
About
Rahul Mathew is the Head of Marketing at OLOID, where he leads global marketing initiatives focused on brand strategy, digital transformation, and customer engagement. With over a decade of experience in technology-driven companies, Rahul drives innovation at the intersection of identity, security, and automation—helping organizations streamline access and workplace experiences through AI-powered solutions. His leadership combines creative vision with data-driven execution to accelerate growth and brand recognition.
Usually writes about
RFID Badge Login
QR Code Login
Palm Authentication
NFC Authentication
Face Authentication
Continuous Authentication
Contact Center
Use Case - Presence Detection
Use Case - Shared Device Access
Use Case - Phising Resistant MFA
Use Case - Shared Login
Use Case - Passwordless SSPR
Use Case - Login to SSO
Pharmaceutical
Healthcare
Retail
Manufactoring
No items found.
No items found.
No items found.
No items found.
No items found.
No items found.
No items found.
use-case-phising-resistant-mfa
qr-code-login
pharmaceutical
healthcare
No items found.
No items found.
No items found.
Related posts

Time-Based One-Time Password (TOTP): The Complete Guide to Secure Authentication
Time-Based One-Time Password (TOTP) generates temporary authentication codes that expire within 30-60 seconds. Organizations use TOTP to secure access without relying on vulnerable SMS-based verification methods. This guide explains technical implementation, security advantages, and deployment strategies for enterprise environments.

Rahul Mathew
Last Updated:
January 23, 2026

Mobile Authentication Explained: Methods, Benefits, and Secure Login Best Practices
Mobile authentication uses smartphones as primary verification devices, replacing traditional password-based login systems. Organizations deploy biometrics, passkeys, push notifications, and device-bound credentials for secure access. This blog explains how mobile authentication works, compares security methods, and provides implementation strategies. Learn the best practices, use case recommendations, and security considerations for deploying mobile-first authentication across enterprise environments.

Rahul Mathew
Last Updated:
January 23, 2026
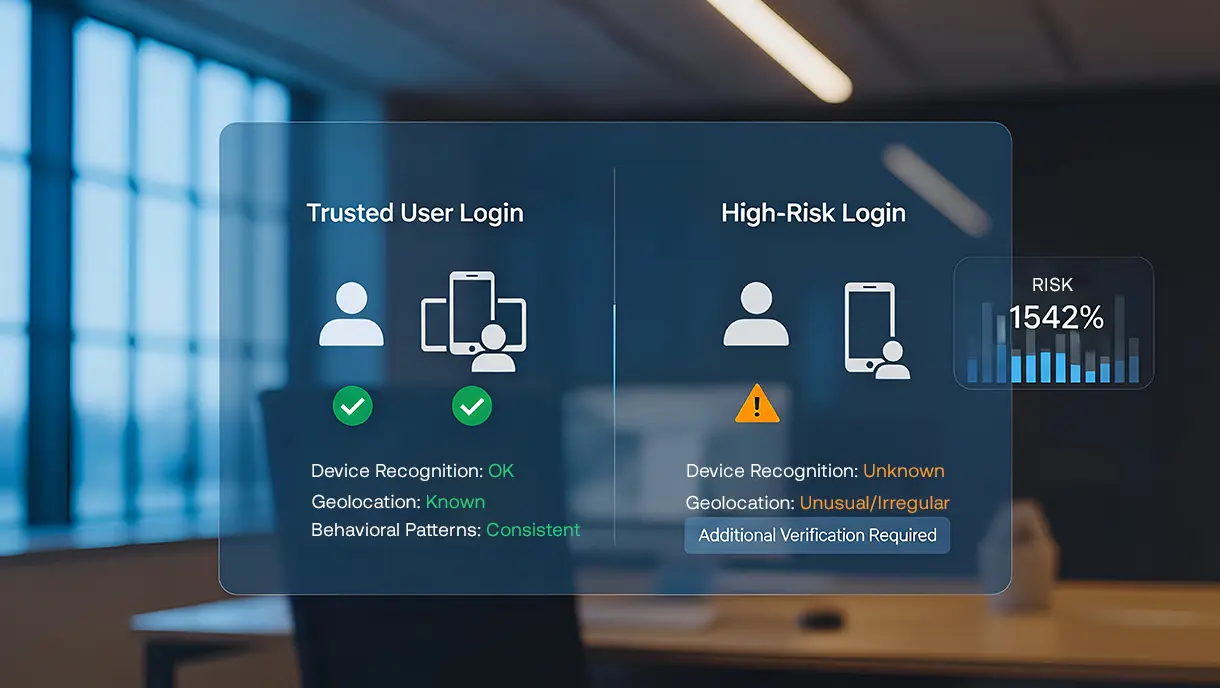
What Is Risk-Based Authentication? Benefits, Use Cases & How It Works
Risk-based authentication evaluates threat indicators and user behavior patterns before enforcing authentication requirements. Traditional static authentication applies the same verification regardless of the actual risk levels. This guide explains how risk-based systems calculate scores, analyze signals, and make dynamic decisions. Learn implementation strategies, regulatory compliance requirements, and best practices for deploying intelligent, risk-aware authentication.

Rahul Mathew
Last Updated:
January 23, 2026

The Future of Passwords: What Comes Next in Digital Authentication?
Passwords have protected digital accounts for decades, but cannot effectively defend against modern cyber threats. Organizations increasingly adopt passwordless authentication using passkeys, biometrics, and device-based credentials. This guide explores why passwords are becoming obsolete and what technologies replace them. You'll discover authentication trends, implementation challenges, and predictions for how digital identity will evolve.

Rahul Mathew
Last Updated:
January 29, 2026

How to Eliminate Passwords with Passwordless Authentication
Passwords create security vulnerabilities and operational burdens that modern organizations can no longer afford. Passwordless authentication eliminates these risks through biometrics, cryptographic keys, and device-based verification. This blog explores why eliminating passwords matters and how to implement effective alternatives. Learn passwordless authentication methods, implementation strategies, and best practices for transitioning your enterprise to passwordless security.

Rahul Mathew
Last Updated:
January 23, 2026

Zero-Trust Implementation Guide: Steps, Policies, & Best Practices
Zero-Trust Implementation transforms traditional security by continuously verifying every access request. Organizations adopt this model to protect against modern threats like credential theft and lateral movement. This guide provides practical steps, technical architecture insights, and real-world use cases. Enterprise security teams gain actionable frameworks for deploying Zero-Trust across hybrid environments.

Rahul Mathew
Last Updated:
January 23, 2026
Making every day-in-the-life of frontline workers frictionless & secure!
Get the latest updates! Subscribe now!
Thank you! Your submission has been received!
Oops! Something went wrong while submitting the form.


