Enterprise SSO: The Key to Secure, Seamless Access Management for Modern Businesses
Enterprise SSO simplifies secure access by allowing employees to log in once and use multiple business applications without having to re-enter their credentials. This blog examines how Enterprise SSO operates, its key benefits for security, compliance, and productivity, and the challenges organizations encounter during implementation. It also outlines best practices and guidance on selecting the right SSO solution.

How many passwords do your employees juggle every day, for email, CRM, HR systems, project tools, and analytics dashboards?
Now multiply that by hundreds or even thousands of users across your organization. The result? A constant battle between security and convenience, where password fatigue, forgotten credentials, and unauthorized access attempts drain IT resources and put data at risk.
That’s where Enterprise Single Sign-On (SSO) comes in. By allowing users to authenticate once and securely access all approved applications, Enterprise SSO eliminates password sprawl, improves security compliance, and simplifies user management across hybrid and cloud environments.
For IT leaders and security teams, it answers critical questions like:
- How can we simplify authentication without compromising security?
- How do we ensure compliance and visibility across hundreds of applications?
- What’s the best way to enable passwordless, seamless access at enterprise scale?
This blog explores everything you need to know about Enterprise SSO, from how it works and why it’s essential to its business benefits, key features, and implementation best practices. You’ll also see how modern enterprise SSO platforms help modern enterprises deliver secure, frictionless access across all digital touchpoints.
What is Enterprise SSO (Single Sign-On)?
Enterprise Single Sign-On (SSO) is an authentication system that allows employees to access multiple business applications and systems using a single set of login credentials. Instead of remembering and managing passwords for every tool (CRM, HR portal, email, or analytics platform), users log in once and gain secure access to all authorized applications within the enterprise environment.
At its core, Enterprise SSO simplifies identity management while strengthening security. It connects an organization’s identity provider (such as Active Directory or Azure AD) with the various apps and systems employees use daily. When a user signs in, the system authenticates their identity once and issues a secure session token, allowing seamless access to integrated services without repeated logins.
Enterprise SSO also forms a critical component of a broader Identity and Access Management (IAM) framework. While consumer SSO (like “Sign in with Google” or “Login with Facebook”) focuses on convenience for individual users across public websites, enterprise-grade SSO is designed for scalability, governance, and compliance.
How Enterprise SSO Works: Protocols & Architecture
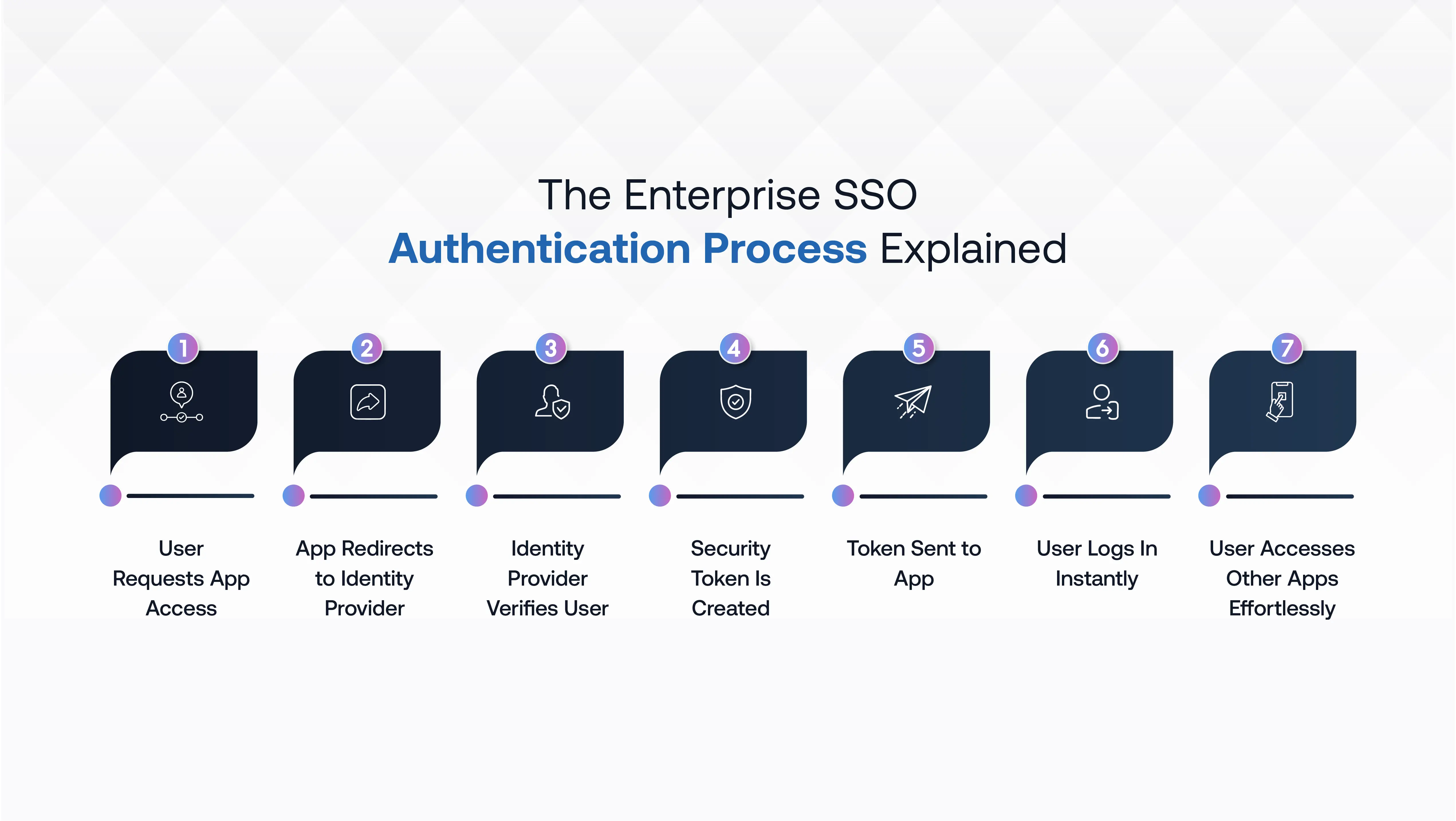
Single Sign-On for enterprises enables employees to log in once and securely access all connected applications without re-entering their credentials. It centralizes authentication through a trusted Identity provider (IdP), improving both security and user convenience across business systems.
Step 1: User Tries to Access a Business Application
When a user attempts to open a company app, that application (Service Provider) recognizes that SSO is configured. Instead of asking for credentials, it redirects the user to the company’s Identity Provider (IdP) for authentication.
Process Overview:
- The user clicks or opens a company application. (e.g., Salesforce or Zoom)
- The app detects that SSO is enabled and initiates a redirect.
- The redirection ensures credentials are verified only by the trusted IdP.
- This keeps sensitive login data out of third-party apps.
Step 2: Application Sends an Authentication Request
The Service Provider then sends an authentication request to the Identity Provider to confirm the user’s identity. This secure, digitally signed request contains all necessary details to ensure the integrity and legitimacy of the login attempt.
Authentication Request Includes:
- The app’s unique identifier (Entity ID).
- A redirect/callback URL to receive the authentication response.
- A digital signature to confirm authenticity.
- Supported protocol type (SAML, OAuth 2.0, or OIDC).
Step 3: Identity Provider Authenticates the User
Once redirected, the user is presented with the IdP's corporate login screen. The IdP verifies credentials using company directories such as Active Directory or LDAP, often with an added layer of security through Multi-Factor Authentication (MFA).
Authentication Steps:
- The user enters their corporate username and password.
- The IdP validates credentials against a secure directory.
- MFA or biometric checks may be required for stronger security.
- Once verified, the IdP issues a security token.
Step 4: Identity Provider Issues a Security Token
After successful verification, the Identity Provider generates a secure, signed token or assertion that carries identity data. This token serves as proof that the IdP has authenticated the user.
Token Details:
- Contains user identity, roles, and attributes.
- Includes timestamps, expiry info, and audience details.
- Protected by a digital signature to prevent tampering.
- Token formats include SAML assertions (XML) or JWTs (JSON).
Step 5: Token Is Sent Back to the Application
The Identity Provider sends the signed token back to the Service Provider’s Assertion Consumer Service (ACS) endpoint. The application then validates this token to confirm the user’s authenticity before granting access.
Verification Checks:
- Confirms the IdP’s signature is valid.
- Ensures the token has not expired or been modified.
- Verifies the “audience” field matches the target app.
- Once verified, the SP creates a session for the user.
Step 6: User Gains Access Without Re-Login
After token verification, the Service Provider establishes a secure session and grants immediate access to the requested application. Users can now interact freely without re-entering their credentials for the duration of the session.
Key Benefits:
- Provides seamless access without multiple logins.
- Reduces password fatigue and login friction.
- Enhances productivity by saving time.
- Maintains strong security through token-based validation.
Step 7: Seamless Access to Other Apps
When the same user later opens another SSO-integrated app, they are redirected to the IdP again. Since they are already authenticated, the IdP issues a new token immediately, granting access without requiring another login.
Seamless Access Process:
- The user opens another enterprise app (e.g., Slack or Jira).
- The app redirects the user to the IdP.
- The IdP recognizes the active session and skips re-authentication.
Enterprise SSO simplifies secure access by using a single authentication process across multiple systems. It reduces password fatigue, enhances security through centralized authentication, and provides a smooth user experience across all enterprise tools. Next, let’s explore the benefits of implementing SSO in enterprise environments.
[[cta]]
What are the Benefits of Enterprise Single-Sign-On
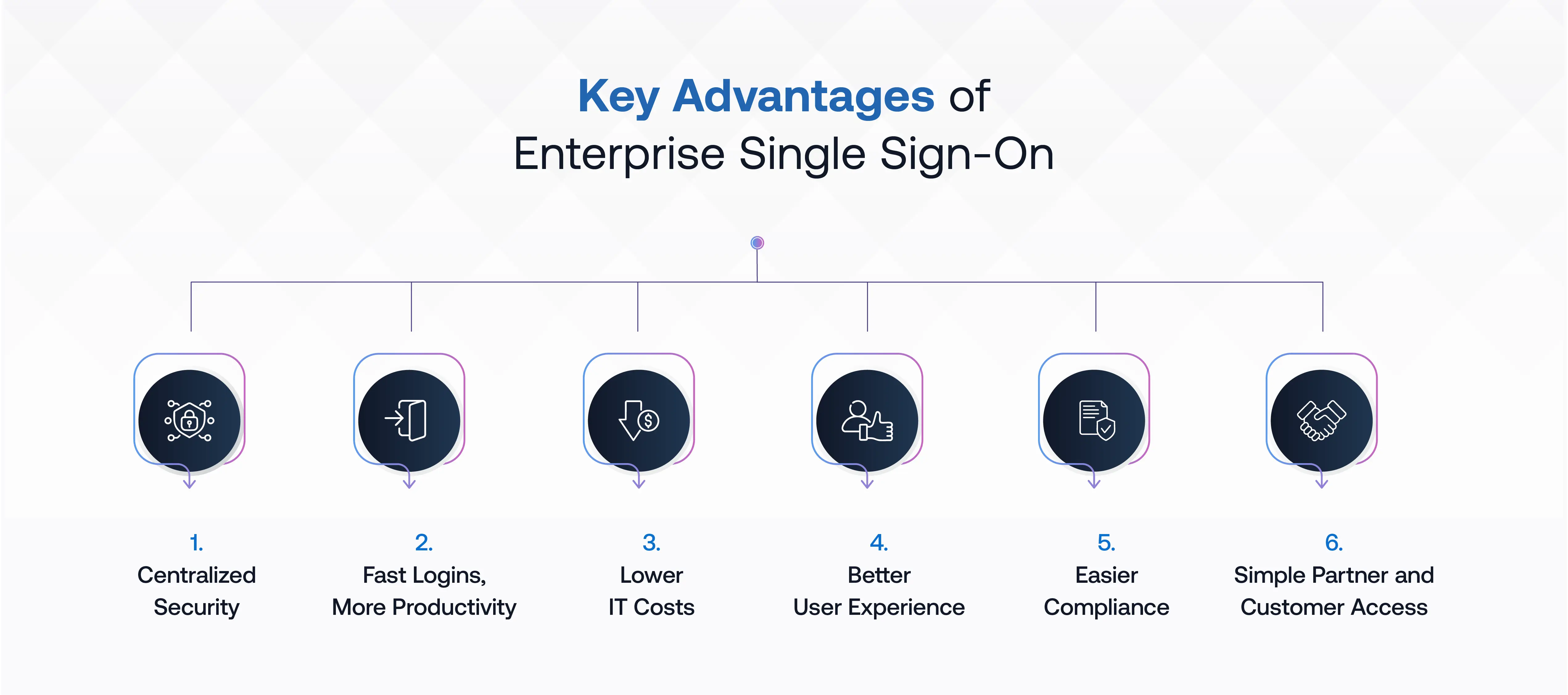
Adopting SSO transforms the way users authenticate across platforms, delivering tangible value to both IT leaders and employees. Here are the seven strongest reasons enterprises should prioritize SSO.
1. Powerful Security with Centralized Control
Enterprise SSO significantly decreases the risk of data breaches and phishing by limiting password exposure and enforcing strong authentication from a single provider. One compromised credential no longer means unrestricted access throughout the enterprise. This makes threat detection and incident response much more manageable. Centralized control also enables rapid deprovisioning, instantly cutting off access to ex-employees.
2. Time Savings and Higher Productivity
Employees sign in once and instantly access all their business-critical tools, saving hours that would otherwise be lost to repeated login screens and password resets. SSO is especially impactful for mobile, hybrid, and remote teams who routinely switch between dozens of apps.
For frontline industries such as manufacturing, healthcare, and retail, where time and productivity are critical, an SSO-enabled passwordless authentication solution like OLOID can be beneficial. For enterprises, the collective time saved annually using such platforms translates to primary business wins in efficiency and employee engagement.
3. Lower IT Costs and Admin Burden
SSO minimizes inbound support tickets related to password issues, resulting in substantial cost savings and freeing IT staff to focus on high-priority projects. Centralized access also allows easier license management and less “shadow IT.” Companies often see immediate ROI from lower helpdesk volume and streamlined account administration.
4. Enhanced User Experience Drives Engagement
A seamless login experience encourages confident adoption of digital workplace solutions. Employees, partners, and customers stay engaged when constant authentication prompts don’t disrupt their workflow. SSO also supports hassle-free onboarding and facilitates a smooth user migration when upgrading applications or platforms.
5. Superior Compliance and Audit Readiness
Centralizing authentication through SSO enables more robust tracking and logging for compliance frameworks, such as GDPR, HIPAA, and SOC 2. Auditors can access clean, unified records of user activity, while policy enforcement is both consistent and scalable across all business applications. This transparency helps enterprises avoid penalties and regulatory failures.
6. Seamless Partner, Vendor, and Customer Integrations
SSO enables secure, federated logins for business partners and external stakeholders, improving collaboration while maintaining access control. Enterprises can automate provisioning and deprovisioning (often with SCIM), eliminating bottlenecks and supporting growth across multi-organization environments.
From advanced security to world-class user experiences, the business case for enterprise SSO is clear. However, to fully realize these benefits, enterprises should approach SSO implementation carefully.
Planning an Enterprise SSO Implementation: Here’s How to Approach
A strategic enterprise SSO rollout should be divided into distinct phases, each with actionable steps that balance organizational goals and technical readiness. Here is a streamlined approach for every stage of SSO implementation.
1. Planning and Requirements Gathering
Begin with a thorough understanding of your organization's priorities, applications, and technical environment. Comprehensive planning at this phase sets a solid foundation for the entire deployment and increases project success rates.
What to Do
- Establish specific business goals such as security, productivity, and lower IT costs.
- Prepare a detailed list of all cloud and on-premises applications to onboard.
- Rank applications by criticality, data sensitivity, and user base for phased rollout.
- Involve relevant stakeholders, including IT, security, department heads, and end users.
- Select the best-fit Identity Provider (IdP) by evaluating its features and compatibility.
- Select authentication protocols, such as SAML, OIDC, or Kerberos, based on the application's specific needs.
- Assess technical compatibility and plan for bridging gaps in legacy systems.
- Define provisioning and account management—JIT or SCIM—for automating the user lifecycle.
2. Design and Implementation
Move from requirements to action by configuring your identity provider, establishing access policies, and integrating service providers. This phase hinges on secure execution and minimizing disruption during setup.
What to Do
- Configure trust relationships between the IdP and all enterprise applications.
- Set up role and attribute mapping for granular access controls.
- Integrate organizational user directories like Active Directory with your IdP.
- Connect applications using selected protocols for seamless authentication.
- Enforce multi-factor authentication to bolster security and protect against credential theft.
- Implement Role-Based Access Control (RBAC) to ensure that all users have the least-privileged access.
- Deploy centralized logging and monitoring to track authentication and support audits.
3. Testing and Organizational Rollout
Testing is essential for validating system reliability, user experience, and performance before scaling SSO across all departments. Proactive communication and phased rollout are key to maximizing adoption.
What to Do
- Launch SSO with a pilot user group for real-world feedback.
- Develop robust test cases for user roles, device compatibility, and edge scenarios.
- Test session management, error handling, and self-service user flows.
- Prepare training guides and support resources in advance of the launch to ensure a seamless rollout.
- Refine integration and documentation based on insights from the pilot.
- Scale up SSO deployment in stages to minimize disruption and support rapid troubleshooting.
4. Monitoring, Maintenance, and Optimization
Continuous oversight keeps SSO secure and responsive as business needs evolve. Regular audits, automation, and analytics-driven refinements ensure the system stays effective over time.
What to Do
- Automate onboarding and offboarding to prevent orphaned accounts and unauthorized access.
- Audit access permissions and roles to maintain security compliance.
- Monitor login patterns, detect anomalies, and respond to threats swiftly.
- Proactively manage certificates and schedule renewals to avoid downtime.
- Assess performance analytics and user feedback for ongoing optimization.
- Keep documentation up to date to facilitate troubleshooting and onboard new staff efficiently.
Following these clearly defined phases helps enterprises deploy SSO securely, efficiently, and with strong stakeholder buy-in. However, implementing SSO in complex enterprise environments is not always straightforward. Let’s discuss the common hurdles in SSO adoption for enterprises and how to prepare for them.
Challenges in Enterprise SSO Projects and How to Overcome

Enterprise SSO projects offer significant efficiency and security benefits, but also encounter real-world obstacles during deployment and scaling. Addressing these challenges early helps organizations ensure lasting success and smooth user experiences.
Challenge 1: Integration Complexity and Compatibility
Problem Statement
Integrating SSO across cloud, on-premises, and legacy platforms is challenging, especially when dealing with inconsistent protocol support or proprietary authentication requirements. These technical hurdles can result in extended project timelines and costly support incidents.
How to Overcome This
- Map authentication requirements for every application in advance.
- Select SSO solutions that offer broad support for protocols such as SAML, OIDC, and OAuth.
- Utilize federation or third-party gateways to integrate legacy systems.
- Conduct exhaustive application integration and regression testing.
Challenge 2: Centralized Security Risks
Problem Statement
Enterprise SSO centralizes authentication, creating a single point of failure. Credential theft or system downtime can enable broad access to critical resources, posing significant risks to an organization.
How to Overcome This
- Enforce strong multi-factor authentication and zero-trust policies.
- Conduct regular security audits and reviews of access logs.
- Design robust incident response and backup authentication processes.
- Monitor credentials for potential compromise and respond promptly to any identified threats.
Challenge 3: User Experience and Adoption Resistance
Problem Statement
If SSO login flows are confusing or complex, employees may resist change, increase support tickets, or even bypass SSO, resulting in fragmented authentication and reduced system security.
How to Overcome This
- Offer comprehensive training and clear user guides during rollout.
- Gather feedback from pilot user groups and refine sign-in flows.
- Reduce authentication friction with intuitive interfaces and help resources.
- Provide self-service options for account and password management.
Challenge 4: Scalability and Performance
Problem Statement:
As an organization grows, its SSO system may struggle to handle the increasing number of users, applications, and authentication requests. Poor scalability can cause logins to fail during peak usage periods, disrupting workflows.
How to Overcome This
- Opt for solutions built for enterprise scaling and redundancy.
- Plan regular capacity assessments and stress tests to ensure optimal performance.
- Monitor login performance and adjust infrastructure to anticipate growth.
- Design with future integrations and system expansion in mind.
Challenge 5: Ongoing Maintenance and Change Management
Problem Statement
Without consistent oversight, SSO deployments can suffer from outdated certificates, expired access policies, and operational gaps. This exposes organizations to downtime and security risks.
How to Overcome This
- Schedule regular audits of access controls and certificate renewals to ensure ongoing security.
- Automate provisioning and deprovisioning processes.
- Update documentation for troubleshooting and onboarding.
- Adapt access policies as users and apps change over time.
Organizations that tackle these challenges can achieve secure, scalable, and adoption-friendly enterprise SSO implementations, laying the groundwork for strong digital operations. Along with these insights, it is also essential to choose the right SSO provider that can meet enterprises' authentication needs. The following section explains how enterprises can identify the right SSO solution for their needs.
How to Select the Best SSO Solution for Your Enterprise Needs
Choosing the right SSO solution for your enterprise sets the foundation for secure, efficient, and scalable identity management across all business applications. Here are seven factors you should consider while comparing different SSO solutions to choose the right platform for your enterprise:
1. Security and Compliance
A top SSO solution should prevent breaches and comply with industry regulations.
- Look for strong encryption, multi-factor authentication, and adaptive security features.
- Verify audit logging, compliance certifications, and detailed reporting to support regulatory needs.
- Ensure the solution supports zero-trust principles and policy-driven access.
2. Compatibility and Integration
Seamless integration with your current environment and future projects is crucial.
- Assess compatibility with legacy systems, cloud apps, and new platforms.
- Ensure support for essential standards, including SAML, OAuth, and OIDC.
- Prioritize solutions with pre-built connectors and flexible APIs.
3. Scalability and Performance
As your organization grows, the SSO must keep pace without bottlenecks.
- Select platforms that are designed for high availability, redundancy, and fast authentication during periods of peak demand.
- Confirm capacity for future users, new app integrations, and geographic expansion.
- Run performance tests for authentication and response times.
4. User Experience
The login journey should be as simple as possible for every user.
- Evaluate options for self-service password management and intuitive interfaces to enhance user experience.
- Support multi-device and remote access needs.
- Allow interface branding to match the company’s identity.
5. Automation and Lifecycle Management
Efficient onboarding and offboarding reduce risk and manual workload.
- Utilize automated provisioning and deprovisioning with technologies such as SCIM and JIT.
- Allow hooks for HR-driven events or user role changes.
- Enable easy, rule-based access reviews.
6. Customization and Flexibility
Different teams have unique requirements that may evolve over time.
- Check for customizable authentication flows and granular policy controls.
- Ensure the solution can support multiple user groups, subsidiaries, or external partners.
- Confirm localization and support for global operations if needed.
7. Vendor Reliability and Support
A reputable provider ensures smooth deployment and ongoing success.
- Research vendor reputation, customer service, and community support.
- Compare service-level agreements and support response times to ensure optimal performance.
- Consider the vendor’s roadmap and experience in handling large enterprises.
By focusing on these categories, your enterprise can select an SSO solution that meets today’s needs while preparing you for tomorrow’s challenges. Along with the right solution, there are certain best practices to follow to ensure seamless SSO integration in your enterprise framework.
[[cta-3]]
Enterprise SSO Best Practices for Security & Scale
Following best practices for enterprise SSO is crucial because it helps organizations secure user identities, prevent costly breaches, comply with regulations, and ensure smooth scalability. Consistent strategies protect sensitive data and optimize workforce productivity, providing confidence that every login is safe and every user is accounted for.
1. Mandate Multi-Factor Authentication
Require MFA for all SSO access to significantly reduce the risk of unauthorized logins and credential theft. Strengthen security by combining passwords with authenticator codes or biometrics.
2. Apply the Principle of Least Privilege
Assign users the minimum permissions necessary for their roles to contain the blast radius of a compromised account. Regularly review and adjust privileges to ensure access is always appropriate.
3. Use Proven Authentication Protocols
Implement widely trusted protocols such as SAML, OAuth 2.0, and OpenID Connect to safeguard authentication flows and protect against advanced cyberattacks.
4. Enforce Granular Access Controls
Create specific access rules for each app and dataset, minimizing risk by allowing only verified users to access sensitive areas. Centralized controls facilitate enforcement and monitoring.
5. Activate Real-Time Monitoring and Logging
Monitor logins, sessions, and access attempts continuously to detect anomalies as soon as they occur. Detailed logs help with investigations, audits, and compliance tracking.
6. Schedule Regular Audits and Permission Reviews
Review user roles, permissions, and access logs frequently to spot and resolve excessive access or outdated settings. Keep your security posture up to date and ready for regulatory checks.
7. Enforce Session Timeout and Auto-Logout Policies
Protect data by requiring automatic logout after periods of inactivity to block unauthorized access on lost or unattended devices. Refining session policies further secures organizational assets.
By implementing these best practices, enterprise IT teams create a foundation of strong security and reliability that scales to meet future growth and evolving threats.
Unlock Secure, Seamless Enterprise Access with OLOID
SSO plays a critical role in modern business by eliminating password fatigue, reducing security risks, and simplifying IT management. It enables users to access multiple applications securely with a single set of credentials, streamlining onboarding and offboarding processes. It improves productivity by minimizing login interruptions and reducing support calls throughout the enterprise.
OLOID reimagines secure workplace access through usernameless, passwordless authentication tailored for frontline and deskless workers. By integrating biometrics, device-based access, and physical identity factors, OLOID ensures consistent, frictionless user experiences while meeting robust security and compliance.
- Passwordless authentication enhances security and eliminates reliance on vulnerable passwords.
- OLOID streamlines onboarding and life cycle management via HRIS, SSO, and physical access integrations.
- Multi-factor authentication safeguards access for frontline workers in industries with strict compliance requirements.
- CISA-mandated solutions are available for manufacturing, healthcare, and retail environments.
- Consistent user experiences across devices and apps improve workplace efficiency and security.
- Integration workflows automate account creation, updates, and deactivation for fast, secure scaling.
- Contactless time clocking supports facial recognition, NFC, and QR codes for efficient workforce management.
By leveraging OLOID, enterprises unlock next-level security and efficiency, turning workplace authentication into a strategic advantage. Book a demo today to see OLOID in action and learn how it can streamline enterprise authentication.
Frequently Asked Questions on Enterprise SSO
1. What is enterprise SSO, and how does it work?
Enterprise SSO is an authentication system that enables users to access multiple company applications and resources with a single set of login credentials. It works by connecting various applications to a centralized identity provider (IdP); once a user signs in to the IdP, access to all linked apps is granted without requiring additional logins, using secure protocols such as SAML and OAuth.
2. What are the main benefits of implementing SSO in large organizations?
SSO simplifies user access, reduces support ticket volume, strengthens security by centralizing authentication, and boosts productivity. All employees experience fewer interruptions, less password fatigue, and IT teams can enforce unified security policies and monitor activity more effectively.
3. Is SSO secure? How can organizations protect against risks?
SSO is highly secure when paired with multi-factor authentication (MFA), rigorous identity management, and continual security monitoring. Protecting the IdP is essential, as it serves as the gateway to all connected apps; therefore, organizations should enforce strong access controls, maintain audit logs, and conduct regular security reviews.
4. Can SSO be required for all users in a company?
Yes, SSO can be enforced as the mandatory login method for all employees. Organizations configure policies so that all users must authenticate via the SSO solution, centralizing identity management and eliminating weak, scattered password usage.
5. What troubleshooting steps should be followed if SSO fails?
Start by verifying user credentials and IdP connectivity, then check compatibility between the application and identity provider. Review application and network logs for errors, confirm that authentication protocols are correctly configured, and ensure that certificates and tokens are valid and up to date. Reaching out to technical support or referring to the detailed SSO documentation can further expedite the resolution.



Get the latest updates! Subscribe now!



