Passwordless MFA for Frontline Teams
No mobile phones. No passwords. Just secure, traceable logins at every shift. Fast, frictionless & phishing-resistant MFA for shared devices and shift-based frontline teams.





Secure Frictionless Access
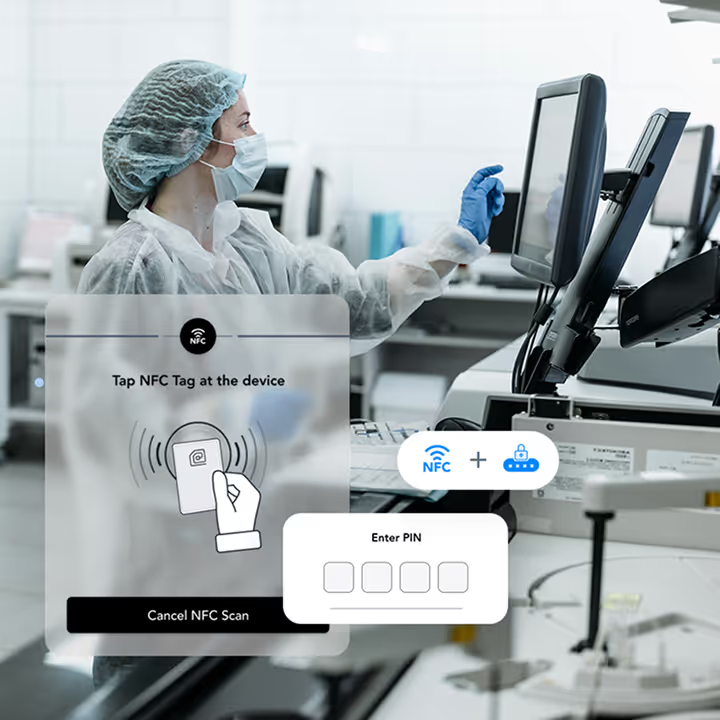
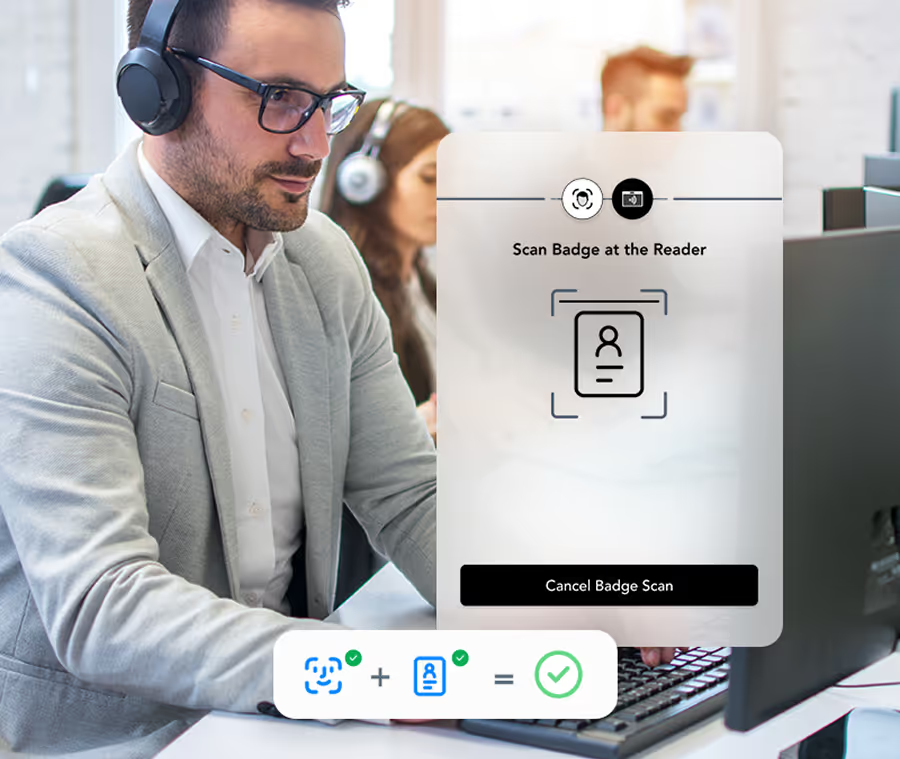
Passwordless Login
Employees log in with a badge or face. No devices to carry, no passwords to forget
Seamless SSO Integration
Easily connects to Okta, Azure AD, and your existing SSO apps. No changes to your current systems or workflows
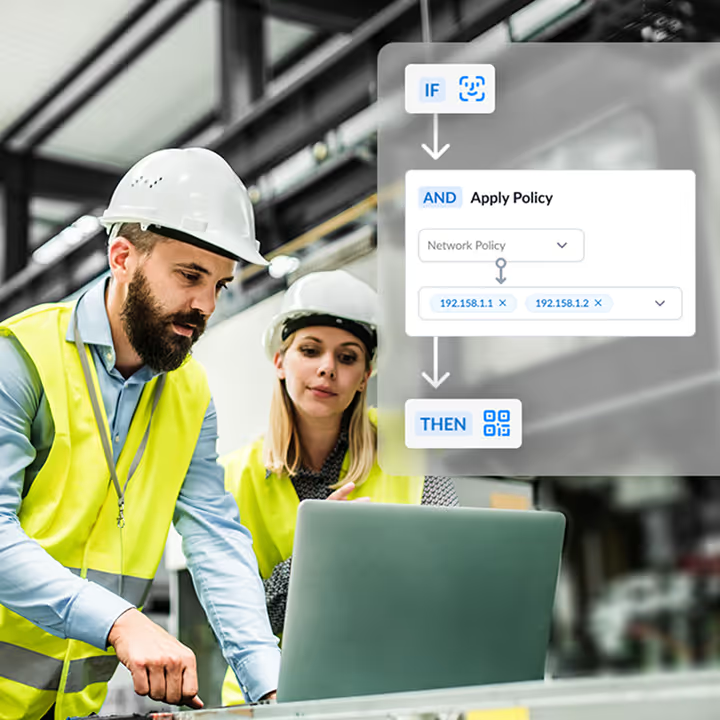
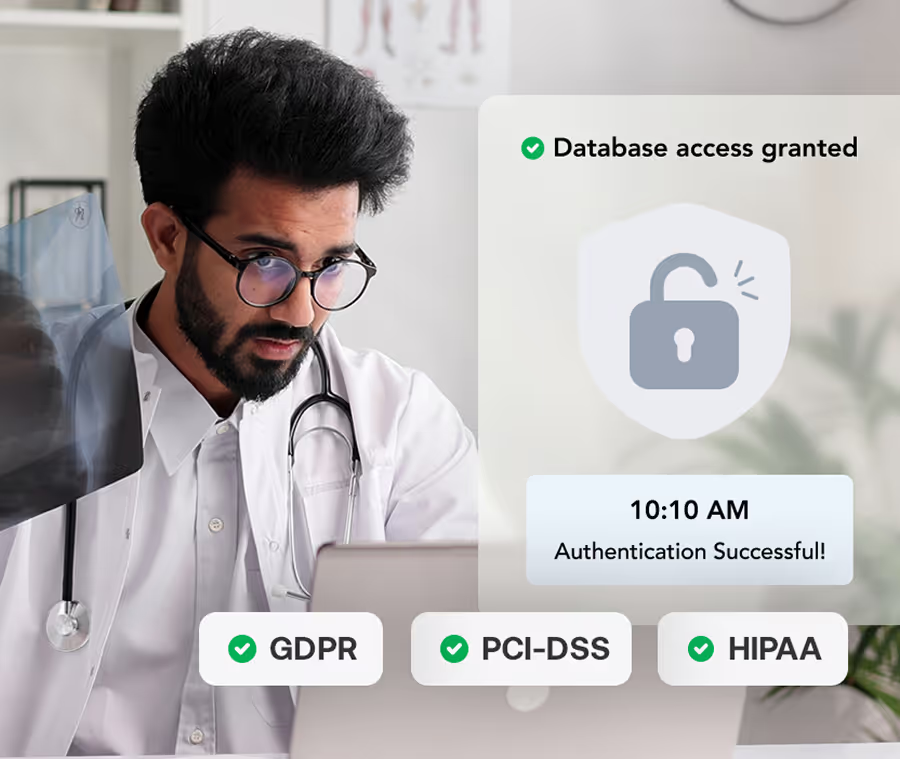
Smart Access Control
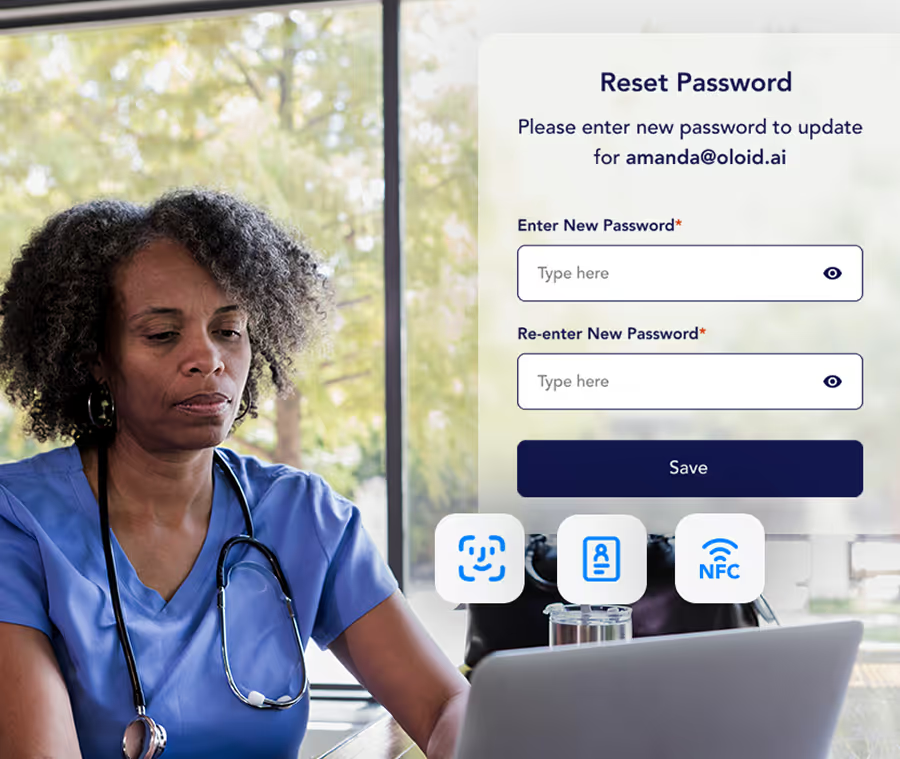
Set access rules by role, device, or location. Users reset passwords on their own, without IT help
Flexible, Secure Access Anywhere
Enable passwordless login and MFA on shared devices to keep every shift fast and secure.


Built to Fit Your Environment
See What Our Customers Have To Say

Peter Hunt
VP Security & Resiliency at Flex
-Logo.wine.avif)
Our customers demand the highest standard of security at our workplace. We are also committed to providing a safe environment at our workplace. OLOID is helping us achieve both these objectives.

Robert Fowler
Global Director of IT @ Tyson Foods

We recognized the tech challenges our frontline workers faced. Partnering with OLOID provided a user-friendly, passwordless solution. Through the OLOID-Okta integration, team members can swiftly access apps, view payroll, change benefits, and access job instructions on tablets. This enhancement streamlines their tasks, improving their work experience, and allowing them to focus more on delivering quality and efficiency in their roles.

Crystal Wydler
Sr. Human Resource Director @ White Horse Village

White Horse Village has loved OLOID's Time Clock product from the moment we started using it. Our hourly staff have found it fast and seamless, with no issues on our end. The only hiccup we faced was due to an ADP outage, but we were thrilled with how promptly OLOID retrieved all the punches during that period. The reliability and efficiency of OLOID’s product have significantly enhanced our time-tracking processes. We absolutely love OLOID’s Time Clock and highly recommend it to any organization seeking a dependable time management solution.

Melanie Briggs
FPC Payroll Administrator @ Chesapeake Health Care

At Chesapeake Health Care, efficient time tracking across our multiple locations is crucial. We needed an integrated solution for our workforce, and OLOID’s Time Clock with ADP integration delivered perfectly. The implementation was straightforward, and we haven’t encountered any issues since we started using it. OLOID’s product has streamlined our time management processes, making it easier to manage our workforce effectively. We highly recommend OLOID Time Clock for its reliability and integration capabilities.

Gregg Adkin
Managing Director @ Dell

OLOID's innovation has the potential to transform the hardware-centric access control industry into a software-as-a-service model with minimal capital expenditure.

Aaron Polinsky
Managing Partner @ Cammebys

OLOID has the potential to simplify an extremely complex task of access management in our buildings. OLOID’s mobile access retrofit solution and their PACS integrations make it well suited for our wide range of properties with diverse access control systems.

Tal Bernier
Plant Manager @ Tracco

The transition from ADP swipe cards to the OLOID facial recognition program has been a seamless process. With swipe cards, we had issues with lost cards, shared cards, and employees forgetting to clock in and out altogether. With OLOID, all our employees have to do is show their faces and easily clock in and out without any problems.