The OLOID Blog
Articles and Podcasts on Customer Service, AI and Automation, Product, and more


Featured
What is SSPR: Benefits, Implementation, and Security Considerations
Self-Service Password Reset (SSPR) empowers users to reset passwords and unlock accounts independently without IT helpdesk intervention. This comprehensive implementation guide covers SSPR fundamentals, step-by-step deployment in cloud and hybrid environments, authentication methods, security considerations, and proven strategies to maximize user adoption. Get actionable insights to reduce support costs, enhance productivity, and strengthen security postures.

Garima Bharti Mehta
Last Updated:
January 28, 2026


Step-By-Step Guide to Seamless MFA Implementation
Effective MFA implementation is crucial for protecting organizations against password breaches and unauthorized access. This blog offers a step-by-step guide to deploying multi-factor authentication, from assessing infrastructure to training users and optimizing performance. Learn about common implementation pitfalls, their solutions, and best practices to simplify multi-factor authentication adoption while strengthening overall security.

Rahul Mathew
Last Updated:
January 23, 2026


Passwordless Authentication for Zero-Trust: Modern Security Without Compromise
Passwordless authentication is transforming enterprise security by eliminating passwords, reducing vulnerabilities, and enhancing user experience. This blog explores methods, implementation steps, and key considerations for adopting passwordless authentication while supporting Zero-Trust principles. OLOID’s platform offers a secure, scalable solution to help organizations modernize access management effectively.

Garima Bharti Mehta
Last Updated:
December 18, 2025


What Is RFID Authentication and How Does It Work?
RFID authentication uses radio frequency technology to enable secure, contactless identity verification. It works through RFID tags and readers to grant quick and reliable access, making it a strong alternative to traditional methods like passwords or PINs. This blog explores how RFID authentication works, its applications, benefits, challenges, and best practices for effective implementation.

Garima Bharti Mehta
Last Updated:
October 30, 2025


Phishing-Resistant MFA: Complete Guide to Modern, Secure Authentication
Traditional multi-factor authentication fails against modern phishing attacks. Phishing-resistant MFA uses cryptographic technology and hardware-bound credentials to eliminate vulnerabilities that attackers exploit. This guide covers how it works, key technologies like FIDO2 and security keys, implementation steps, and real-world attack scenarios it blocks. Learn the benefits, including faster logins and stronger security.

Garima Bharti Mehta
Last Updated:
December 17, 2025


The Ultimate Guide to QR Code Authentication for Modern Security
QR code authentication revolutionizes organizational security by eliminating password vulnerabilities. This comprehensive guide covers passwordless authentication through scannable codes, comparing static versus dynamic implementations, and demonstrating superior security over traditional methods. Learn implementation methodology, security best practices, compliance requirements, risk management strategies, and real-world solutions for addressing modern authentication challenges.

Rahul Mathew
Last Updated:
January 23, 2026


NFC Authentication: Basics, Benefits, Models, and Implementation
NFC authentication revolutionizes workplace security by eliminating password vulnerabilities. It is a short-range wireless technology that verifies identity within a contactless interaction distance of four centimeters. This blog provides a comprehensive understanding of what Near Field Communication (NFC) authentication is, why it is a great alternative to traditional passwordless-based authentication, and how businesses can implement it.

Garima Bharti Mehta
Last Updated:
October 30, 2025


PIN Authentication: How It Powers Modern Business Security
PIN authentication revolutionizes workplace security by eliminating password vulnerabilities while providing instant access for frontline workers using shared devices. This technology offers superior phishing resistance through local validation and integrates seamlessly with comprehensive passwordless solutions that combine biometric verification, badge access, and NFC cards. Explore how PIN authentication works and how it can improve your security in this detailed guide.

Garima Bharti Mehta
Last Updated:
October 17, 2025


10 Key Passwordless Authentication Best Practices to Streamline Access Management
Passwordless authentication eliminates security vulnerabilities while improving user experience across organizations. This guide explores 10 essential passwordless authentication best practices. Following these proven strategies enables organizations to deploy secure, user-friendly authentication systems that reduce costs and enhance their security posture.

Garima Bharti Mehta
Last Updated:
November 24, 2025


10 Best Identity and Access Management Tools for 2026
Choosing the right Identity and Access Management (IAM) solution is critical for securing systems, managing access, and ensuring compliance in today’s hybrid and cloud-driven environments. This blog reviews the 10 best IAM tools for 2026, highlighting their key features, strengths, and ideal use cases. It also addresses common challenges, evaluation criteria, and how IAM platforms can streamline security while improving user experience, helping organizations make informed decisions.

Garima Bharti Mehta
Last Updated:
December 24, 2025


10 Best Passwordless Authentication Solutions of 2026 [Latest Rankings]
Passwordless authentication has evolved from a security trend to a business necessity, with organizations seeking alternatives to traditional password-based systems that create vulnerabilities and operational inefficiencies. This comprehensive guide examined 10 leading passwordless authentication solutions, each designed for different organizational needs and use cases.

Garima Bharti Mehta
Last Updated:
December 17, 2025


Workforce Authentication: The Key to Securing Modern Workplaces
Modern workplaces face unprecedented cyber threats, with traditional password systems creating massive security gaps. This comprehensive guide explores workforce authentication fundamentals, from traditional methods to cutting-edge passwordless solutions. Learn about implementation challenges, compliance requirements, and best practices for securing your workforce.

Garima Bharti Mehta
Last Updated:
December 17, 2025


SSO for Healthcare: Simplifying Access While Strengthening Security
The write-up explains how Single Sign-On (SSO) simplifies access to multiple healthcare systems, reducing password fatigue, improving clinical efficiency, and strengthening data security. It highlights unique compliance needs, key features of healthcare-focused SSO, implementation best practices, and how OLOID’s passwordless authentication platform enhances security, streamlines workflows, and supports HIPAA and DEA EPCS compliance for modern healthcare environments.

Rahul Mathew
Last Updated:
January 23, 2026


Biometrics in Healthcare: Transforming Patient Security and Care
Biometric technologies like fingerprint, facial, iris, and voice recognition are revolutionizing healthcare by improving patient identification, security, and operational efficiency while ensuring regulatory compliance. This blog on biometrics in healthcare highlights real-world uses, implementation challenges, and how platforms like OLOID streamline passwordless authentication for safer, faster, and more patient-friendly care.

Garima Bharti Mehta
Last Updated:
October 30, 2025


How Passwordless Login Solves Access Challenges for Factory Workers with Diverse Language Backgrounds
Multilingual factory teams struggle under English-only password systems that slow access, drive risky credential sharing, and overwhelm IT with resets. Passwordless login using facial recognition, badges, and QR codes transcends language barriers, delivering sub-second authentication, stronger security, improved worker productivity, better compliance, and lower IT costs while integrating seamlessly with existing factory systems across all shifts and facilities.

Garima Bharti Mehta
Last Updated:
November 10, 2025


10 Multi-factor Authentication Trends to Watch Out for in 2026
Multi-factor authentication (MFA) is evolving to meet rising cybersecurity challenges. Emerging trends such as biometrics, behavioral and contextual authentication, AI-driven systems, and passwordless methods are making MFA more secure and user-friendly. These advancements aim to reduce friction, prevent breaches, and align with Zero Trust principles. As businesses and individuals adopt these modern MFA solutions, they strengthen their defense against increasingly sophisticated threats.
OLOID Desk
Last Updated:
October 17, 2025


How to Achieve DEA EPCS Compliance: Authentication Solutions for Healthcare and Pharmacies
Healthcare providers and pharmacies struggle to meet strict DEA EPCS rules while juggling legacy systems and clunky two-factor logins. Secure, passwordless authentication with advanced biometric identity proofing, digital signatures, and automated audit trails solves these challenges, protecting patients, ensuring compliance, boosting workflow efficiency, and cutting IT costs while integrating seamlessly with existing EHRs.

Garima Bharti Mehta
Last Updated:
October 29, 2025


How to Use a Passkey Solution for Shared Devices: A Comprehensive Guide
Traditional passkeys fail in shared device environments because they're designed for 1:1 user-device binding, leaving frontline workers who can't use personal phones stuck with weak passwords on shared terminals. This guide explains how innovative shared device passkey solutions overcome WebAuthn limitations through multi-tenant credential stores and enterprise IAM integration, enabling phishing-resistant authentication for manufacturing, healthcare, and retail workers on shared workstations while maintaining individual accountability and FIDO2 compliance.

Rahul Mathew
Last Updated:
January 23, 2026


How to Configure Microsoft External Domain for Frontline Workers: Best Practices and Implementation
Microsoft Entra ID works well for office employees but struggles with frontline workers who share devices, can't use personal phones for MFA, and include high-turnover contractors needing temporary access. This guide explains how to configure external domains in Microsoft Entra ID to extend authentication to frontline staff, covering setup procedures, conditional access policies, automated lifecycle management, and integration with physical access system.

Garima Bharti Mehta
Last Updated:
October 17, 2025


How Face Recognition Login Works in Manufacturing: A Complete Guide
Manufacturing workers lose valuable production time struggling with passwords while wearing PPE, leading to shared credentials on factory terminals that create compliance risks and endless IT support tickets. This guide demonstrates how face recognition login solves these challenges by working seamlessly with safety equipment, providing individual accountability for regulatory compliance, and delivering proven ROI through faster shift changes and reduced IT costs, all while integrating with existing systems like ADP, Workday, and Okta.

Garima Bharti Mehta
Last Updated:
November 17, 2025


SOC 2 Compliance with Face Recognition Vaults: A Guide for Security Leaders
Security leaders often discover too late that their face recognition vendor's SOC 2 certification doesn't explicitly cover biometric data handling, creating permanent compliance risks since facial data can't be reset like passwords. This guide provides a practical framework for evaluating true SOC 2 compliance in face recognition vaults, including specific audit scope verification criteria, multi-regulatory alignment strategies (GDPR/HIPAA/BIPA), and proven solutions for deployment challenges across shared devices in manufacturing, healthcare, and retail environments.

Garima Bharti Mehta
Last Updated:
October 17, 2025


A Complete Guide to Passwordless MFA Without Mobile Devices
Traditional smartphone MFA fails in regulated industries due to safety restrictions and device bans. Learn seven deviceless authentication solutions - biometric scanners, hardware keys, badge systems, and proximity wearables - that provide enterprise security for frontline teams without requiring personal phones or creating compliance violations.

Rahul Mathew
Last Updated:
January 23, 2026


How Can Manufacturing Facilities Enable Unlimited Users on Shared Devices: A Guide
Manufacturing facilities lose productivity to password bottlenecks during shift changes and per-user licensing costs. This guide covers unlimited user authentication solutions using face recognition, badge tap, and NFC methods that eliminate passwords, reduce IT burden, and enable seamless access for thousands of workers on shared devices.

Rahul Mathew
Last Updated:
November 24, 2025


The Security Risks of Shared Passwords in Manufacturing and How Passwordless Prevents Them
Generic credentials and sticky-note passwords create massive security gaps in manufacturing environments. This comprehensive guide covers the business risks of shared logins, why they persist despite vulnerabilities, and how modern passwordless authentication delivers individual accountability while working seamlessly with existing industrial systems and workflows.

Garima Bharti Mehta
Last Updated:
January 8, 2026


How Zero-Touch PACS Makes RFID Badge Authentication Seamless Across Enterprises
RFID badges are mostly used to handle only physical access, requiring separate digital logins. Zero-touch PACS integration changes this by automatically syncing badge credentials across all systems. This guide covers implementation benefits, technical architecture, and how enterprises achieve unified authentication without manual IT provisioning overhead.

Garima Bharti Mehta
Last Updated:
November 24, 2025


The Complete Guide to Frontline IAM for Manufacturing
Manufacturing facilities struggle with shared passwords, authentication delays, and compliance gaps on factory floors. This guide explores specialized Frontline IAM solutions that enable seamless, secure access for industrial workers while integrating with OT systems and delivering measurable productivity gains.

Garima Bharti Mehta
Last Updated:
December 24, 2025

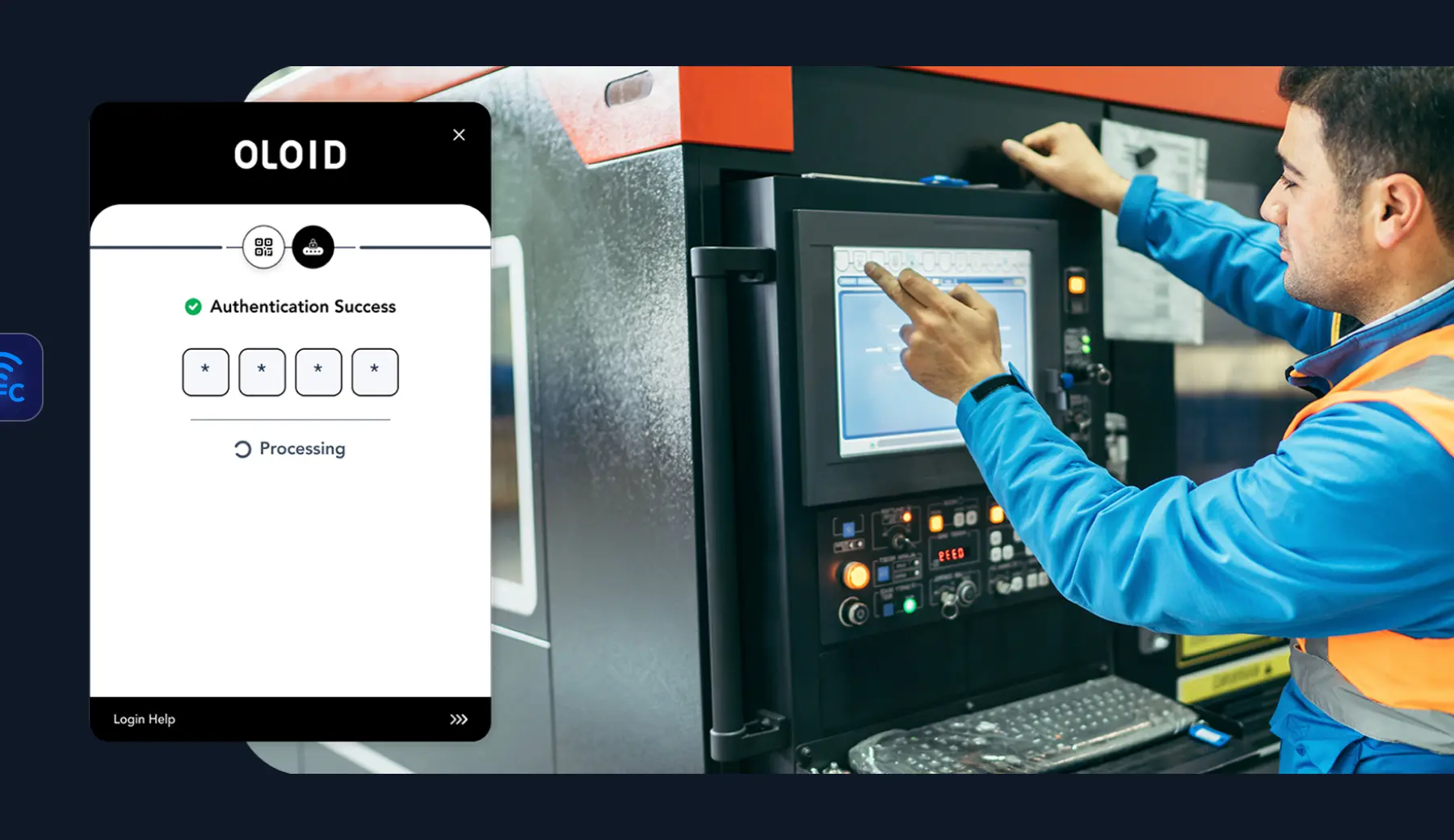
Securing Shared Devices Without Shared Passwords
Shared devices are vital in frontline work, but shared passwords and legacy MFA can’t meet the demands of shift-based, high-turnover environments. Modern security needs contactless, passwordless solutions that scale, ensuring secure access, individual accountability, and fast ROI.

Garima Bharti Mehta
Last Updated:
January 28, 2026

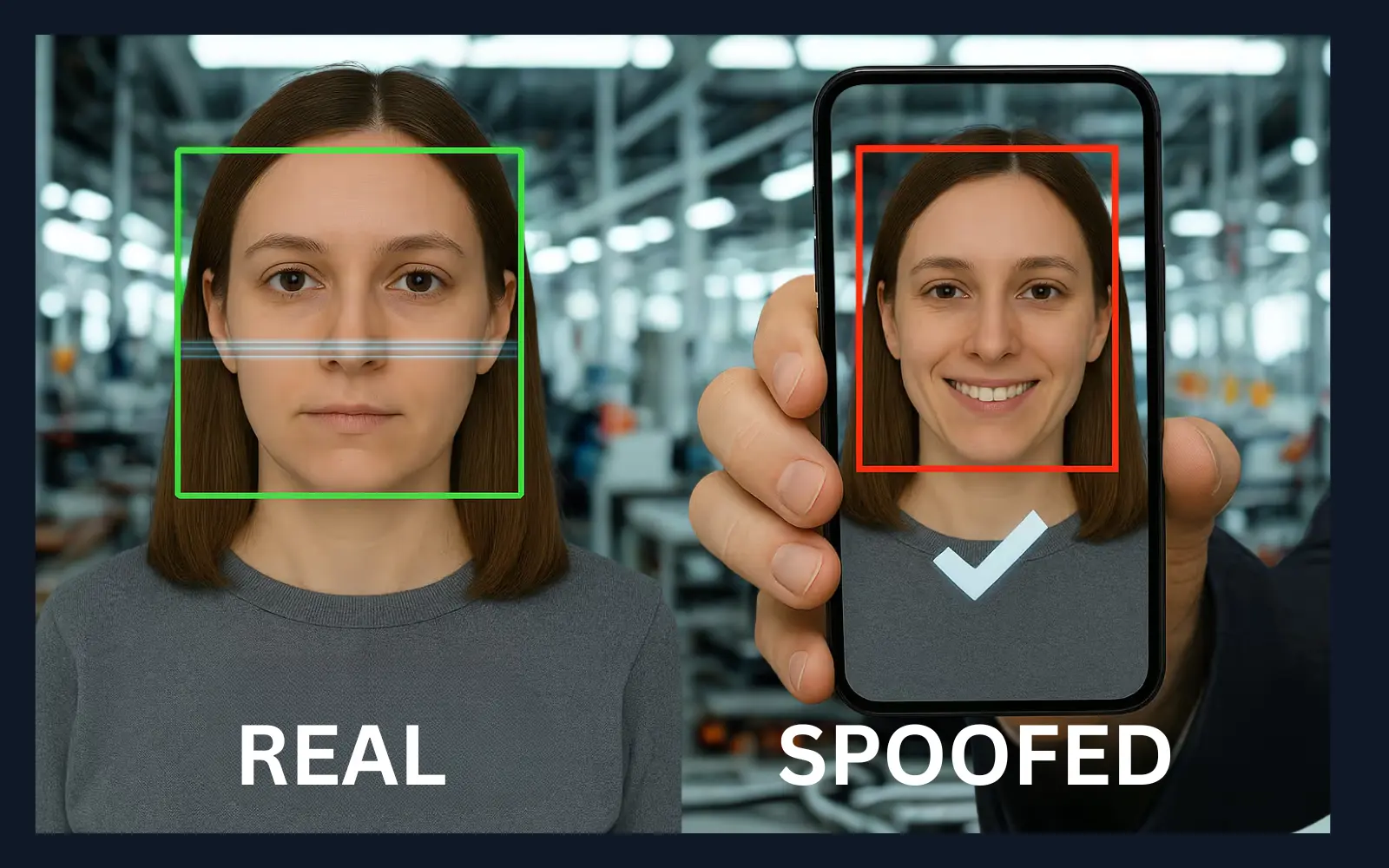
Liveness Detection Guide: Protecting Digital Identity 2026
Learn how liveness detection is revolutionizing digital identity verification in 2026. Discover the technology behind preventing spoofing attacks like deepfakes, photos, and masks. Understand its role in securing transactions, improving compliance, and enhancing security across industries such as finance, healthcare, and manufacturing.
OLOID Desk
Last Updated:
January 1, 2026


How OLOID Secures and Automates Manufacturing Access
The post explains how OLOID secures and automates access in manufacturing environments using modern identity and automation solutions. It highlights features like passwordless authentication, contactless time tracking, and workflow automation. Learn how OLOID boosts safety, efficiency, and compliance for frontline workers.
OLOID Desk
Last Updated:
November 17, 2025


OLOID at Oktane 2024 in Las Vegas
Oktane 2024 is set to prove to be, once again, the biggest Identity event of the year, based on Okta’s standing as the world’s leading identity and access management company, and their industry-leading solutions and thought leadership, along with the participation of strategic partners such as OLOID, a leading provider of physical identity and access […]
OLOID Desk
Last Updated:
October 17, 2025


OLOID at Workday Rising 2024 in Las Vegas
Workday Rising is set to prove to be, once again, the biggest Enterprise Management event of the year, based on Workday’s standing as the world’s leading Finance, HR, and Planning cloud software company, with their industry-leading solutions and thought leadership, along with the participation of innovation partners such as OLOID.
OLOID Desk
Last Updated:
November 8, 2025
Making every day-in-the-life of frontline workers frictionless & secure!
Get the latest updates! Subscribe now!
Thank you! Your submission has been received!
Oops! Something went wrong while submitting the form.
