What Is FIDO Authentication and How Does It Work?
Passwords are costing your organization millions in resets and breach risks. Learn how FIDO authentication eliminates these vulnerabilities with cryptographic, phishing-resistant security. Explore step-by-step implementation strategies, real-world use cases across industries, and the measurable benefits of one-tap biometric login.

In today’s digital world, passwords are no longer enough to protect sensitive data. Phishing attacks, credential theft, and password reuse continue to compromise security for both individuals and organizations. The solution? FIDO Authentication, a modern, passwordless approach that uses cryptographic key pairs to verify users securely and conveniently.
Unlike traditional login methods, FIDO Authentication keeps private keys on the user’s device, ensuring that credentials are never shared or exposed. Supported by major technology companies through the FIDO Alliance, this standard is rapidly becoming the foundation of secure, phishing-resistant digital identity.
In this blog, we’ll explore what FIDO Authentication is, how it works, its key benefits, real-world use cases, and a step-by-step look at implementing it effectively. By the end, you’ll have a clear understanding of why FIDO is transforming the way we access digital systems.
What Is FIDO Authentication?
FIDO (Fast Identity Online) Authentication is an open standard that enables secure, passwordless login experiences. Instead of relying on traditional passwords, it uses cryptographic key pairs to verify users. This means authentication happens locally on the user’s device, through biometrics, PINs, or security keys, making it both more secure and convenient.
Developed and maintained by the FIDO Alliance, a global consortium of technology leaders including Google, Microsoft, Apple, and others, FIDO’s mission is to reduce the world’s over-reliance on passwords. The Alliance creates and promotes interoperable authentication standards that work across devices, browsers, and operating systems.
FIDO promotes passwordless security by ensuring that private credentials never leave the user's device. During authentication, only a cryptographic proof is exchanged with the server; so even if databases are breached, no reusable credentials are exposed. This approach not only protects against phishing and credential theft but also streamlines access management for both users and organizations.
As the FIDO standard has evolved, understanding the differences between FIDO and FIDO2 helps organizations select the most appropriate authentication framework for their security requirements.
In short, FIDO Authentication represents the foundation of a secure, user-friendly, and phishing-resistant digital identity ecosystem, paving the way for a truly passwordless future.
What Are Passkeys?
Passkeys are the consumer-friendly name for FIDO2 credentials. They represent a modern way of signing in that replaces traditional passwords with cryptographic key pairs, making authentication both safer and easier for users.
When a passkey is created, your device generates two mathematically linked keys. The **private key** is stored securely on your device and never leaves it, while the **public key** is shared with the service you’re trying to sign in to. During login, the service verifies your identity using the public key, without ever needing access to the private key.
Types of Passkeys
There are two main types of passkeys: device-bound passkeys and synced passkeys.
Device-bound passkeys
These are stored on physical hardware and cannot be copied or extracted. Examples include hardware security keys like YubiKeys or smart cards. Because authentication requires physical possession of the device, this type of passkey offers stronger security guarantees.
Synced passkeys
These are stored in cloud-based credential managers and automatically sync across multiple devices. Common examples include Apple iCloud Keychain, Google Password Manager, and Windows Hello. These passkeys are more convenient for users who switch between devices frequently, but they rely on the security of the underlying cloud service.
Device-bound passkeys prioritize maximum security by requiring a specific physical device for authentication. Synced passkeys focus on convenience and accessibility, allowing users to sign in easily across devices while still providing a password-less experience.
Key Components of FIDO Authentication
FIDO Authentication relies on several integrated components working together to create passwordless security. Each component plays a specific role in verifying user identity without transmitting secrets. Understanding these elements helps you grasp how FIDO delivers both security and convenience.
1. Public Key Cryptography: The Foundation
Public key cryptography forms the security backbone of FIDO Authentication. Your device generates a unique key pair consisting of a private key and a public key. The private key stays encrypted on your authenticator and never leaves your device.
The public key registers with the service you want to access. When you authenticate, your device uses the private key to sign a challenge. The service verifies this signature using your stored public key to confirm your identity.
2. Authenticators: Your Verification Device
Authenticators are the tools that verify your identity during login attempts. They store your private keys securely and perform cryptographic operations locally. Different authenticator types suit different security needs and user preferences.
Types of authenticators:
- Biometric authenticators: Built-in fingerprint readers or facial recognition on your devices
- Hardware tokens: Physical security keys such as USB, NFC, or Bluetooth devices. These are often roaming authenticators, meaning they can be used across multiple devices.
- Software tokens: Applications on your smartphone that generate cryptographic signatures
- Platform authenticators: Security features built into your operating system
3. FIDO Protocols: WebAuthn and CTAP
WebAuthn is the Web Authentication API that enables browsers to perform FIDO authentication. It provides a JavaScript interface for websites to request cryptographic credentials from authenticators. WebAuthn is compatible with all major browsers and platforms, ensuring a consistent user experience.
CTAP (Client-to-Authenticator Protocol) enables external authenticators to communicate with your devices. It allows physical security keys to work with computers, smartphones, and tablets. CTAP ensures roaming authenticators function seamlessly across different platforms and applications.
4. The FIDO Server: Verification Hub
The FIDO server manages authentication on the service provider side. It stores user public keys during registration and verifies signatures during login attempts. The server never handles private keys or passwords, thereby eliminating the risk of password database breaches.
Key FIDO Server Functions:
- Registers and stores public keys for each user account
- Generates authentication challenges during login attempts
- Verifies digital signatures against stored public keys
- Manages user accounts and access control policies
These components work together seamlessly to deliver passwordless authentication that's both more secure and easier to use than traditional password systems. Organizations ready to eliminate password-related vulnerabilities can explore different types of passwordless authentication methods to find the best fit for their security requirements.
FIDO Authentication Standards
FIDO has evolved through multiple standards to address different authentication needs. Each standard offers unique capabilities while maintaining passwordless security principles. Understanding these standards helps you select the most suitable approach for your organization.
1. FIDO UAF (Universal Authentication Framework)
FIDO UAF enables passwordless authentication using biometrics and local device credentials through device-based authentication. Users verify identity through fingerprint scans, facial recognition, or PIN codes. Authentication happens entirely on the user's device without sending biometric data to servers.
UAF suits mobile applications and consumer-facing services perfectly. It eliminates passwords from the login process while delivering seamless user experiences. Organizations benefit from strong authentication without managing password databases or reset workflows.
2. FIDO U2F (Universal 2nd Factor)
FIDO U2F adds a second authentication factor using physical security keys. Users tap or insert a hardware token after entering their password. This enhances existing password-based systems without requiring a complete replacement.
U2F security keys are phishing-resistant because they verify service domains cryptographically. Attackers cannot trick users into using keys on fraudulent websites. This makes U2F significantly stronger than SMS-based or app-based codes for multi-factor authentication.
3. FIDO2: The Modern Passwordless Standard
FIDO2 represents the latest evolution, combining WebAuthn and CTAP protocols. It enables fully passwordless authentication across web browsers and platforms. FIDO2 works with both built-in biometrics and external security keys.
Major browsers, including Chrome, Firefox, Safari, and Edge, support FIDO2 natively. Operating systems like Windows, macOS, Android, and iOS have integrated FIDO2 capabilities. This widespread support makes FIDO2 the recommended standard for new implementations.
FIDO2 also supports single-step multi-factor authentication, combining possession and biometrics. Users prove both what they have and who they are in one action. This delivers stronger security with a better experience than traditional login methods.
We have curated a detailed comparison of passwordless vs. traditional logins to make an informed decision.
4. WebAuthn vs. CTAP: Understanding Their Roles
WebAuthn and CTAP serve complementary functions within the FIDO2 framework. Both protocols work together to enable passwordless authentication.
Key Differences Between WebAuthn vs. CTAP
WebAuthn handles communication between websites and authenticators through browser APIs. CTAP enables external security keys to communicate with devices. Together, they create a complete passwordless ecosystem.
Organizations can leverage both protocols simultaneously for comprehensive coverage. Employees use platform authenticators for convenience, while security keys provide an additional layer of security. This flexibility ensures authentication works across all scenarios.
[[cta]]
How Is FIDO Different from Traditional MFA?
Multi-factor authentication (MFA) is a broad term for any authentication method that requires more than one factor—typically something you know (a password), something you have (a security token), and something you are (biometrics).
However, traditional MFA often still relies on shared secrets, which can be intercepted, phished, or stolen.
FIDO can be used as a passwordless, single-factor authentication method or combined with other factors in a multi-factor setup. In both cases, its public-key cryptography provides significantly stronger security than traditional MFA approaches.
How Does FIDO Authentication Work?
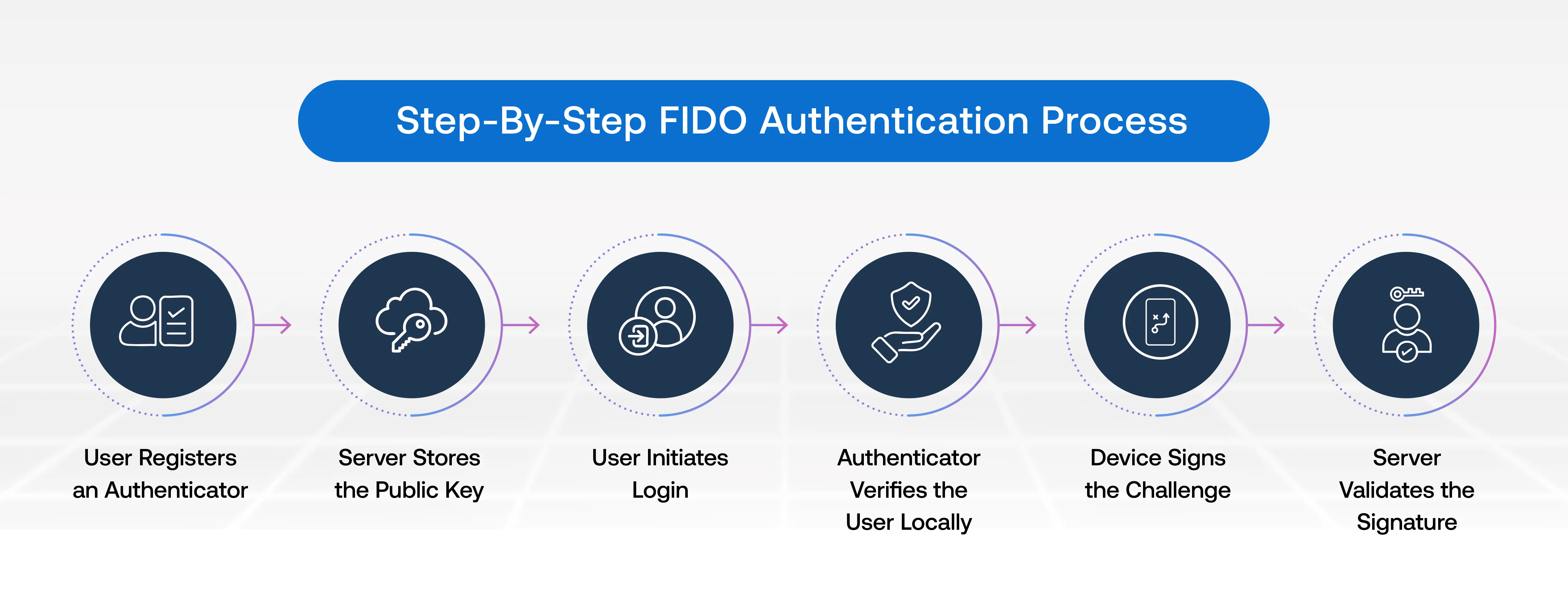
FIDO Authentication replaces passwords with cryptographic keys that securely verify your identity. The authentication flow happens in two phases: registration and login. During registration, your device creates a unique key pair for each service you use. During login, the server challenges your device to prove possession of the private key. Here’s the entire FIDO authentication workflow:
Step 1: User Registers an Authenticator
Registration begins when you create an account with a FIDO-enabled service. Your device generates a unique cryptographic key pair specifically for that service. The private key encrypts and stays locked on your authenticator device permanently. This key pair is mathematically linked but cannot be reverse-engineered from each other.
Key Aspects of Registration
- Each service gets its own unique key pair for enhanced security.
- The private key never leaves your device under any circumstances.
- You can use biometrics, security keys, or platform authenticators.
- No passwords, usernames, or shared secrets are created.
Step 2: Server Stores the Public Key
The server receives and stores your public key along with your account information. This public key acts as your digital identity for that specific service. The server never receives or stores your private key or biometric data. Your public key cannot decrypt anything or authenticate on its own.
What the Server Stores
- Your public key is linked to your account identifier.
- Service-specific credential information without sensitive data.
- No passwords, biometrics, or private keys ever stored.
- A public key alone cannot be used for unauthorized access.
Step 3: User Initiates Login
You start the login process by entering your username on the service. The server recognizes your account and retrieves the public key stored in your account. It then generates a unique cryptographic challenge and sends it to your device. This challenge is a random string that changes with every login attempt.
Login Initiation Process
- User provides a username or account identifier to the service.
- The server generates a unique, time-sensitive cryptographic challenge.
- The challenge is a random string that prevents replay attacks.
- Your device receives the challenge and prepares authentication.
Step 4: Authenticator Verifies the User Locally
Your device prompts you to verify your identity using a local authentication method. You might scan your fingerprint, use facial recognition, or enter a PIN code. This verification happens entirely on your device without sending biometric data anywhere. The authenticator unlocks your private key only after successful local verification has been completed.
Local Verification Methods
- Biometric authentication: fingerprint, facial recognition, or iris scan.
- PIN or password entered directly on your device.
- Physical gestures, such as touchless authentication using contactless technology.
- Multimodal biometric options combining multiple verification factors.
- All verification data stays protected on your device.
Step 5: Device Signs the Challenge
After verifying your identity, your device uses the private key to sign the challenge. This cryptographic signature proves you possess the correct private key without revealing it. The signature is unique to this specific challenge and cannot be reused. Your device creates this digital signature using complex mathematical operations.
Signature Creation Process:
- Private key signs the challenge after local verification succeeds.
- Signature is unique to this login attempt and cannot be replayed.
- Mathematical operations combine challenges with your private key.
- The signed response is sent back to the server for validation.
Step 6: Server Validates the Signature
The server receives your signed challenge and verifies it using the public key stored for you. The cryptographic verification confirms that the signature came from your private key. If the signature matches, the server grants you immediate access to your account. This validation happens in milliseconds without transmitting passwords or secrets.
Validation and Access
- The server uses the public key to verify the signature mathematically
- Successful verification confirms you possess the private key
- Access granted instantly without transmitting any secrets
- Failed attempts don't reveal information about your credentials
5 Noteworthy Benefits of FIDO Authentication
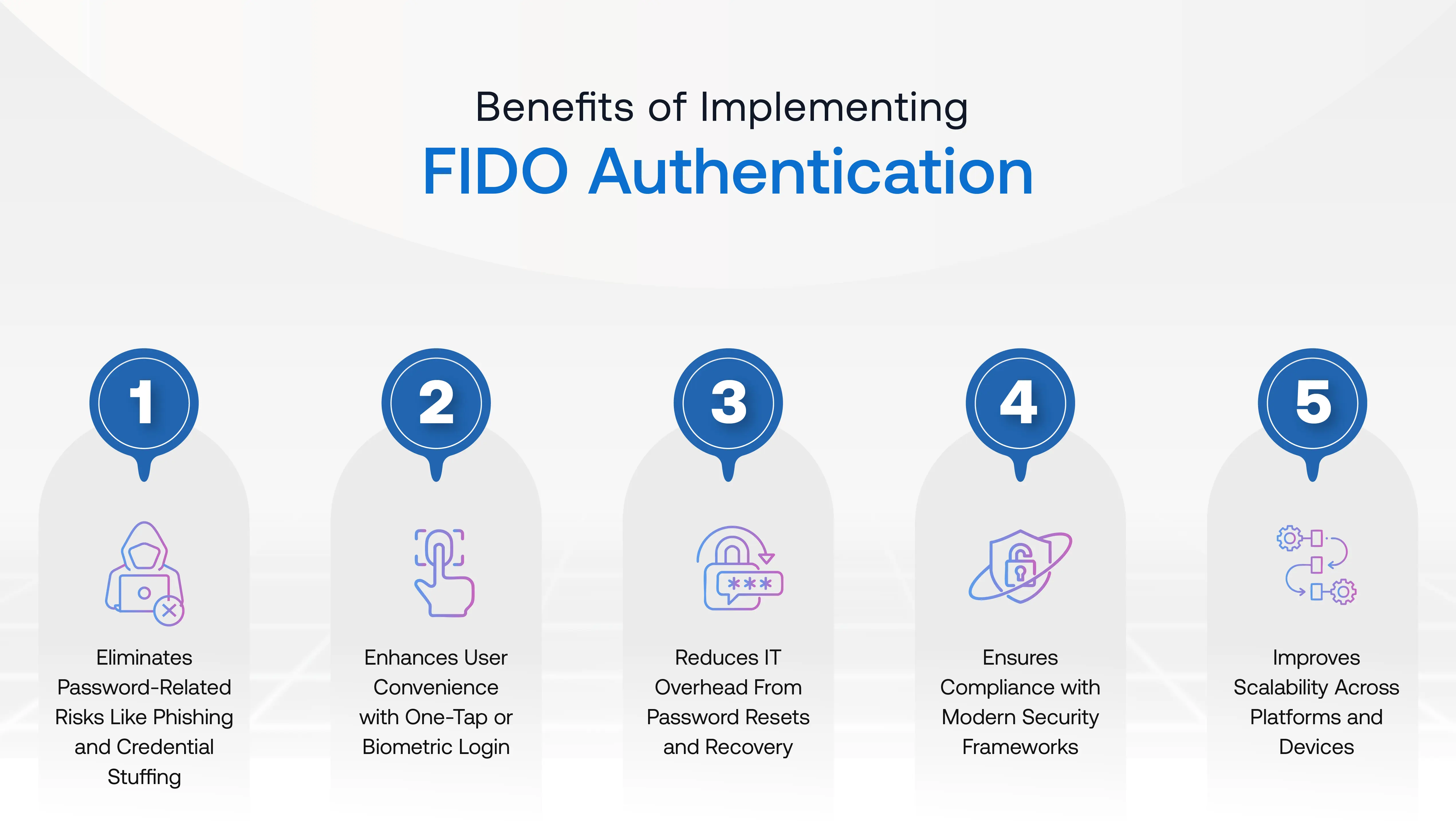
FIDO-based authentication delivers measurable benefits for both organizations and end-users. It eliminates security vulnerabilities inherent in password-based systems while improving user experience. Organizations that adopt FIDO experience reduced operational costs, a stronger compliance posture, and higher user satisfaction.
1. Eliminates Password-Related Risks Like Phishing and Credential Stuffing
FIDO authentication prevents phishing attacks because private keys are never stored on a central server or shared with third parties. Attackers cannot steal credentials that are never transmitted across networks or stored in databases.
The cryptographic binding to specific service domains prevents users from authenticating to fraudulent websites. Each service receives unique cryptographic keys, making credential stuffing attacks impossible.
2. Enhances User Convenience with One-Tap or Biometric Login
Users authenticate with simple gestures, such as fingerprint scans or facial recognition. Login happens in seconds without requiring the recall of complex passwords or the typing of lengthy character strings.
This convenience significantly increases login success rates and user satisfaction. The seamless experience works uniformly across desktop, mobile, and tablet devices.
3. Reduces IT Overhead From Password Resets and Recovery
Organizations eliminate the massive burden of password reset requests, consuming IT helpdesk resources. FIDO removes passwords entirely, so there's nothing to reset or manage anymore. IT teams redirect time from password management to strategic security initiatives. Organizations save money on both direct support costs and employee productivity losses.
4. Ensures Compliance with Modern Security Frameworks
FIDO authentication aligns with major regulatory requirements and global security standards. Standards like NIST, PCI DSS, GDPR, and HIPAA increasingly recommend phishing-resistant authentication. Organizations that use FIDO simplify their audit processes and demonstrate best security practices.
The cryptographic foundation meets the technical requirements for data protection regulations.
5. Improves Scalability Across Platforms and Devices
FIDO works universally across web browsers, mobile apps, and enterprise systems. Users authenticate in the same way, regardless of the device or platform they choose. Organizations deploy once and support authentication everywhere, eliminating the need for platform-specific customization. This scalability extends to organizational growth without authentication bottlenecks.
These combined benefits make FIDO authentication the superior choice for modern enterprises. With these benefits in mind, let’s look at how organizations across industries are putting FIDO Authentication into practice.
[[cta-2]]
FIDO and Biometrics
FIDO authentication often uses biometrics for local user verification. These biometrics fall into two main categories:
Biological Biometrics
- Fingerprint scanning
- Facial recognition
- Retina or iris scanning
- Voice recognition
- Vein pattern recognition
Behavioral Biometrics
- Typing patterns and speed
- Mouse movement characteristics
- Touchscreen gesture patterns
- Gait analysis (on mobile devices)
Important Considerations
While biometrics enable fast and convenient authentication, they also have certain limitations:
- Spoofing risks: Advanced attackers may attempt to bypass biometrics using photos, silicone fingerprints, or synthetic voice recordings
- Accuracy variations: Environmental factors such as lighting, moisture, or injuries can impact recognition
- Bias concerns: Some biometric systems show varying accuracy across different demographic groups
- Immutability: Unlike passwords, biometric traits cannot be changed if they are compromised
FIDO reduces these risks by using biometrics only for local verification. Biometric data never leaves the device and is not transmitted to servers. Even if a biometric were spoofed, an attacker would still need physical access to the user’s registered device to authenticate.
Common Use Cases of FIDO Authentication
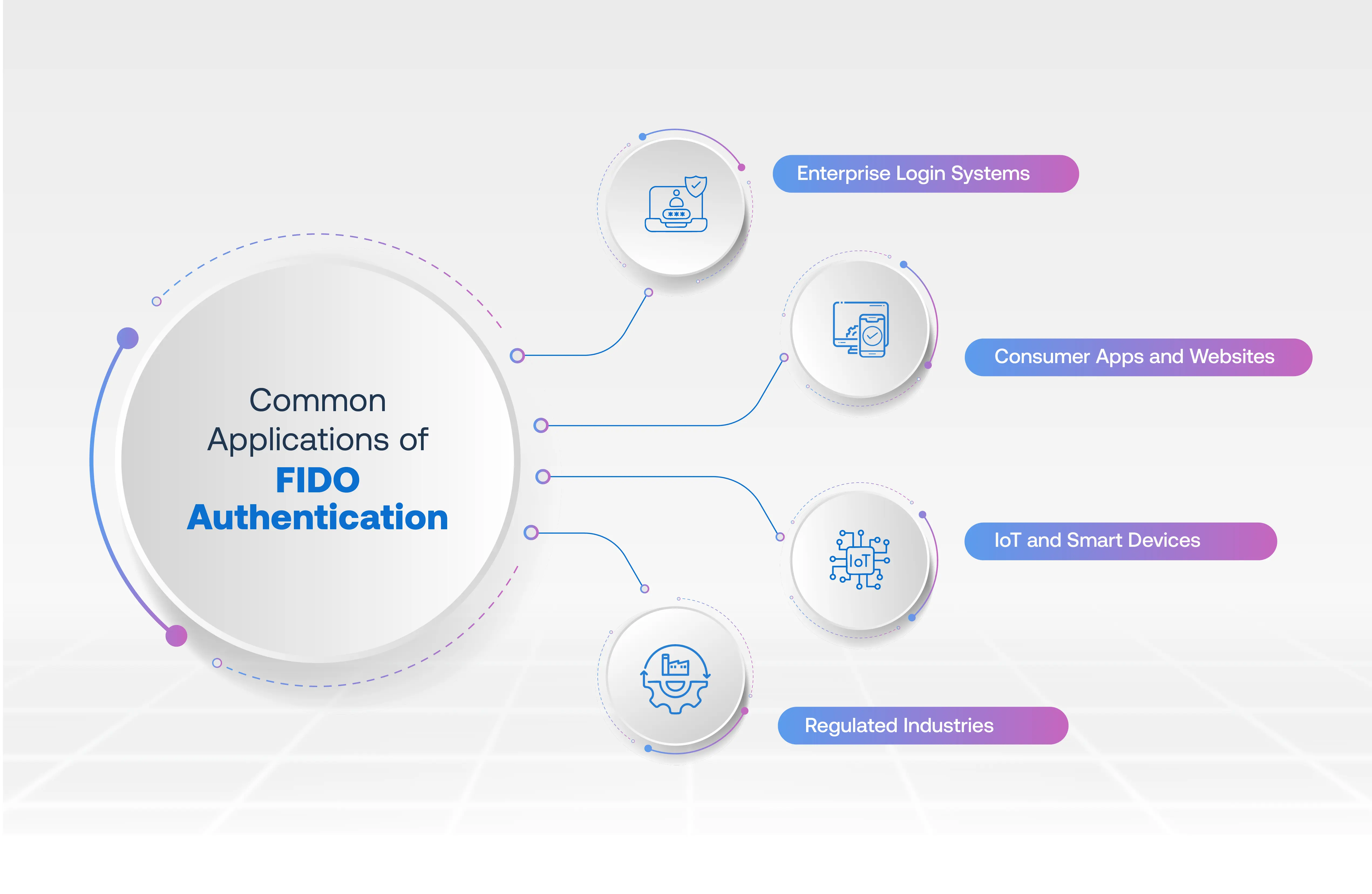
FIDO Authentication solves real-world security challenges across diverse industries and applications. Organizations implement FIDO to protect sensitive data while simplifying user access and authentication.
1. Enterprise Login Systems
Enterprises deploy FIDO to secure employee access to corporate applications and resources. Workers authenticate themselves using biometrics or security keys, eliminating the need to remember multiple passwords.
This eliminates password fatigue while strengthening security across the entire organization. IT administrators gain centralized control over authentication policies without having to manage password complexity requirements.
2. Consumer Apps and Websites
Banks utilize FIDO to safeguard customer accounts against credential theft and account takeover. Retail platforms implement passwordless login to reduce cart abandonment and enhance checkout conversion rates.
Healthcare providers secure patient portals with FIDO while maintaining HIPAA compliance standards. Consumers enjoy faster, safer access to their accounts without the hassle of passwords.
3. IoT and Smart Devices
Smart home devices use FIDO protocols to establish secure connections with user smartphones. IoT manufacturers eliminate hardcoded default passwords that create security vulnerabilities in connected devices.
Device pairing happens seamlessly using cryptographic authentication instead of shared secrets. This approach prevents unauthorized access to smart devices and protects user privacy.
4. Regulated Industries
Financial institutions adopt FIDO to meet stringent authentication requirements from regulatory bodies. Government agencies implement passwordless access to protect classified information and citizen data.
Healthcare organizations utilize FIDO to fulfill security mandates while safeguarding electronic health records. These industries benefit from FIDO's alignment with compliance frameworks and audit requirements.
FIDO authentication adapts seamlessly to any industry or application requiring strong security. Organizations across sectors leverage FIDO to protect users while improving operational efficiency. Understanding the key use cases is the first step—next comes putting FIDO Authentication into action through a structured implementation process.
How to Implement FIDO Authentication: Step-By-Step Process
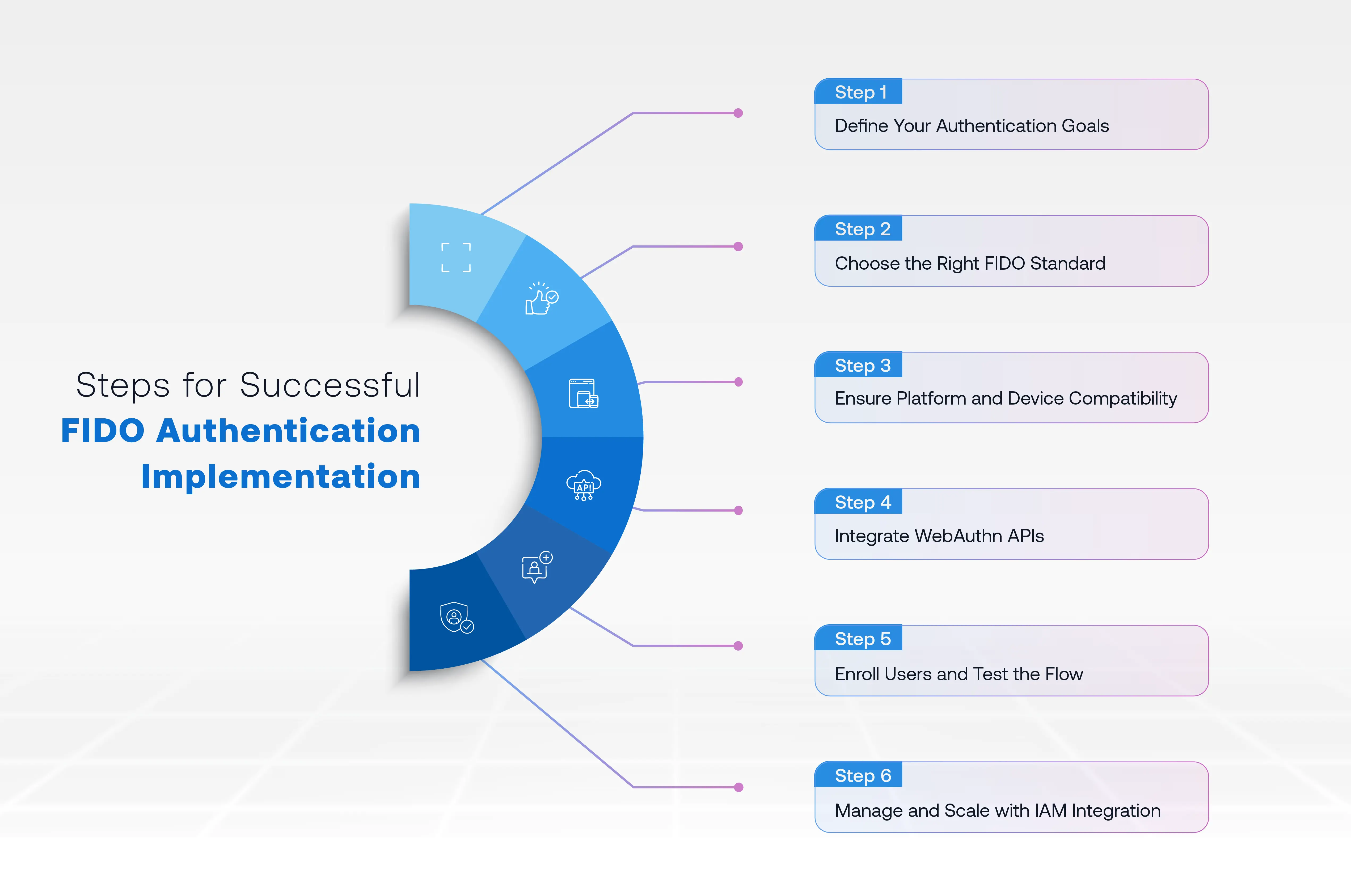
Implementing FIDO Authentication requires careful planning and systematic execution across technical and user layers. Following a structured approach ensures successful deployment while minimizing disruption to existing workflows.
Step 1: Define Your Authentication Goals
- Identify where you want to deploy FIDO across your organization: workforce apps, customer platforms, or both.
- Assess current authentication challenges like password reset volume, phishing incidents, and compliance gaps.
- Decide whether you're replacing passwords entirely or enhancing existing multi-factor authentication systems.
Step 2: Choose the Right FIDO Standard
- Select FIDO2 for complete passwordless authentication or U2F for strong second-factor verification.
- FIDO2 offers the most modern capabilities, supporting the WebAuthn and CTAP protocols.
- Your choice depends on organizational readiness, user experience goals, and security requirements.
Step 3: Ensure Platform and Device Compatibility
- Verify that your target browsers, operating systems, and devices support FIDO standards natively.
- Verify that authenticators, such as biometric readers and security keys, function seamlessly across all platforms.
- Thoroughly test compatibility to prevent deployment issues and ensure a seamless experience.
- OLOID’s passwordless authentication platform simplifies compatibility management across devices and applications, ensuring secure, passwordless authentication at scale.
Step 4: Integrate WebAuthn APIs
- Implement FIDO authentication using WebAuthn APIs in your web or mobile applications.
- Configure your authentication server to securely handle credential creation and verification requests.
- Test the integration across different browsers, devices, and network conditions.
Step 5: Enroll Users and Test the Flow
- Allow users to register their authenticators through transparent, self-service enrollment processes.
- Provide step-by-step instructions guiding users through credential registration.
- Test end-to-end authentication scenarios and verify backup methods work correctly.
Step 6: Manage and Scale with IAM Integration
- Integrate FIDO with your identity and access management system for centralized control.
- Configure authentication policies, user groups, and credential lifecycle management procedures.
Successful FIDO implementation transforms your security posture while enhancing user satisfaction. However, while implementing FIDO Authentication can transform security and user experience, it’s important to be aware of potential challenges along the way. Let’s explore the most common challenges in adopting FIDO for authentication.
[[cta-3]]
Challenges and Considerations In Implementing Fast Identity Online (FIDO)

Organizations face several practical challenges when adopting FIDO Authentication despite its clear benefits. Understanding these obstacles and their solutions ensures smoother implementation and higher adoption rates.
1. Device and Browser Compatibility
Problem Statement
Not all devices and browsers support FIDO standards equally or consistently. Legacy systems and older hardware may lack the necessary cryptographic capabilities for FIDO authentication.
Solution
- Conduct compatibility audits across all devices and browsers before deployment.
- Implement temporary fallback authentication methods for unsupported platforms.
- Upgrade or replace legacy systems that cannot support FIDO standards.
- Test thoroughly across different operating system versions and browsers.
2. User Onboarding and Change Management
Problem Statement
Users accustomed to passwords may resist changing to new authentication methods. Training employees or customers on FIDO authenticators requires significant resources and planning.
Solution
- Develop clear enrollment guides with visual instructions and videos.
- Implement a phased rollout, starting with early adopters first.
- Provide dedicated support channels during transition periods to ensure seamless continuity of service.
- Offer multiple authenticator options so users can choose preferred methods.
3. Managing Legacy Systems and Hybrid Environments
Problem Statement
Many organizations run legacy applications that cannot integrate with modern FIDO protocols. Hybrid environments mixing old and new systems create authentication complexity for users.
Solution
- Deploy identity bridges that translate FIDO authentication to legacy protocols.
- Implement Single Sign-On solutions handling authentication differences transparently.
- Create phased migration plans prioritizing critical applications first.
- Utilize IAM platforms that support both modern and legacy authentication methods.
4. Regulatory or Compliance Mapping
Problem Statement
Organizations must verify that FIDO implementation meets specific industry regulations and standards. Different compliance frameworks have varying authentication requirements that need careful mapping.
Solution
- Map FIDO capabilities to specific compliance requirements like NIST and PCI DSS.
- Work with compliance officers to document how FIDO satisfies regulatory mandates.
- Implement comprehensive logging and audit trails for authentication events to ensure accurate tracking and accountability.
- Engage security auditors early to validate FIDO implementation meets standards.
Addressing these challenges proactively ensures successful FIDO Authentication deployment at scale. Organizations that plan carefully achieve passwordless security while maintaining compliance and user satisfaction.
Summing It Up
FIDO Authentication fundamentally transforms digital identity security by eliminating password vulnerabilities through cryptographic verification. Organizations gain phishing-resistant protection that works seamlessly across all platforms and devices. This shift from shared secrets to cryptographic keys represents the future of enterprise authentication.
The dual benefit of enhanced security and improved user experience makes FIDO uniquely valuable. Users authenticate instantly with biometrics or security keys without password frustration. Organizations strengthen security while reducing IT overhead and operational costs simultaneously.
Now is the time to transition your organization to passwordless authentication. OLOID integrates physical identity infrastructure with FIDO standards for seamless enterprise deployment. Book a demo today to discover how OLOID delivers FIDO Authentication tailored to your security requirements.
Frequently Asked Questions on FIDO-Based Authentication
1. How secure is FIDO authentication compared to traditional passwords?
FIDO authentication is far more secure than passwords because it uses public-key cryptography instead of shared secrets. Private keys are never stored on the user’s device and cannot be stolen or reused. Each login is verified with a unique cryptographic challenge, making phishing, credential stuffing, and brute-force attacks ineffective.
2. Is FIDO the same as passwordless authentication?
FIDO is the foundation for passwordless authentication. It enables users to log in using secure methods such as biometrics (fingerprint, facial recognition) or device PINs, without ever entering a password. While all FIDO logins are passwordless, not all passwordless systems meet FIDO’s phishing-resistant standards.
3. Why Is FIDO Authentication Phishing-Resistant?
FIDO Authentication is phishing-resistant because it uses public-key cryptography instead of passwords. The private key stays securely on your device and is tied only to the legitimate website. When you log in, your device signs a challenge sent by the server using this key, after verifying the site’s domain. Since the authenticator won’t respond to fake or spoofed sites, phishing attacks and credential theft become ineffective.
4. What is FIDO2, and how is it different from FIDO U2F?
FIDO2 is the latest standard from the FIDO Alliance, combining the W3C WebAuthn API and the FIDO Client to Authenticator Protocol (CTAP). It allows full passwordless login experiences across browsers and devices. In contrast, FIDO U2F (Universal 2nd Factor) is designed for two-factor authentication only. It supplements passwords rather than replacing them.
5. Can small businesses implement FIDO authentication easily?
Yes. FIDO authentication can be implemented with minimal infrastructure changes. Many modern devices and browsers already support FIDO2 standards, making adoption simple and cost-effective. Platforms like OLOID help small and mid-sized businesses integrate phishing-resistant MFA and passwordless access without disrupting existing workflows.



Get the latest updates! Subscribe now!



