
About
Garima Bharti Mehta is a B2B marketer with experience in enterprise and security technology. She works on positioning, content strategy, and narrative-building that helps technical products connect with real buyers.
Usually writes about
RFID Badge Login
QR Code Login
Palm Authentication
NFC Authentication
Face Authentication
Continuous Authentication
Contact Center
Use Case - Presence Detection
Use Case - Shared Device Access
Use Case - Phising Resistant MFA
Use Case - Shared Login
Use Case - Passwordless SSPR
Use Case - Login to SSO
Pharmaceutical
Healthcare
Retail
Manufactoring
No items found.
No items found.
No items found.
No items found.
No items found.
No items found.
No items found.
No items found.
No items found.
No items found.
No items found.
No items found.
No items found.
No items found.
No items found.
No items found.
No items found.
No items found.
No items found.
No items found.
No items found.
No items found.
No items found.
No items found.
No items found.
No items found.
No items found.
No items found.
No items found.
No items found.
No items found.
No items found.
No items found.
No items found.
No items found.
No items found.
No items found.
No items found.
No items found.
No items found.
No items found.
use-case-phising-resistant-mfa
use-case-presence-detection
continuous-authentication
contact-center
rfid-badge-login
No items found.
nfc-authentication
No items found.
No items found.
No items found.
No items found.
No items found.
pharmaceutical
healthcare
No items found.
No items found.
No items found.
No items found.
No items found.
No items found.
No items found.
No items found.
use-case-shared-device-access
use-case-shared-login
retail
pharmaceutical
contact-center
use-case-presence-detection
continuous-authentication
No items found.
No items found.
No items found.
use-case-shared-device-access
No items found.
No items found.
No items found.
No items found.
No items found.
healthcare
No items found.
No items found.
No items found.
No items found.
No items found.
No items found.
contact-center
contact-center
healthcare
pharmaceutical
retail
use-case-login-to-sso
Related posts
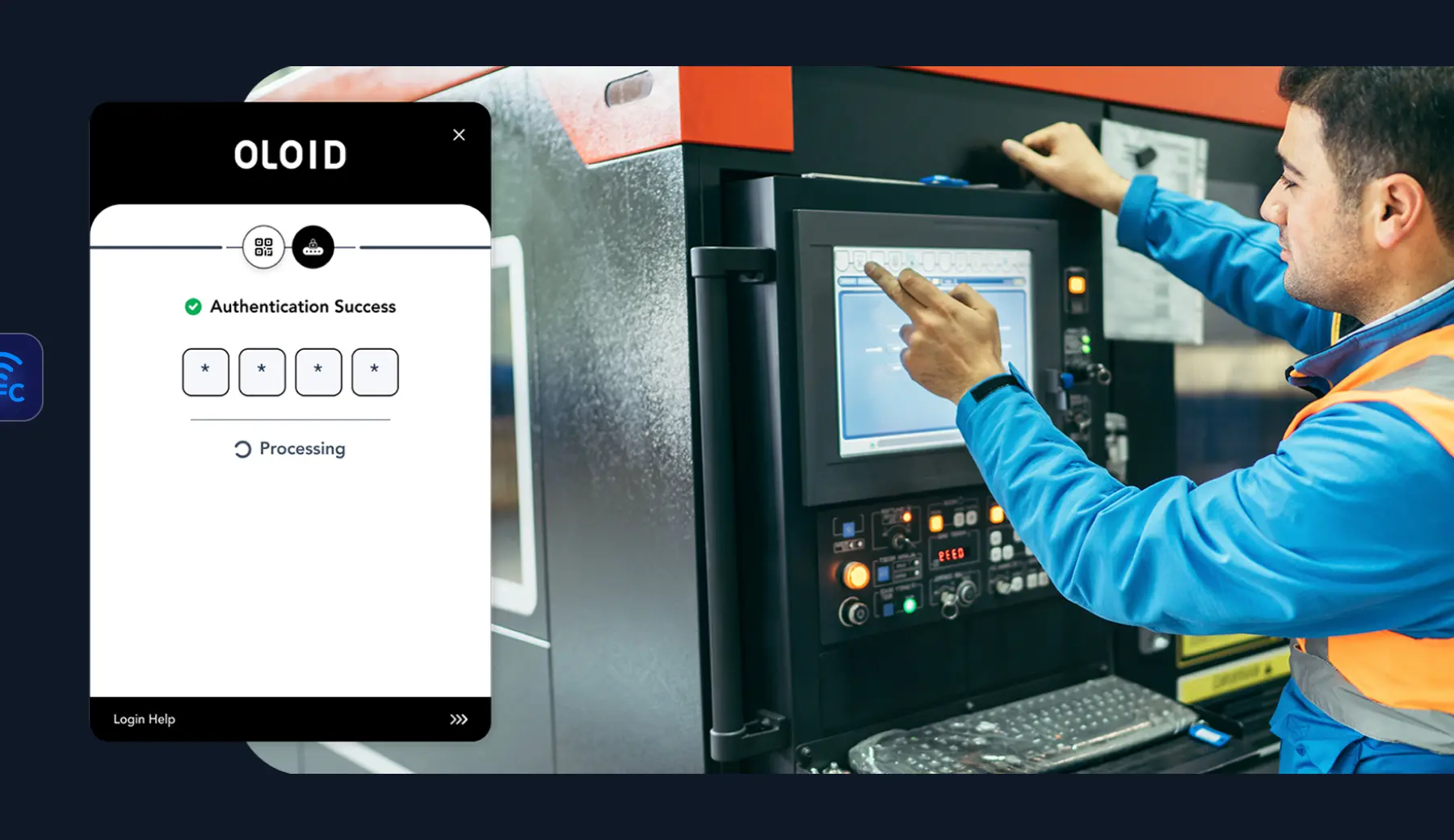
Securing Shared Devices Without Shared Passwords
Shared devices are vital in frontline work, but shared passwords and legacy MFA can’t meet the demands of shift-based, high-turnover environments. Modern security needs contactless, passwordless solutions that scale, ensuring secure access, individual accountability, and fast ROI.

Garima Bharti Mehta
Last Updated:
January 28, 2026

What Is Passwordless MFA? A Complete Guide to Secure and Frictionless Authentication
Passwordless MFA eliminates traditional passwords while maintaining multi-factor security through biometrics, security keys, and device-based authentication. This comprehensive guide explores what passwordless MFA is, its business benefits, implementation strategies, and best practices for overcoming common challenges. Learn how leading organizations are adopting passwordless multi-factor authentication to strengthen security, improve user experience, reduce IT costs, and meet compliance requirements.

Garima Bharti Mehta
Last Updated:
November 24, 2025

What Is Single Sign-On (SSO) and How Does It Work?
Single Sign-On (SSO) transforms how organizations manage user authentication across multiple applications and services. This comprehensive guide explores what SSO is, how it works, and why it matters for modern enterprises. Learn about different SSO types, implementation protocols, and the key advantages of adopting SSO solutions. The guide also covers practical use cases, step-by-step implementation processes, and expert advice on choosing the right SSO provider.

Garima Bharti Mehta
Last Updated:
December 18, 2025

Why Artificial Intelligence in Cybersecurity Is Essential for Modern Enterprises
Is your enterprise prepared for AI-powered cyberattacks? This complete guide examines how artificial intelligence strengthens cybersecurity defenses across every digital touchpoint. Learn how machine learning detects threats in milliseconds, how AI adapts to evolving attack patterns, and why automation reduces human error.

Garima Bharti Mehta
Last Updated:
January 8, 2026

Facial Authentication Explained: How It’s Transforming Digital Security
Facial authentication is transforming digital security by replacing passwords with secure biometric verification using AI-powered algorithms. This guide explains how facial authentication works, from detection to verification. Explores its benefits, including enhanced security, contactless convenience, and operational efficiency.

Garima Bharti Mehta
Last Updated:
November 15, 2025

What Is Biometric Authentication And How Does It Work?
Biometric authentication has transformed how organizations verify identity and secure access. This technology uses unique physical or behavioral traits like fingerprints, facial features, or voice patterns to replace vulnerable password-based systems. This guide covers the fundamentals of biometric authentication, including how the technology works and the various types available. You'll find practical implementation strategies, real-world industry applications, and key benefits for enterprises.

Garima Bharti Mehta
Last Updated:
February 6, 2026
Making every day-in-the-life of frontline workers frictionless & secure!
Get the latest updates! Subscribe now!
Thank you! Your submission has been received!
Oops! Something went wrong while submitting the form.


