OLOID Workflows at ISC West: Automate Security & PACS Value
At the recent ISC West event in Las Vegas, OLOID unveiled its newest product, OLOID Workflows. The product is designed to help organizations automate physical security and business operations using no-code/low-code workflows, allowing them to extract more value from their existing Physical Access Control Systems (PACS) and other systems.

At the recent ISC West event in Las Vegas, OLOID unveiled its newest product, OLOID Workflows. The product is designed to help organizations automate physical security and business operations using no-code/low-code workflows, allowing them to extract more value from their existing Physical Access Control Systems (PACS) and other systems.
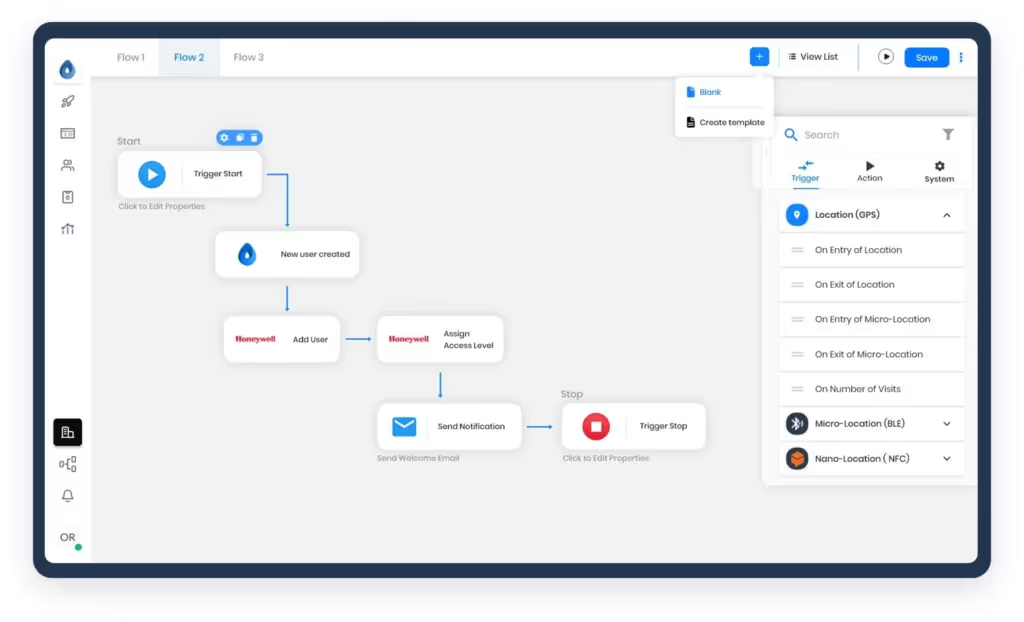
OLOID Workflows is equipped with a visual drag-and-drop rule engine, and it also offers no/low-code scripting for organizations with specific needs. It provides businesses with an extensive library of pre-built templates to automate their HR, IT, and security operations or create custom rules with minimal coding. The pre-built templates can be customized to suit specific requirements.
Madhu Madhusudhanan, Co-founder & CTO of OLOID, emphasized the versatility of OLOID Workflows, stating that it provides boundless flexibility to organizations with its extensive range of cyber and physical integration capabilities. It automatically connects and transfers identity and attribute data between access events, organizational operations, and other systems without disrupting any APIs.
Here's what OLOID Workflows offers:
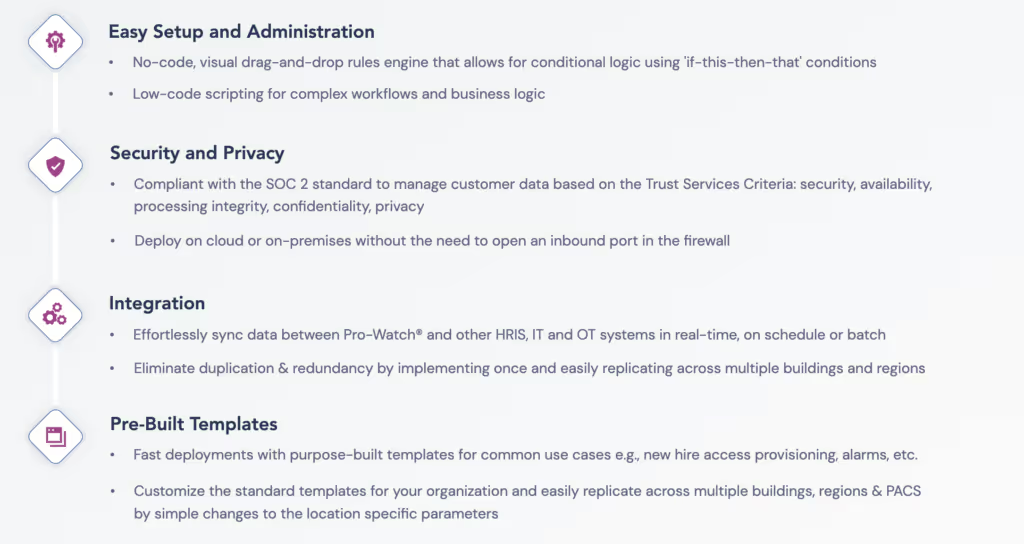
OLOID Workflows is an important addition to OLOID's product line, as it plays a crucial role in the company's strategy to upgrade physical security and access for modern workplaces while not disrupting existing identity and access infrastructure. It smoothly integrates with current PACS infrastructure, whether on-cloud or on-premises, to enable effortless scaling of business operations. By ensuring real-time data synchronization and eliminating duplicity and redundancy, OLOID Workflows unifies data architecture to provide a comprehensive solution for businesses, particularly enterprises.

Mohit Garg, Co-founder, and CEO of OLOID, explained that OLOID Workflows was created to assist organizations in maximizing the value of their existing systems by automating their everyday tasks and operations beyond just physical access, security, and identity management. He added that while OLOID M-Tag modernizes access control systems by enabling mobile access, OLOID Workflows enhances the versatility, dynamism, and administrative capabilities of their PACS while also ensuring compliance with security and privacy regulations.
The OLOID team demonstrated OLOID Workflows at the ISC West event, receiving positive reviews from attendees. The event is an annual gathering organized by the Security Industry Association (SIA), a leading trade association for global security solution providers and innovators.
Ayhan Olca, Head of Devices at Invia, spoke with the OLOID team and praised their products and solutions. He said, "OLOID has filled a significant gap in the industry that has not been addressed by anyone else. The direction our customers want to take is also aligned with OLOID's vision of leveraging existing hardware and infrastructure."
With its ease of use, versatility, and ability to integrate with existing PACS infrastructure, OLOID Workflows has the potential to automate physical security and business operations for organizations, enabling them to get more out of their existing systems. To learn more about OLOID Workflows or to book a demo, click here.



Get the latest updates! Subscribe now!




