What Is Risk-Based Authentication? Benefits, Use Cases & How It Works
Risk-based authentication evaluates threat indicators and user behavior patterns before enforcing authentication requirements. Traditional static authentication applies the same verification regardless of the actual risk levels. This guide explains how risk-based systems calculate scores, analyze signals, and make dynamic decisions. Learn implementation strategies, regulatory compliance requirements, and best practices for deploying intelligent, risk-aware authentication.
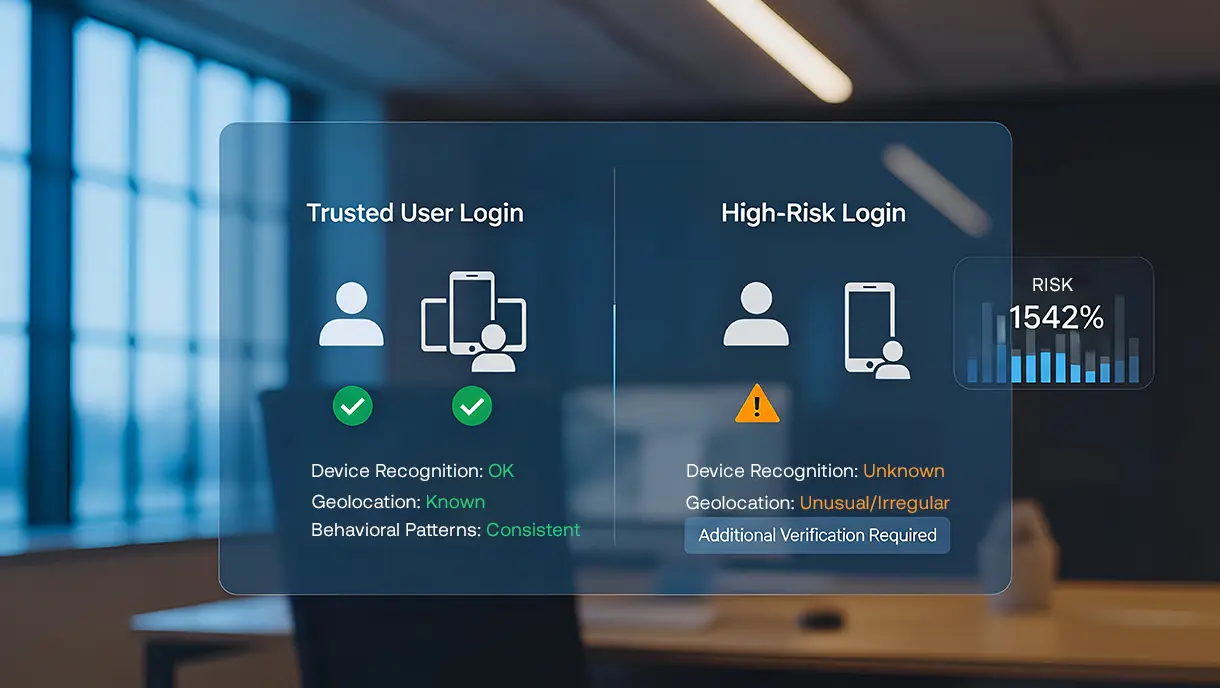
Identity is now the primary attack surface for modern organizations. As passwords, static multi-factor authentication, and one-size-fits-all access controls struggle to keep up with evolving threats, security teams are being forced to rethink how authentication decisions are made.
Granting the same level of access in every situation no longer reflects the real-world risk behind each login attempt.
This is where risk-based authentication comes in. Instead of treating every user and every login the same, risk-based authentication evaluates contextual signals like device trust, location, behavior, and access patterns in real time to decide how much authentication is actually needed.
In this guide, we break down what risk-based authentication is, how it works, and why it has become a critical part of modern identity and access security. Learn where traditional authentication models fall short, common use cases across industries, and how organizations are combining risk-based and passwordless approaches to improve both security and user experience.
What Is Risk-Based Authentication (RBA)?
Risk-based authentication, often referred to as RBA, is an authentication approach that adjusts access requirements based on the level of risk associated with each login attempt. Instead of applying the same authentication steps to every user and every session, RBA evaluates contextual and behavioral signals in real time to determine whether access should be granted seamlessly, challenged with additional verification, or denied altogether.
At its core, risk-based authentication recognizes that not all access attempts carry the same level of risk. A trusted employee logging in from a known device and location during regular working hours presents far less risk than an unusual login from an unknown device, unfamiliar location, or abnormal behavior pattern. RBA uses this context to make smarter, more proportionate authentication decisions.
This intelligent approach differs fundamentally from static authentication, applying fixed requirements regardless of circumstances. Risk-based systems answer critical questions about each authentication attempt:
- Does this access pattern match normal behavior?
- Are there suspicious indicators suggesting credential theft?
- Should additional verification be required, given current risk factors?
These assessments enable security proportional to actual threats.
How Risk-Based Authentication Works
Risk-based authentication follows systematic processes from initial access attempts through continuous monitoring. Understanding these workflows helps organizations implement adequate risk-aware security.
Step 1: Signal Collection (IP reputation, device data, user behavior, transaction context)
The system collects comprehensive signals during authentication attempts, including IP addresses, device fingerprints, geolocation coordinates, and behavioral patterns. Transaction details, resource sensitivity, and historical access patterns provide additional context. This multi-dimensional data collection enables accurate risk assessment across diverse threat indicators and user characteristics.
Step 2: Risk Analysis (anomaly detection + historical patterns)
The platform compares collected signals against established user baselines and organizational norms to identify behavioral deviations. Anomaly detection algorithms flag unusual access patterns, impossible travel scenarios, and suspicious device characteristics. Historical pattern analysis reveals whether current behavior matches legitimate user activities or indicates potential compromise or fraud.
Step 3: Risk Scoring (low, medium, high)
The risk engine combines analyzed signals using weighted algorithms, generating numerical scores that represent overall threat levels. Machine learning models identify subtle attack patterns while rule-based logic enforces explicit security requirements. Scores typically range from low-risk, routine access, to medium-risk requiring attention, to high-risk, suspicious attempts demanding immediate action.
Step 4: Policy Engine Decision (allow, MFA, block)
The system evaluates calculated risk scores against configured policies to determine appropriate authentication requirements and access decisions. Low scores enable seamless access without additional verification, while medium scores trigger step-up authentication. High-risk scores may block access entirely or require manual review by the security team, ensuring protection against identified threats.
Step 5: Continuous Session Monitoring (token misuse, lateral movement)
Platform monitors active sessions continuously, reassessing risk as user behavior and context change throughout the session. Behavioral shifts, attempts to escalate privilege, or unusual resource access patterns trigger reauthentication requirements. This continuous evaluation extends protection beyond initial login, preventing session hijacking and insider threats from causing damage.
Risk-based authentication continuously evaluates access attempts and adjusts authentication requirements based on calculated risk levels, ensuring security without unnecessary friction. To understand how these risk decisions are made, it’s important to look at the core signals RBA systems analyze when assessing each login attempt.
[[cta]]
Core Risk Signals Used in Risk-Based Authentication
Risk-based authentication analyzes diverse signal categories to produce comprehensive threat assessments. Understanding these signals helps organizations configure effective policies.
1. User & Behavioral Signals
Typing patterns, mouse movements, navigation sequences, and interaction styles create unique behavioral fingerprints. Login frequency, typical access times, and session duration patterns establish individual baselines. Behavioral deviations indicate potential account takeover or credential misuse. User-specific signals provide robust verification without requiring explicit user actions.
2. Device & Technical Signals
Device fingerprints, operating system versions, browser characteristics, and installed software identify endpoints. Security patch levels, endpoint protection status, and device health assessments reveal compromise risks. Unrecognized devices warrant additional verification while trusted endpoints enable streamlined authentication. Technical signals ensure access happens from secure platforms.
3. Network & Location Signals
IP addresses, geolocation coordinates, network types, and connection characteristics inform risk decisions. Impossible travel patterns reveal credential theft across geographic distances. Known malicious IPs, anonymization services, and suspicious network behaviors trigger immediate responses. Location consistency provides strong indicators of legitimate versus fraudulent access attempts.
4. Transaction Signals
Transaction amounts, recipient details, frequency patterns, and historical behaviors influence risk scoring. Significant or unusual transactions are subject to heightened scrutiny to prevent fraud. Sequential transaction patterns may indicate automated attacks or account compromise. Transaction-level risk assessment protects specific activities beyond basic authentication verification.
By analyzing device, location, behavior, and access context, risk-based authentication can accurately gauge the likelihood of legitimate or malicious activity, setting the stage for its key benefits in improving security, reducing friction, and enhancing user experience across organizations.
Benefits of Risk-Based Authentication
Risk-based authentication delivers measurable security and operational improvements across organizations. These advantages justify the investment in implementation and the associated complexity.
1. Significantly Reduces Fraud and ATO Attempts
Risk-based systems detect credential theft and account takeover through behavioral anomalies and contextual inconsistencies. Attackers using stolen credentials face additional verification that they cannot complete. Real-time risk assessment identifies fraud patterns that static authentication misses entirely.
2. Applies MFA Only When Necessary (Less Friction)
Trusted users accessing from normal contexts experience seamless authentication without unnecessary challenges. Additional verification occurs only when risk indicators warrant heightened security. Selective MFA enforcement significantly optimizes the balance between protection and user experience.
3. Adapts in Real Time as User Behavior Changes
Risk scoring updates continuously as new signals become available throughout authentication processes. Systems respond immediately to emerging threats without requiring manual intervention from the security team. Adaptive responses ensure that protection dynamically matches actual risk levels.
4. Protects Transactions, Not Just Logins
Risk-based authentication evaluates individual transactions and actions beyond initial access verification. High-value operations receive appropriate scrutiny, to prevent fraud after successful authentication. Transaction-level protection addresses threats that login-only security cannot control.
5. Supports Zero Trust with Continuous Risk Evaluation
Risk-based approaches align perfectly with Zero-Trust principles, requiring ongoing identity verification. Every access attempt receives an individual risk assessment regardless of previous authentication success. Continuous evaluation effectively implements the "never trust, always verify" mandate.
6. Improves SOC Visibility with Detailed Risk Logs
Comprehensive risk scoring generates detailed logs providing security teams with actionable intelligence. Anomaly patterns reveal emerging attack techniques and threat actor behaviors. Enhanced visibility enables proactive threat hunting and incident investigation, improving overall security posture.
Risk-based authentication delivers stronger security, smoother user experiences, and better alignment with zero-trust architecture principles, making it a practical solution for modern access challenges. These advantages become even clearer when we explore how RBA is applied across different industries and real-world scenarios.
[[cta-2]]
Industry-Specific Use Cases of Risk-Based Authentication
Organizations across industries deploy risk-based authentication to address sector-specific fraud patterns and regulatory requirements. These use cases demonstrate practical applications.
1. Banking & Fintech
Financial institutions face sophisticated fraud targeting high-value transactions and account takeovers. Risk-based authentication evaluates transaction amounts, beneficiary details, and historical patterns to prevent unauthorized transfers.
Regulatory requirements, such as PSD2, mandate risk-based exemptions to enable frictionless payments. Banks reduce fraud losses while maintaining customer experience through intelligent risk assessment.
2. E-Commerce & Consumer Apps
Online retailers combat account takeover, payment fraud, and credential stuffing attacks. Risk-based systems detect unusual purchasing patterns, shipping address changes, and changes in payment methods.
Legitimate customers experience seamless checkout while suspicious activities trigger additional verification. E-commerce platforms balance conversion rates with fraud prevention through adaptive security.
3. SaaS & Enterprise IAM
Cloud application providers protect customer data and prevent unauthorized access across distributed workforces. Risk-based authentication evaluates device trust, location patterns, and access behaviors.
Privileged account activities are subject to heightened scrutiny to prevent insider threats. IAM platforms enforce appropriate security without impeding productivity.
4. Healthcare
Healthcare organizations protect electronic health records and comply with HIPAA requirements. Risk-based authentication ensures appropriate verification based on data sensitivity and access context. Clinical workflows benefit from reduced friction during routine access. Patient privacy receives enhanced protection through intelligent risk assessment.
5. Workforce & Zero Trust Implementations
Enterprises adopting Zero Trust architectures require continuous risk evaluation throughout user sessions. Risk-based authentication provides identity assurance necessary for micro-segmentation and least-privilege access. Remote workers receive appropriate security based on network conditions and device health. Zero Trust implementations rely on risk-based intelligence for effective operation.
These industry-specific examples show how risk-based authentication adapts to diverse environments and access needs, providing both security and usability, and understanding these use cases lays the groundwork for a practical guide on implementing RBA effectively in your organization.
Implementing Risk-Based Authentication: A Practical Technical Guide
Successful implementation requires structured approaches addressing technical architecture and operational considerations. This roadmap guides risk-based authentication deployment.
1. Identify High-Risk Applications & Users
Prioritize risk-based authentication for applications handling financial transactions, sensitive data, or privileged operations. Focus initial deployment where fraud prevention delivers maximum value. The assessment identifies implementation priorities and the expected return on investment.
2. Select Risk Signals Relevant to Your Environment
Choose signals matching your threat profile, user populations, and technical infrastructure. Consider data availability and collection capabilities. Balance signal richness with privacy requirements and regulatory constraints affecting your industry.
3. Choose a Risk Engine (ML-Based or Policy-Based)
Evaluate whether machine learning or rule-based risk scoring better matches organizational needs. ML engines provide sophisticated pattern detection but require training data. Policy-based systems offer faster deployment with explicit control. Many organizations use hybrid approaches combining both technologies.
4. Define Risk Threshold Policies
Establish risk score ranges triggering different authentication requirements and security responses. Configure policies for low-risk seamless access, medium-risk step-up verification, and high-risk blocking. Test thresholds against historical data to validate appropriate sensitivity levels.
5. Integrate RBA With IAM/SSO/MFA Platforms
Connect risk-based authentication to existing identity infrastructure to enable unified security policies. Integration provides consistent experiences across applications while leveraging current investments. API-based architectures enable flexible deployment across diverse technology stacks.
6. Build Real-Time Monitoring & Alerting
Implement dashboards displaying risk scores, authentication patterns, and security incidents. Configure alerts notifying security teams about high-risk access attempts or emerging threats. Real-time visibility enables rapid response to sophisticated attacks.
7. Test & Tune With Live Traffic Data
Begin with shadow mode, observing risk scores without enforcing policies. Analyze false positives and false negatives, adjusting thresholds appropriately. Gradual rollout allows policy refinement before full enforcement, minimizing user disruption.
Successfully implementing risk-based authentication ensures adaptive, context-aware security that balances protection and user convenience, and once in place, it also plays a critical role in meeting regulatory requirements and compliance standards.
[[cta-3]]
Regulatory & Compliance Relevance of RBA
Risk-based authentication addresses regulatory requirements across financial services, healthcare, and enterprise security. Understanding compliance drivers justifies implementation investments.
1. PSD2 SCA (Risk-Based Exemptions)
European Payment Services Directive mandates Strong Customer Authentication for electronic payments. Risk-based exemptions enable frictionless transactions when risk assessments indicate low risk. Financial institutions implement risk engines that calculate transaction risk, enabling regulatory-compliant payment flows.
2. PCI-DSS v4.0 Authentication Guidance
Payment Card Industry standards require risk-based authentication for administrative access to cardholder environments. Version 4.0 emphasizes context-aware authentication and continuous monitoring. Organizations processing payment cards must implement risk assessment capabilities.
3. FFIEC Guidelines for Banking
Federal Financial Institutions Examination Council guidance recommends risk-based authentication for online banking. Institutions should evaluate transaction risk, customer behavior, and device characteristics. Compliance requires documented risk assessment methodologies and ongoing monitoring.
4. NIST 800-63 Standards for Login Risk
National Institute of Standards and Technology guidelines describe risk-based authentication within digital identity frameworks. NIST recommends continuous evaluation and adaptive security responses. Federal agencies and contractors implement risk-based approaches meeting these standards.
By aligning authentication practices with regulatory and compliance standards, risk-based authentication not only strengthens security but also helps organizations avoid penalties, and understanding these requirements highlights the common challenges that must be addressed for successful RBA deployment.
Common Challenges & How to Address Them
Organizations encounter predictable obstacles in deploying risk-based authentication. Understanding these challenges enables proactive mitigation strategies.
1. False Positives Due to Noisy Signals
Unreliable signals generate false alarms, frustrating legitimate users with unnecessary verification challenges. Poor signal quality undermines the accuracy of risk assessment, reducing system effectiveness. Organizations must validate signal reliability before deployment.
How to Overcome This Challenge
- Test signals against historical data to identify unreliable indicators before production use.
- Implement signal quality monitoring to detect data-collection failures that affect risk accuracy.
- Weight signals appropriately based on demonstrated reliability and predictive value.
- Use ensemble methods combining multiple signals, reducing the impact of individual failures.
2. Balancing Friction vs. Security
Overly sensitive risk scoring triggers excessive verification, frustrating users and reducing productivity. Insufficient sensitivity leaves security gaps enabling fraud and unauthorized access. Organizations struggle to find optimal balance points.
How to Overcome This Challenge
- Start with conservative thresholds allowing gradual tightening based on observed threats.
- Monitor user feedback and abandonment rates, identifying friction points requiring adjustment.
- Provide multiple-step-up authentication options that accommodate user preferences and capabilities.
- Segment policies by user type and application sensitivity, enabling targeted security levels.
3. Integrating with Legacy IAM Systems
Older identity infrastructure may lack APIs or extensibility points for risk engine integration. Legacy applications cannot provide the contextual signals modern risk assessment requires. Integration complexity delays deployment and increases costs.
How to Overcome This Challenge
- Deploy authentication proxies intercepting legacy authentication flows for risk assessment.
- Use agent-based signal collection to gather context from endpoints running legacy software.
- Implement parallel risk assessment for legacy systems without modifying application code.
- Prioritize modernizing applications, protecting the most sensitive resources, and the highest fraud risk.
4. Training ML Models with Insufficient Data
Machine learning requires substantial training data, the establishment of behavioral baselines, and the detection of anomalies. New deployments lack the historical data necessary for accurate model training. Insufficient data produces unreliable risk scores.
How to Overcome This Challenge
- Begin with rule-based risk assessment during initial deployment while collecting training data.
- Use transfer learning by applying models trained on similar populations to bootstrap accuracy.
- Implement hybrid approaches combining rules with ML as training data accumulates over time.
- Partner with vendors providing pre-trained models based on aggregated cross-customer intelligence.
5. User Privacy Concerns Regarding Behavioral Tracking
Behavioral analytics and contextual monitoring raise privacy concerns among users and regulators. Data collection practices may conflict with privacy regulations like GDPR. Organizations must balance security needs with privacy requirements.
How to Overcome This Challenge
- Implement transparent policies explaining what behavioral data is collected and why.
- Provide user controls and consent mechanisms where required or expected by law.
- Minimize data retention, keeping only information necessary for risk assessment purposes.
- Conduct privacy impact assessments to ensure regulatory compliance before deployment.
Addressing common challenges in risk-based authentication helps organizations minimize false positives, integration issues, and user friction, paving the way to implement best practices that ensure high-accuracy, reliable, and effective RBA.
Best Practices for High-Accuracy Risk-Based Authentication
Following proven practices ensures risk-based authentication delivers security benefits without excessive friction. These guidelines address common implementation pitfalls.
1. Start with High-Confidence Signals (IP Reputation, Device Fingerprint)
Prioritize signals that provide maximum predictive value with minimal collection complexity. IP reputation and device fingerprints deliver strong fraud detection. Focus on reliable indicators before adding marginal signals, as this increases system complexity.
2. Use a Hybrid Model (Rules + ML)
Combine explicit rule-based policies with machine learning pattern detection. Rules enforce known security requirements while ML identifies emerging threats. Hybrid approaches provide immediate value while improving continuously through learning.
3. Avoid Over-Triggering MFA
Excessive step-up authentication frustrates users and reduces productivity without proportional security improvements. Monitor MFA trigger rates to ensure challenges occur only when genuinely warranted. Balance security with user experience, maintaining acceptable friction levels.
4. Continuously Refine Thresholds
Risk scoring accuracy improves through ongoing threshold tuning based on observed outcomes. Analyze false positives and false negatives and adjust policies accordingly. Regular refinement adapts systems to evolving threats and changing user behaviors.
5. Monitor Transaction-Level Risk
Extend risk assessment beyond initial login to individual transactions and sensitive operations. High-value actions warrant additional scrutiny to prevent fraud after successful authentication. Transaction monitoring provides comprehensive protection throughout user sessions.
6. Ensure Transparency & Compliance with User Data Laws
Communicate clearly what data is collected and how risk assessment protects users. Provide privacy controls where required by regulations or user expectations. Maintain compliance with GDPR, CCPA, and industry-specific privacy requirements.
Final Thoughts: Risk-Based Authentication
Risk-based authentication offers a modern approach to securing access by evaluating each login attempt based on real-time risk factors, ensuring that security measures are proportional to the actual threat.
By leveraging contextual signals like device, location, and user behavior, organizations can reduce reliance on static credentials, prevent identity-based attacks, and minimize friction for legitimate users.
As digital environments grow more complex and distributed, adopting RBA enables businesses to protect sensitive systems, enhance user experience, and maintain compliance, making it an essential component of a resilient and adaptive authentication strategy.
FAQs on Risk-Based Authentication
1. Is risk-based authentication accurate enough for high-risk environments like banking?
Risk-based authentication provides sufficient accuracy for banking and financial services when properly implemented. Modern systems combine multiple signals and machine learning to achieve fraud detection rates exceeding 95%.
Banks worldwide use risk-based approaches to meet regulatory requirements and prevent billions in fraud losses. However, accuracy depends on signal quality, model training, and continuous tuning. Organizations should validate performance against their specific fraud patterns before full deployment.
2. Can RBA work without machine learning?
Risk-based authentication can operate using rule-based policies without machine learning algorithms. Organizations define explicit risk scoring rules based on signal combinations and thresholds. Rule-based systems provide faster deployment and easier explainability for compliance purposes.
However, ML-based approaches detect sophisticated fraud patterns that rules cannot identify. Most effective implementations use hybrid models that combine rules with machine learning to achieve optimal accuracy.
3. Does RBA replace MFA or work alongside it?
Risk-based authentication enhances rather than replaces multi-factor authentication capabilities. RBA determines when additional verification factors are necessary based on calculated risk. Low-risk scenarios may allow password-only access while high-risk attempts require multiple factors.
The technologies work together with risk assessment to decide MFA enforcement policies. Organizations achieve stronger security with less user friction through an intelligent combination.
4. How long does it take to train a reliable risk engine?
Risk engine training duration depends on data volume, user population size, and fraud prevalence. Organizations typically need 30-90 days of historical data to establish behavioral baselines.
Active learning improves accuracy continuously as systems process more authentication attempts. Pre-trained models from vendors provide immediate value while organization-specific training occurs. Most implementations achieve acceptable accuracy within 60 days with ongoing refinement thereafter.
.webp)


Get the latest updates! Subscribe now!



