumpCloud's SSO capabilities extend beyond web applications to include infrastructure access through SSH key management, LDAP authentication, and RADIUS integration. This comprehensive approach makes it particularly appealing to technology companies and distributed teams requiring unified access control across diverse resources.
Key Features of JumpCloud
- Cloud Directory Platform: Delivers centralized user management without on-premises infrastructure, providing a modern alternative to Active Directory for cloud-native organizations.
- Cross-Platform Device Management: Manages Windows, Mac, and Linux endpoints with unified policies, automated patching, and remote command execution.
- Application & Infrastructure SSO: Extends single sign-on beyond web apps to include servers, networks, and IT resources through LDAP, RADIUS, and SSH protocols.
- Conditional Access Policies: Enforce context-aware authentication requirements based on device compliance, location, and security posture.
5. Rippling
Best For: Fast-growing companies want an all-in-one identity & HR solution
Rippling stands out by combining workforce management with identity and access control in a single unified platform. This integration automatically provisions user accounts, assigns applications, and configures device access based on HR data, eliminating manual workflows and reducing onboarding time from days to minutes.
Rippling's SSO implementation integrates seamlessly with its broader platform capabilities, including device management, software deployment, and compliance reporting. For organizations valuing operational efficiency alongside security, Rippling offers compelling advantages through its unified approach to employee systems management.
Key Features of Rippling
- Automated Identity Lifecycle: Synchronizes access provisioning with HR events, automatically creating accounts, assigning applications, and adjusting permissions based on employee status.
- Unified HR-IT Platform: Combines payroll, benefits, device management, and identity access in one system, eliminating data silos and duplicate entry.
- App Management & Deployment: Manages SaaS subscriptions, SSO access, and software licenses with automated provisioning and usage tracking.
- Device-to-Identity Binding: Links company devices directly to user identities, enabling automated configuration, security policies, and remote management.
6. Oracle SSO
Best For: Large organizations already operating within the Oracle infrastructure
Oracle Identity Management provides comprehensive SSO capabilities designed for complex enterprise environments with demanding security and compliance requirements. The platform excels in federating identities across Oracle's extensive application portfolio, including E-Business Suite, PeopleSoft, JD Edwards, and Oracle Cloud Applications.
Oracle's approach emphasizes identity governance and administration, offering detailed access certification, segregation-of-duties enforcement, and comprehensive audit capabilities. These features make it particularly attractive to highly regulated industries requiring stringent identity controls and detailed compliance reporting.
Key Features of Oracle SSO
- Oracle Application Integration: Offers comprehensive, pre-built connectors for Oracle's enterprise application suite that require minimal configuration.
- Identity Governance Controls: Enforces access certification workflows, separation of duties policies, and role-based access management with comprehensive audit trails.
- Federation & Standards Support: Implements SAML, OAuth, OpenID Connect, and WS-Federation for identity federation across diverse systems and partner organizations.
- Hybrid Deployment Options: Supports cloud, on-premises, and hybrid architectures to accommodate complex enterprise requirements and regulatory constraints.
7. Cisco Duo
Best For: Security-first organizations implementing Zero Trust architecture
Cisco Duo delivers identity-centric security through its comprehensive approach to authentication, device trust, and access control. Beyond basic SSO functionality, Duo provides continuous device health assessment, ensuring that only trusted, compliant devices can access corporate resources regardless of network location.
The platform's Zero Trust Network Access capabilities extend security beyond perimeter-based models by verifying both user identity and device posture before granting access to applications. This approach proves especially valuable for distributed workforces and BYOD environments where traditional network security controls are ineffective.
Key Features of Cisco Duo
- Device Trust & Health Verification: Continuously assesses device security posture, operating system versions, and compliance status before allowing access to applications.
- Zero Trust Network Access (ZTNA): Provides identity-based network access that eliminates implicit trust, ensuring continuous verification regardless of user location.
- Phishing-Resistant Authentication: Supports FIDO2 security keys, WebAuthn, and push notifications that prevent credential phishing and man-in-the-middle attacks.
- Secure Remote Access: Enables secure connectivity to internal applications without the complexity of VPNs through application-aware access controls.
8. 1Password
Best For: SMBs and tech teams needing a password vault + SSO combination
1Password Extended Access Management combines the company's renowned password vault with enterprise SSO capabilities, creating a unified security platform for credential management. This integration ensures that while SSO handles application access, sensitive credentials, API keys, and secrets remain securely vaulted and properly governed.
The platform appeals particularly to development teams and security-conscious organizations that need both SSO for business applications and secure secrets management for infrastructure access. 1Password's developer-friendly approach includes CLI tools, API integrations, and automation capabilities that streamline credential management across the development lifecycle.
Key Features of 1Password
- Unified Password Vault & SSO: Combines enterprise SSO with secure credential storage, ensuring comprehensive protection for both SSO and non-SSO applications.
- Secrets Management: Provides secure storage and sharing of API keys, database credentials, certificates, and infrastructure secrets with access controls and audit logging.
- Developer Integration: Offers CLI tools, SDKs, and API access for automated credential management in CI/CD pipelines and infrastructure-as-code workflows.
- Security Reporting & Insights: Delivers visibility into password health, credential reuse, and security vulnerabilities across the organization.
9. Auth0
Best For: Companies building custom apps requiring embedded authentication
Auth0 offers a developer-centric identity platform designed to integrate authentication and authorization into custom applications seamlessly. The platform offers extensive customization capabilities through Universal Login, enabling organizations to create branded, seamless authentication experiences that match their application design.
Auth0's strength lies in its flexibility for complex authentication scenarios, including multi-tenant applications, B2C identity management, and progressive profiling. The platform's extensibility via rules, hooks, and actions enables developers to implement custom authentication logic without building an identity infrastructure from scratch.
Key Features of Auth0
- Customizable Authentication Experience: Provides Universal Login with extensive branding and UX customization to create seamless, application-native authentication flows.
- Multi-Tenant Architecture Support: Enables sophisticated multi-tenant application designs with isolated identity domains and organization-specific configurations.
- Extensible Authentication Pipeline: Offers rules, hooks, and actions for implementing custom authentication logic, fraud detection, and integration workflows.
- Comprehensive Protocol Support: Implements OAuth 2.0, OpenID Connect, SAML, WS-Federation, and LDAP for broad compatibility with modern and legacy systems.
10. Citrix
Best For: Enterprises with Citrix virtual desktop infrastructure
Citrix Workspace provides SSO capabilities as part of its broader digital workspace platform, consolidating access to applications, desktops, and data through a unified interface. The platform excels in environments where virtual application delivery and desktop virtualization form core components of the IT strategy.
For organizations with significant investments in Citrix infrastructure, the platform's SSO capabilities offer native integration advantages and simplified administration. Citrix's focus on secure remote access and application delivery ensures optimized performance even for bandwidth-intensive virtualized applications.
Key Features of Citrix
- Unified Workspace Aggregation: Consolidates SSO access to web apps, SaaS services, virtual applications, and published desktops in a single user interface.
- Intelligent Resource Orchestration: Automatically presents contextually relevant applications based on user role, device type, and current tasks.
- Virtual Application Delivery: Provides secure access to legacy and Windows applications through virtualization, eliminating the need for application refactoring.
- Session Management & Recording: Offers detailed session monitoring, recording, and analytics for compliance and security incident investigation.
8 Factors to Consider While Choosing an SSO Platform
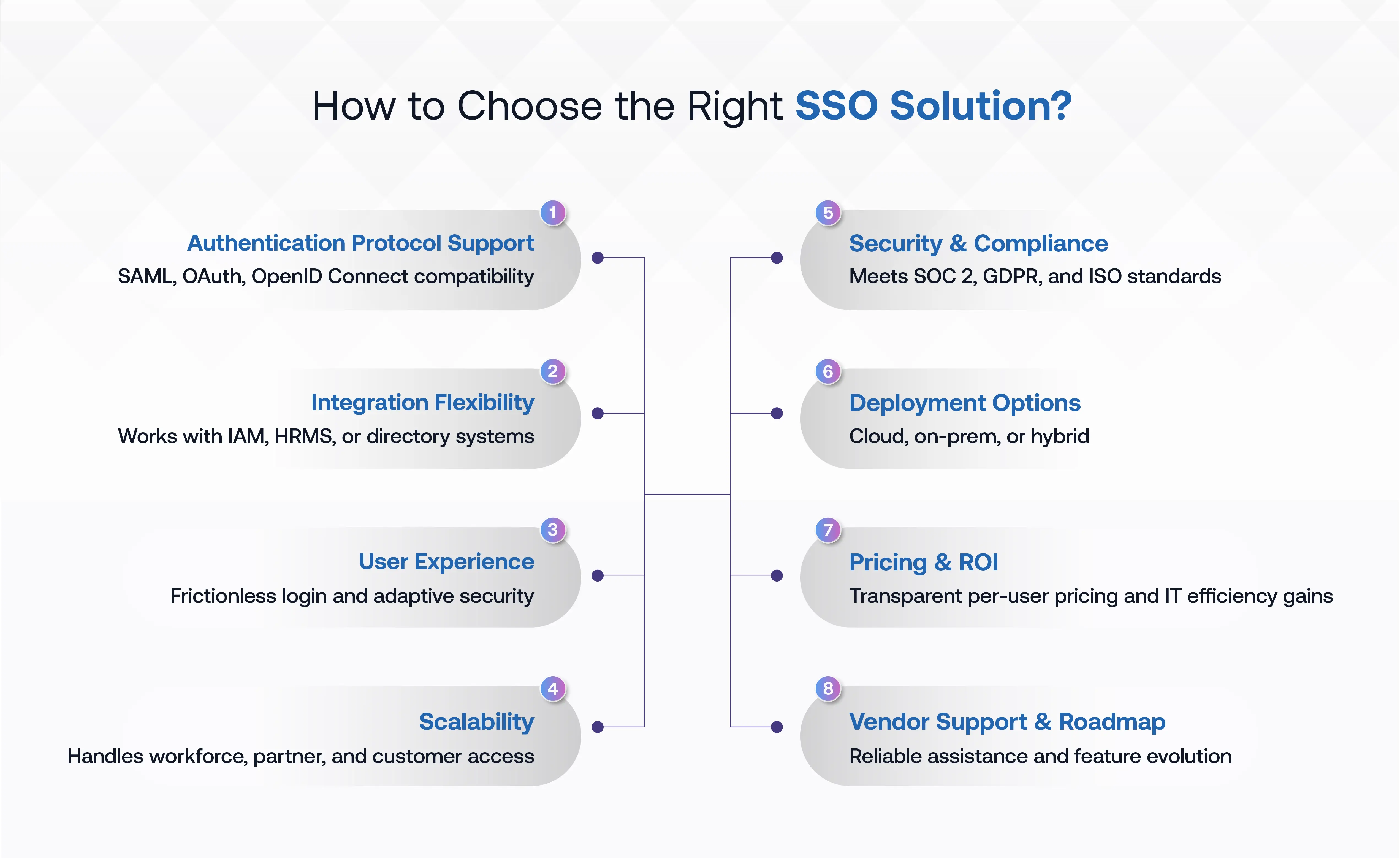
Selecting the right SSO platform requires a careful evaluation that extends beyond surface-level features. The ideal solution must enhance security posture, improve user productivity, and integrate seamlessly with your existing technology ecosystem. Here are eight critical factors that should guide your decision-making process.
1. Authentication Protocol Support
Ensure your chosen platform supports modern authentication standards, including SAML 2.0, OAuth 2.0, OpenID Connect (OIDC), and WS-Federation. Platforms like OLOID and Microsoft Entra ID offer broad protocol support, ensuring seamless integration with both modern cloud applications and legacy enterprise systems.
Platforms lacking comprehensive protocol support create integration gaps that require costly workarounds or limit application coverage. Look for solutions that enable protocol flexibility on a per-application basis, allowing you to use the most appropriate authentication method for each system in your environment.
2. Integration Flexibility
Your SSO solution must integrate deeply with existing Identity and Access Management systems, HR platforms, directory services, and business applications. Evaluate pre-built connectors, API capabilities, and support for SCIM provisioning to ensure smooth data synchronization and automated user lifecycle management.
Platforms offering extensive integration marketplaces reduce implementation time and ongoing maintenance burden. Consider whether the solution supports both cloud-based and on-premises integration patterns to accommodate your current and future infrastructure requirements.
3. User Experience
The best SSO implementation becomes invisible to users while dramatically simplifying their daily authentication experience. Assess the login flow across desktop, mobile, and web interfaces to ensure consistency and minimal friction. Consider how the platform handles session management, idle timeouts, and seamless transitions between applications.
Platforms that strike a balance between security and usability drive higher adoption rates and reduce shadow IT risks. Features such as persistent sessions, adaptive authentication, and passwordless options significantly enhance user satisfaction while maintaining a strong security posture.
4. Scalability
Your chosen SSO platform must accommodate current user populations while scaling effortlessly as your organization grows. Evaluate performance characteristics under load, geographic distribution capabilities, and support for various user types, including employees, contractors, partners, and customers.
Consider platforms like OLOID that offer flexible licensing models and architectural designs capable of supporting millions of authentication requests without degradation. Solutions built on cloud-native architectures typically scale more efficiently than legacy systems, which often require hardware upgrades.
5. Security & Compliance
Verify that prospective platforms maintain relevant security certifications, including SOC 2 Type II, ISO 27001, and industry-specific standards such as HIPAA or PCI-DSS, where applicable. Review built-in security features such as anomaly detection, impossible travel alerts, session hijacking prevention, and detailed audit logging.
Ensure the platform supports compliance requirements for data residency, retention policies, and regulatory reporting. Solutions offering comprehensive compliance reporting and automated evidence collection simplify audit processes and reduce compliance overhead.
6. Deployment Options
Match the SSO platform's deployment model to your infrastructure strategy and security requirements. Cloud-native solutions offer rapid deployment and reduced operational overhead, while on-premises options provide maximum control over sensitive identity data.
Many organizations benefit from hybrid deployment models that keep critical identity infrastructure on-premises while leveraging cloud services for application integration and user access. Evaluate how each deployment option affects disaster recovery, business continuity, and geographic redundancy requirements.
7. Pricing & ROI
Look beyond initial licensing costs to evaluate the total cost of ownership, including implementation services, ongoing maintenance, support fees, and administrative overhead. Consider per-user pricing models, tiered feature sets, and potential cost increases as your organization scales.
Calculate expected ROI based on measurable benefits such as reduced IT support tickets for password resets, improved security posture preventing breach costs, and enhanced employee productivity through faster application access. Organizations typically see positive ROI within the first year through operational efficiency gains alone.
8. Vendor Support & Roadmap
Assess the vendor's commitment to product innovation, security updates, and customer success. Review the product roadmap to ensure alignment with emerging technologies, such as passwordless authentication, Zero Trust architectures, and AI-driven security analytics.
Evaluate support offerings, including response time guarantees, dedicated account management, and access to technical resources during implementation. Vendors with active user communities, comprehensive documentation, and regular feature releases demonstrate long-term platform viability and commitment to customer success.
[[cta-3]]
Redefine Workforce Access with OLOID’s Passwordless SSO
In an era of sophisticated cyber threats and distributed workforces, Single Sign-On has evolved from a convenience feature to a security imperative. Modern SSO platforms eliminate password-related vulnerabilities while simplifying access management across increasingly complex application landscapes. The shift toward passwordless and Zero Trust architectures represents the future of enterprise authentication.
OLOID’s passwordless authentication platform leads this transformation by unifying physical and digital identity under a single, password-free experience. With native support for front-line, desk-based, and shift-based workers, OLOID eliminates credentials as an attack vector and enables deviceless, factor-based authentication, even on shared devices.
Why OLOID stands apart:
- True passwordless and username-less login using face recognition, badge/NFC tap, QR code, PIN, no dependency on mobile phones or email.
- Seamless integration into your existing SSO ecosystem (OIDC, SAML, SCIM protocols) and directory/HR/PACS systems.
- Unified access across digital apps and physical environments, supporting shared devices, kiosks, factory HMIs, POS systems, and more.
- Reduced IT overhead + enhanced security posture through self-service resets for frontline workers, continuous authentication, presence detection, and centralized audit logs.
Ready to experience the future of enterprise SSO? Schedule a personalized demo with OLOID's team to see how passwordless authentication can transform your organization's access management.
FAQs on Single Sign-On Solutions
1. What are the most secure Single Sign-On solutions?
The most secure SSO solutions implement phishing-resistant MFA authentication methods, including FIDO2 security keys, biometric verification, and passwordless technologies. Platforms like OLOID, Microsoft Entra ID, Cisco Duo, and Okta offer advanced security features, including adaptive authentication, device trust verification, and continuous risk assessment.
Security strength also depends on the proper implementation of modern protocols, such as SAML 2.0, OAuth 2.0, and OpenID Connect. Prioritize platforms that maintain SOC 2 Type II and ISO 27001 certifications, and offer anomaly detection and context-aware access policies for the strongest protection.
2. Which SSO platforms are best for enterprises or SMBs?
For large enterprises, Okta, Microsoft Entra ID, OLOID, and Oracle SSO deliver the scalability, governance controls, and extensive integration capabilities required for complex environments. These platforms support millions of users and provide detailed compliance reporting.
Mid-sized businesses benefit from JumpCloud, 1Password, and Rippling, which offer comprehensive functionality without the complexity typically associated with enterprise solutions.
3. Can SSO integrate with MFA or passwordless authentication?
Yes, modern SSO platforms integrate seamlessly with multi-factor authentication and passwordless systems. Combining SSO with MFA represents current best practices in security. Leading platforms, such as OLOID, Okta, Microsoft Entra ID, and Cisco Duo, offer native MFA integration that supports biometrics, FIDO2 security keys, push notifications, and one-time passwords.
4. What are the main benefits of implementing SSO?
SSO delivers strategic benefits across security, productivity, and operational efficiency. It reduces password-related vulnerabilities by minimizing credential sprawl and enabling centralized access controls. User productivity improves as employees save 5-10 minutes daily managing passwords.
IT teams benefit from automated user provisioning, resulting in 50-70% reductions in password-related support requests. Additional benefits include enhanced compliance reporting, improved visibility into application usage, streamlined onboarding processes, and detailed audit trails. SSO platforms also reduce shadow IT risks by making legitimate applications easier to access and manage.
5. How do I choose the right SSO provider for my organization?
Select an SSO provider by evaluating your organizational needs, existing infrastructure, and security strategy. Assess your application landscape and workforce composition—organizations with frontline workers need solutions like OLOID's passwordless authentication, while Microsoft-centric environments benefit from Entra ID.
Evaluate authentication protocol support, integration capabilities with IAM and HR systems, deployment flexibility, security compliance, user experience, scalability, and total cost of ownership. Request proof-of-concept deployments to validate performance in your specific environment before making a decision.



Get the latest updates! Subscribe now!



